For decades, businesses have relied on traditional networking solutions to manage their digital infrastructure. However, as organizations increasingly migrate to the cloud, the limitations of these legacy systems have become more apparent. Traditional networking models—based on physical hardware, on-premises data centers, and manual configurations—are struggling to keep up with the demands of modern business.
Challenges in Traditional Networking
Before the cloud era, businesses faced several significant challenges with traditional network infrastructures:
- Economic Inefficiencies: Organizations had to invest heavily in physical hardware, data centers, and ongoing maintenance, often resulting in underutilized resources.
- Operational Complexity: Managing complex networks requires specialized teams, manual configurations, and significant downtime during expansions.
- Scalability Constraints: Expanding infrastructure was a slow and costly process, often requiring physical hardware procurement.
As organizations transitioned to cloud computing, these traditional approaches became increasingly inadequate.
Virtualized Private Networks
Virtualized private networks (VPNs) address many of the challenges of traditional networking by moving network infrastructure into the cloud. A virtualized network exists entirely in software, allowing for the flexibility and scalability that traditional hardware networks couldn't provide.
This evolution in networking capabilities leads directly to AWS Virtual Private Cloud (VPC), which gives businesses the ability to build and manage their private network in the AWS Cloud.
What is an AWS Virtual Private Cloud (VPC)?
An AWS Virtual Private Cloud (VPC) is a virtualized private network in the AWS cloud. Think of it as a private network that behaves similarly to an on-premises data center but with the scalability and flexibility of the cloud. Unlike traditional networks, AWS VPC allows you to create complex, isolated network architectures with full control over traffic routing and security.
In simple terms, AWS VPC allows you to build your network in the cloud, where you can define IP ranges, set up subnets, and apply security measures like firewalls and access control, all without the need for physical hardware. It is the foundation for any AWS-based network, enabling businesses to scale, secure, and customize their networks as needed.
Why is Network Isolation Essential?
Network isolation is critical for securing cloud environments. With AWS VPC, you can isolate your cloud infrastructure from external traffic, ensuring that only authorized users and systems have access to sensitive resources. This is achieved through features like security groups and network access control lists (NACLs), which allow you to enforce strict access controls and protect data. Proper isolation is essential to safeguard against unauthorized access and maintain compliance with industry security standards.
Why AWS VPC Matters?
After understanding what AWS VPC is and why network isolation is crucial, it’s important to recognize why AWS VPC stands out as an essential service in modern cloud infrastructure. VPC provides the ability to build secure, customizable, and scalable networks tailored to specific organizational needs.
- Complete Control: With VPC, you have full control over your network architecture, allowing you to define IP ranges, subnets, route tables, and more, ensuring that the network works exactly as needed.
- Enhanced Security: By utilizing security groups, NACLs, and traffic routing policies, VPC helps protect your data and applications from unauthorized access, making it an indispensable tool for security-conscious businesses.
- Scalability: As your business grows, AWS VPC scales with ease. You can add more resources without the limitations of traditional networking setups, ensuring that your network can grow alongside your demands.
- Seamless Hybrid Connectivity: AWS VPC also supports hybrid environments, enabling secure connections between on-premises infrastructure and the cloud through features like VPN and AWS Direct Connect.
By leveraging AWS VPC, businesses can achieve a network architecture that is both flexible and secure, ensuring that cloud resources are aligned with business goals and operational requirements.
Traditional Networking vs AWS VPC
| Aspect | Traditional Networking | AWS VPC |
| Infrastructure | Physical hardware | Software-defined |
| Scalability | Slow, hardware-dependent | Instantaneous, elastic |
| Cost | High capital expenditure | Pay-as-you-go |
| Network Isolation | Complex, manual | Built-in, granular |
| Security Configuration | Time-consuming | Automated, configurable |
| Global Reach | Expensive | Instant multi-region |
Key Components of AWS VPC
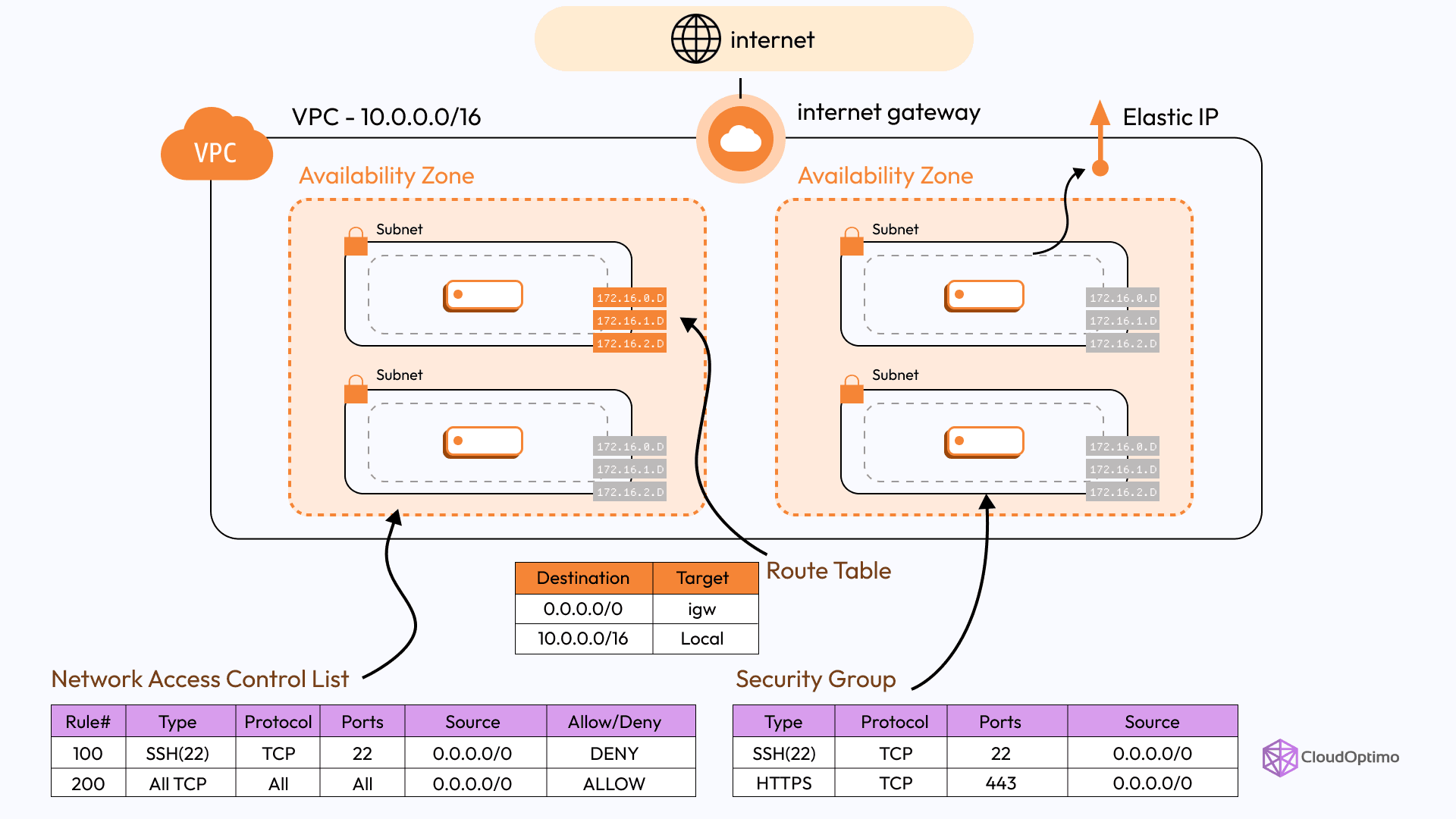
Source - AWS
The AWS VPC architecture consists of several key components that provide both flexibility and control. Let’s break down each component in detail:
Subnets
Subnets divide your VPC into smaller network segments. Each subnet resides in a specific Availability Zone (AZ) and can either be public or private.
- Public Subnet: Accessible from the internet (e.g., for web servers).
- Private Subnet: Not directly accessible from the internet (e.g., for databases, application servers).
- Best Practice: Use a combination of public and private subnets for high availability and security.
Route Tables
A route table controls the traffic flow between your subnets, VPC, and external networks (e.g., the Internet). It contains rules that specify where network traffic is directed.
- Main Route Table: AWS automatically creates a default route table for your VPC.
- Custom Route Tables: You can create multiple custom route tables for fine-grained control over traffic between subnets.
Internet Gateway (IGW) and NAT Gateway
- Internet Gateway (IGW): A scalable gateway to connect your VPC to the internet. Essential for resources in a public subnet that requires internet access.
- NAT Gateway: Provides outbound internet access for resources in private subnets without exposing them to the internet.
Network Access Control Lists (NACLs)
NACLs are stateless security layers that control traffic entering and exiting a subnet. Unlike Security Groups, NACLs operate at the subnet level, and traffic must match the inbound and outbound rules.
- Stateless: NACLs treat inbound and outbound traffic separately.
- Use Case: Ideal for controlling traffic between subnets or for additional layers of security.
Security Groups
Security Groups are stateful firewalls applied to individual instances (e.g., EC2 instances) within your VPC. They define rules for inbound and outbound traffic.
- Stateful: If an inbound rule allows traffic, the corresponding outbound traffic is automatically allowed.
- Best Practice: Security Groups should be used to control instance-level access and isolate different services within your VPC.
Elastic IP (EIP)
An Elastic IP is a static IP address associated with your AWS account. You can associate it with an EC2 instance or a NAT Gateway for consistent IP addressing.
Best Use Case: Essential for failover scenarios or applications requiring fixed IP addresses.
VPN Gateway
A VPN Gateway enables you to create an encrypted VPN connection between your on-premises network and your AWS VPC, allowing secure communication.
Types of VPN Connections:
- Site-to-Site VPN: For securely connecting an on-premises network to your VPC.
- Client VPN: For enabling secure connections from remote devices to your VPC.
Enhanced Routing Mechanisms Explained
Routing plays a pivotal role in the movement of data across your network, particularly when dealing with multi-tiered architectures or complex network setups. Let’s break down the key routing mechanisms:
Route Tables:
These define the paths that network traffic will take. Every subnet must be associated with a route table to determine how packets are directed.
- Local Routes: By default, VPCs are configured to allow communication within themselves. Local routes enable this inter-subnet communication across your VPC.
- Internet Gateway Routes: Public subnets can route traffic to the internet through the internet gateway (IGW). This enables the outbound communication needed for applications or services that interact with external systems.
- NAT Gateway Routes: For private subnets that require secure internet access, NAT gateways route traffic to the internet while maintaining the security of the internal network.
Complex Configurations:
- Multi-Region Traffic: In more complex architectures, such as multi-region networks, Transit Gateways are used to facilitate routing between VPCs or between cloud environments and on-premises networks. This is essential for businesses that need high availability and low-latency communication across geographical regions.
- Custom Route Policies: You may also need to implement custom routing policies to manage specific conditions, such as failover scenarios or compliance-driven routing for sensitive workloads.
While routing defines how traffic flows through the network, ensuring that traffic is secure is equally crucial. Let's now explore AWS VPC's Advanced Network Security Mechanisms—security features that complement routing by protecting data and controlling access at various levels.
Advanced Network Security Mechanisms
AWS VPC offers advanced security features to protect data and resources, ensuring network security at both the instance and subnet levels. Let’s explore the core security mechanisms offered by AWS VPC:
Network Access Control Lists (NACLs)
NACLs act as stateless firewalls that protect entire subnets. Unlike security groups, which operate at the instance level, NACLs function at the subnet boundary, giving you an extra layer of control. NACLs support both allow and deny rules, providing explicit control over the types of traffic that can enter or leave your subnet. Here’s how they work:
- Stateless Packet Filtering: NACLs do not track the state of connections, meaning every packet is evaluated based on its merit.
- Processed in Numeric Order: Rules are evaluated in the order they are listed.
- Applied to Entire Subnets: Unlike security groups, which are tied to individual instances, NACLs apply to all instances within the subnet.
- Default Behavior: The default NACL allows all inbound and outbound traffic unless specified otherwise
Security Groups: Instance-Level Protection
While NACLs protect entire subnets, security groups offer a more granular, stateful firewall approach to network protection, specifically designed for EC2 instances. Each EC2 instance within a VPC can have one or more security groups associated with it, providing more detailed control over traffic flow.
Key features of security groups:
- Stateful Protection: Security groups automatically track the state of network connections. This means that if you allow inbound traffic, the corresponding outbound traffic is automatically allowed.
- Allow Rules Only: Unlike NACLs, security groups only support allow rules. Any traffic not explicitly allowed is automatically denied.
- Reference Other Security Groups: You can specify other security groups as sources, allowing easy grouping and organization of rules.
Security groups provide instance-level isolation and protection, ensuring that only authorized traffic can reach your EC2 instances.
Network Address Translation (NAT)
While both NACLs and security groups protect your network resources, NAT gateways and instances play a critical role in providing internet access for resources within private subnets. NAT enables private instances to communicate with external resources without exposing their private IP addresses.
- NAT Gateways: These are managed services that enable automatic failover and scalability, ensuring seamless internet access for private subnet resources.
- NAT Instances: These are EC2 instances configured to perform NAT, but require more management and scaling.
NAT is essential for maintaining the security of private subnets, ensuring that internal resources can access the internet for updates, patches, or external communication, while still keeping their IPs private.
Advanced Configuration Guidance
CIDR Block Planning:
CIDR (Classless Inter-Domain Routing) is a method used to allocate and specify IP addresses and routing prefixes. It replaces the older class-based system (Class A, B, C) with a more flexible and efficient way of dividing IP address space. In CIDR notation, an IP address is followed by a slash and a number (e.g., 192.168.1.0/24), where the number indicates how many bits are used for the network prefix.
- The network prefix represents the portion of the IP address that identifies the network, while the remaining bits are used for the individual hosts within that network.
- For example, a /24 subnet represents a network with 256 IP addresses, where the first 24 bits are the network portion, and the remaining 8 bits are available for hosts.
- CIDR allows for more precise and efficient IP address allocation, which is especially important for scaling cloud networks like AWS VPC.
Effective CIDR block planning is essential for a well-organized and scalable VPC architecture. When designing your VPC, consider the following best practices to ensure that your network is both efficient and capable of accommodating future growth:
- Calculate IP Needs: Estimate both your current and future resource requirements to determine the appropriate CIDR block size. It’s important to ensure that your chosen block can accommodate future growth without needing to resize.
- Avoid IP Range Overlaps: Carefully select CIDR blocks that don’t overlap with existing on-premises IP ranges, ensuring smooth connectivity between your AWS infrastructure and on-premises systems.
Best Practices for Multi-Tier Architectures:
In multi-tier architectures, the proper segmentation of resources is key to performance, security, and scalability. Here’s how to approach it:
- Separate Subnets for Each Tier:
- Web Tier (Public): This tier hosts your web-facing applications and needs to be publicly accessible.
- App Tier (Private): This tier holds the business logic layer and should be isolated from external access.
- DB Tier (Private): Databases should be placed in a private subnet with restricted access, ensuring sensitive data remains protected.
Security Configurations: A robust security framework is essential for safeguarding your resources. Key considerations include:
- Security Groups: Apply the principle of least privilege to limit access to only what is necessary. For instance, allow TCP 80/443 (HTTP/HTTPS) traffic from 0.0.0.0/0 for web servers to allow public access, but restrict all other outbound traffic.
- IAM Roles: Attach IAM roles to control access to your resources, simplifying security management by reducing the need for individual key management.
- Separate Subnets for Each Tier:
Following these best practices, you can build a secure, well-organized, and scalable AWS VPC architecture that suits your needs.
Performance and Design Considerations
When designing AWS VPC architectures, organizations must balance various aspects of network performance, security, scalability, and cost. By making the right design choices, businesses can optimize performance while managing potential trade-offs. Here's an overview of the key factors to consider when building a secure and efficient network infrastructure on AWS.
Design Strategies:
Subnet Segmentation:
Distribute workloads across subnets based on resource intensity. This approach enables more efficient resource management, better isolation, and improved performance. For example, placing resource-heavy services in private subnets can help reduce the impact on other services.It is also important to segment subnets by environment, such as development, testing, and production, to keep them organized and isolated. Here's an example setup:
- 10.0.0.0/24 – Development Environment
- 10.0.1.0/24 – Testing Environment
- 10.0.2.0/24 – Production Environment
- Load Balancers:
Implementing Application Load Balancers (ALB) or Network Load Balancers (NLB) ensures efficient traffic distribution, preventing overload on any individual instance or subnet. Load balancers automatically scale to accommodate changes in traffic volume, ensuring high availability and fault tolerance.
When designing VPC architectures, organizations must consider:
Network Performance Optimization
To optimize network performance, it's crucial to consider:
- Selecting appropriate CIDR block sizes.
- Strategically placing resources across availability zones.
- Minimizing network hops and latency.
- Balancing subnet segmentation with performance requirements.
Configuration Trade-offs
Some key trade-offs when designing VPCs include:
- Wider CIDR blocks provide more IP flexibility but can complicate routing.
- Strict subnet segmentation enhances security but may increase complexity.
- Multi-tier architectures offer better isolation but require careful design.
Performance Metrics and Optimization Strategies
To ensure your network consistently meets performance benchmarks, it's crucial to monitor key metrics and apply optimization strategies. Here's how to quantify and enhance VPC performance.
Quantitative Data:
- Average Latency: Subnets within the same AZ typically experience latency < 1 ms.
- Cross-Region Traffic: Can have latencies of 20-50 ms, depending on the regions involved
Optimization Strategies:
- AZ-Aware Design: Deploy applications across multiple availability zones (AZs) for redundancy and low-latency access.
- Enable Enhanced Networking: For high-throughput workloads, utilize Elastic Network Adapters (ENA).
- Traffic Inspection: Use VPC Traffic Mirroring to analyze and optimize packet flow.
VPC Peering and Connectivity Options
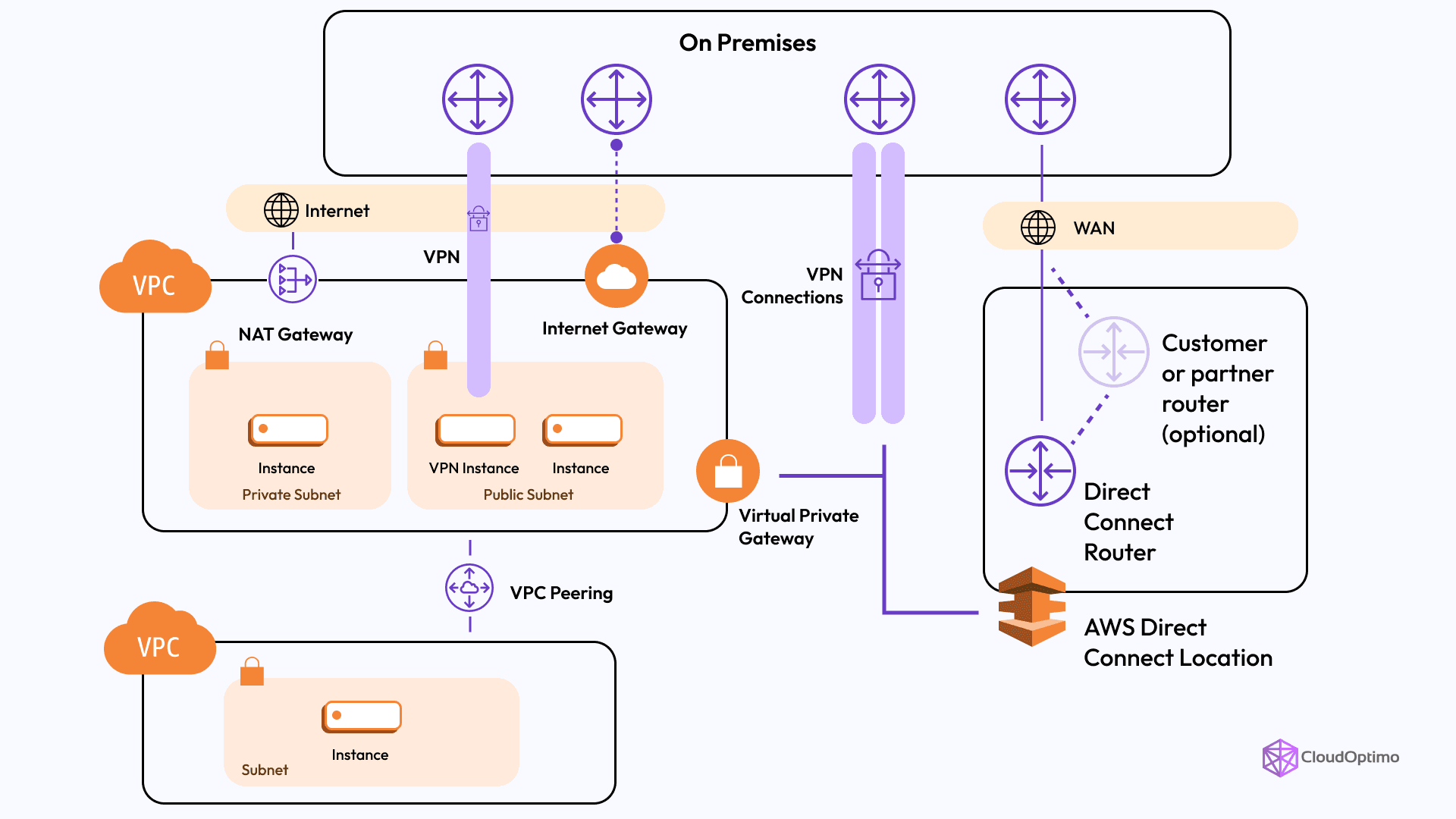
Source - AWS
Once you have a clear understanding of VPC design and performance considerations, it's essential to explore how to connect these VPCs to ensure smooth communication and secure access to AWS services
VPC Peering
VPC peering enables private networking between two VPCs, allowing resources to communicate as if they were in the same network. This supports:
- Cross-region communication: Ensures seamless service discovery for distributed workloads, including containerized applications and traditional services.
- Simplified multi-account architectures: Ideal for managing resources like databases, microservices, and application environments across different VPCs.
- Reduced network latency: Enhances performance for all inter-VPC communications, from EC2 instances to container clusters.
Note: Peering connections are one-to-one, meaning only two VPCs can be connected at a time.
AWS Direct Connect
AWS Direct Connect provides a private, direct link between on-premises infrastructure and AWS networks for enterprises requiring dedicated, low-latency connections. Benefits include:
- Consistent network performance: Beneficial for container orchestration platforms (like Kubernetes) and applications requiring low-latency access to on-premises data.
- Enhanced security: Supports secure data transfer for databases, legacy systems, and containerized workloads.
- Reduced bandwidth costs: Optimizes costs for high-volume data transfers between on-premises environments and various AWS services.
Site-to-Site VPN
VPN connections encrypt traffic between on-premises networks and AWS VPCs, offering a cost-effective solution for:
- Hybrid environments: Securely connect on-premises systems with cloud-based databases, applications, and microservices.
- Container communication: Ensures encrypted connections between on-premises Kubernetes clusters and cloud-hosted services.
Transit Gateway
Transit Gateway acts as a central hub for managing multiple VPCs and on-premises networks:
- Simplified routing: Efficiently routes traffic between VPCs hosting various services, including containerized applications, databases, and web servers.
- Scalability: Expands seamlessly to connect more VPCs and services as your cloud environment grows.
PrivateLink
AWS PrivateLink allows private, secure connectivity between VPCs and AWS services without traversing the public internet:
- Service integration: Securely connects your VPC to services like S3, EC2, Lambda, and API Gateway.
- Microservices support: Ideal for containerized applications accessing other internal services or third-party SaaS offerings.
Limitations and Trade-offs
While these connectivity options offer significant benefits, it's essential to evaluate the trade-offs involved:
- Latency vs. Security
Tightening security with multiple layers (e.g., VPNs, NACLs) often adds extra latency to network traffic. While these layers are crucial for protecting your resources, it's important to assess how they may impact your application’s performance. - Scalability vs. Cost
When scaling your VPC, ensure you choose the right CIDR block size. Over-allocating IP addresses might lead to wasted resources while under-allocating could create scalability issues. Striking a balance between these factors will help control costs while maintaining performance.
Understanding the trade-offs between latency, security, and scalability is essential—but these decisions also impact your costs significantly. Let's explore how optimizing your VPC configurations can help manage cloud expenses effectively.
Cost Optimization in AWS VPC
Optimizing VPC configurations is crucial to managing cloud costs effectively. Here’s a detailed look at cost considerations:
Cost Implications of Different Configurations
- CIDR Blocks and IP Addressing: Larger blocks (e.g., /16) may offer flexibility but come at a higher cost if underutilized.
- Subnets: Plan subnets based on traffic patterns to avoid overspending on NAT gateways or inter-zone traffic.
- Internet Gateway Usage: Limit public subnet access where possible to reduce data transfer costs.
| Service/Resource | Cost | Notes |
| CIDR Blocks (IP Addressing) | No direct charge for IP allocation in VPC | Charges are based on the number of IP addresses required. |
| NAT Gateway | $0.045 per hour | Plus $0.04 per GB of data processed. |
| Internet Gateway | No direct cost for the gateway itself | Data transfer out of AWS is charged at $0.09 per GB for the first 10 TB. |
| Data Transfer (within the same region) | Free | Data transfer between resources in the same region is free. |
| Data Transfer (cross-region) | $0.02 per GB | Charges apply for data transfer between different AWS regions. |
| VPC Peering | Free (within the same region) | Data transfer charges apply based on the region. |
| VPN Connection | $0.05 per hour + data transfer charges | Cost for VPN connections, in addition to data transfer charges. |
| Elastic IP Address | $0.005 per hour (if not associated with a running instance) | Charges apply when the Elastic IP is not in use. |
Note: The prices listed above are subject to change. For the most accurate and up-to-date pricing, please refer to the AWS Pricing Calculator.
Cost Management Strategies
- Monitor Data Transfer Costs: Use AWS Cost Explorer to identify unexpected charges.
- Leverage Reserved Instances: For long-running workloads in VPC, reserved instances can offer significant savings.
- Optimize Traffic Flow: Minimize inter-region data transfer and use VPC Peering instead of VPN for internal connections.
- Audit Unused Resources: Regularly check for unused NAT gateways, IP addresses, or unused subnets.
Best Practices for VPC Design
To fully harness the power of AWS VPC, businesses must consider key design practices that will maximize the flexibility, security, and scalability of their networks.
- Network Segmentation
- Implement multi-tier architectures
- Use separate subnets for different environment stages
- Follow the least privilege access principles
- IP Address Management
- Plan CIDR blocks strategically
- Allow room for future expansion
- Avoid hard-coded IP configurations
- Security Considerations
- Implement robust security group rules
- Use network ACLs as an additional security layer
- Regularly audit and update network configurations
Now that we've covered the best practices for designing a VPC, let's take a look at some practical use cases that demonstrate how these concepts come together in real-world environments.
Practical Use Cases for AWS VPC
- Small Startup Scenario
A small e-commerce startup might use AWS VPC to host a simple web application:
- Public Subnet: The web server and load balancer are placed here, accessible from the internet.
- Private Subnet: The database server is isolated in a private subnet to ensure security and reduce the attack surface.
- Security Groups and NACLs: These are configured to allow only necessary traffic (e.g., HTTP/HTTPS for the web server, and SQL traffic for the database server).
This setup allows the startup to scale its infrastructure easily, handling traffic spikes during promotional events without worrying about hardware management.
- Enterprise Scenario: Complex, Multi-Tier Network Design
For a large enterprise, AWS VPC can be leveraged to build a robust, multi-tier network infrastructure:
- Multiple VPCs: Different VPCs are used for development, staging, and production environments.
- VPC Peering: VPC peering is configured between different VPCs to ensure secure and seamless communication across environments.
- AWS Direct Connect: A dedicated connection is established between the enterprise’s on-premises data center and AWS, ensuring low-latency, high-throughput access to AWS resources.
Step-by-Step VPC Creation Guide
Let’s explore how to create and configure a VPC. Here’s a step-by-step guide to setting up a basic VPC with public and private subnets.
Step 1: Define the VPC’s CIDR Block
You will first create a VPC with a specific CIDR block using the aws ec2 create-vpc command. For example, we'll create a VPC with the CIDR block 10.0.0.0/16:
- Example: A common CIDR block is 10.0.0.0/16, which gives you over 65,000 IP addresses to work with.
| aws ec2 create-vpc --cidr-block 10.0.0.0/16 --query 'Vpc.VpcId' --output text |
This command creates the VPC and returns its VPC ID.
Step 2: Create Subnets
Next, we’ll create two subnets within this VPC: a public subnet and a private subnet. We assume you already have the VpcId from the previous step.
Create a public subnet in Availability Zone us-east-1a:
| aws ec2 create-subnet \ --vpc-id vpc-xxxxxxxx \ --cidr-block 10.0.0.0/24 \ --availability-zone us-east-1a \ --query 'Subnet.SubnetId' \ --output text |
Create a private subnet in Availability Zone us-east-1b:
| aws ec2 create-subnet \ --vpc-id vpc-xxxxxxxx \ --cidr-block 10.0.1.0/24 \ --availability-zone us-east-1b \ --query 'Subnet.SubnetId' \ --output text |
Step 3: Set Up Route Tables
Now, create route tables and associate them with the subnets.
Create a route table for the public subnet:
| aws ec2 create-route-table --vpc-id vpc-xxxxxxxx --query 'RouteTable.RouteTableId' --output text |
Create a route table for the private subnet:
| aws ec2 create-route-table --vpc-id vpc-xxxxxxxx --query 'RouteTable.RouteTableId' --output text |
Associate the public route table with the public subnet:
| aws ec2 associate-route-table \ --subnet-id subnet-xxxxxxxx \ --route-table-id rtb-xxxxxxxx |
Associate the private route table with the private subnet:
| aws ec2 associate-route-table \ --subnet-id subnet-xxxxxxxx \ --route-table-id rtb-xxxxxxxx |
Step 4: Attach an Internet Gateway
For public access, you’ll need to attach an Internet Gateway to the VPC. This allows the public subnet to communicate with the internet.
Create and attach the Internet Gateway:
| # Create an Internet Gateway aws ec2 create-internet-gateway --query 'InternetGateway.InternetGatewayId' --output text # Attach the Internet Gateway to your VPC aws ec2 attach-internet-gateway --vpc-id vpc-xxxxxxxx --internet-gateway-id igw-xxxxxxxx |
Step 5: Configure Security Groups and NACLs
Next, configure the security groups (SGs) to allow specific traffic.
Create a Security Group for the web server (public subnet):
| aws ec2 create-security-group \ --group-name web-sg \ --description "Web server security group" \ --vpc-id vpc-xxxxxxxx --query 'GroupId' --output text |
Add inbound rules to allow HTTP and HTTPS traffic:
| aws ec2 authorize-security-group-ingress \ --group-id sg-xxxxxxxx \ --protocol tcp --port 80 --cidr 0.0.0.0/0 aws ec2 authorize-security-group-ingress \ --group-id sg-xxxxxxxx \ --protocol tcp --port 443 --cidr 0.0.0.0/0 |
Create a Security Group for the database server (private subnet):
| aws ec2 create-security-group \ --group-name db-sg \ --description "Database security group" \ --vpc-id vpc-xxxxxxxx --query 'GroupId' --output text |
Add an inbound rule to only allow internal traffic:
| aws ec2 authorize-security-group-ingress \ --group-id sg-xxxxxxxx \ --protocol tcp --port 3306 --source-group sg-xxxxxxxx |
Create a Network ACL (NACL) for additional control over subnet traffic.
| # Create a Network ACL aws ec2 create-network-acl --vpc-id vpc-xxxxxxxx --query 'NetworkAcl.NetworkAclId' --output text # Associate the NACL with a subnet (example: public subnet) aws ec2 associate-network-acl --network-acl-id acl-xxxxxxxx --subnet-id subnet-xxxxxxxx |
Step 6: Set Up VPC Peering (Optional)
If you need to connect two VPCs, you can create a VPC peering connection. Assume you have another VPC (VPC 2) and want to connect it to your VPC (VPC 1).
Create a VPC Peering connection:
| aws ec2 create-vpc-peering-connection \ --vpc-id vpc-xxxxxxxx \ --peer-vpc-id vpc-yyyyyyyy \ --query 'VpcPeeringConnection.VpcPeeringConnectionId' \ --output text |
Accept the peering request (from the second VPC):
| aws ec2 accept-vpc-peering-connection --vpc-peering-connection-id pcx-xxxxxxxx |
CloudFormation Template Example:
Here’s an example CloudFormation template to create a simple VPC:
yaml
| Resources: MyVPC: Type: AWS::EC2::VPC Properties: CidrBlock: 10.0.0.0/16 EnableDnsSupport: true EnableDnsHostnames: true |
This script guides you through the creation of a basic VPC with public and private subnets, route tables, Internet Gateway, Security Groups, and (optionally) VPC Peering. Replace the placeholder values (e.g., vpc-xxxxxxxx, subnet-xxxxxxxx) with your actual AWS resource IDs.
This setup can be customized further depending on your requirements, such as adding more subnets, configuring additional security rules, or setting up a NAT Gateway for internet access in private subnets.
Troubleshooting Common VPC Challenges
- Connectivity Issues
- Verify route tables
- Check security group rules
- Confirm network ACL configurations
- Use VPC Flow Logs for diagnostics
- Performance Optimization
- Choose appropriate subnet sizes
- Distribute resources across availability zones
- Monitor network latency
- Implement efficient routing strategies
While basic troubleshooting can resolve most connectivity and performance issues, complex architectures often require deeper analysis.
Advanced Troubleshooting Techniques
Beyond basic checks, advanced troubleshooting involves:
- Flow Logs Analysis: Capture and analyze VPC Flow Logs to detect abnormal traffic patterns.
- Route Table Validation: Check for conflicting or overly complex route table configurations.
- Latency Testing: Use AWS CloudWatch metrics to compare expected vs. actual performance.
- Network ACL Debugging: Ensure rules are correctly ordered and troubleshoot potential blocking rules.
Example Scenario: If cross-subnet communication fails, verify that:
- NACLs permit traffic both ways.
- Security groups allow inbound/outbound traffic.
- Route tables correctly direct traffic between subnets
VPC Monitoring and Optimization
VPC offers several tools for monitoring and optimizing network performance, helping you ensure that your cloud resources are running at peak efficiency.
Amazon CloudWatch
Use Amazon CloudWatch to monitor your VPC and its resources. You can set up alarms to notify you of potential issues such as excessive network latency or high packet loss.
AWS Cost Explorer
Monitor the cost of your VPC components using AWS Cost Explorer. This tool can help identify areas where you might optimize costs, such as by using Reserved Instances or moving traffic to Spot Instances.
Emerging Trends in VPC Architecture
- Serverless Network Design
The increasing adoption of serverless computing is driving more dynamic, event-driven network architectures within VPCs. - Enhanced Micro-Segmentation
Zero Trust security models are pushing more granular network segmentation strategies. - AI-Driven Network Optimization
Machine learning algorithms are beginning to assist in intelligent network configuration and threat detection.
AWS VPC represents more than just a networking solution—it's a strategic platform for digital transformation. As cloud architectures become increasingly complex, VPC’s flexibility and robust feature set position it as a critical component of modern IT infrastructure. By mastering VPC configuration, organizations can achieve unprecedented levels of security, performance, and scalability.
To take the next step in optimizing your cloud network:
- Conduct a comprehensive VPC architecture review
- Implement infrastructure-as-code for consistent deployments
- Invest in continuous training and certification
- Explore advanced networking services
To start building your AWS VPC today, follow our step-by-step guide to setting up your first VPC, or check out AWS documentation for advanced configurations.
Don't forget to leverage AWS Free Tier to experiment with VPC components and develop your cloud network infrastructure.





