Cloud computing has revolutionized how businesses operate, offering scalability, cost savings, and flexibility. However, with increased cloud adoption comes a surge in security threats. Cybercriminals now target cloud environments, exploiting vulnerabilities such as misconfigurations, weak access controls, and sophisticated attack techniques.
Where Traditional Security Falls Short in the Cloud?
Traditional security tools were designed for static, on-premise environments, where infrastructure was predictable, traffic patterns were stable, and security perimeters were well-defined. However, cloud environments are highly dynamic, distributed, and scalable, making traditional security approaches ineffective.
- Static rule-based detection is insufficient – Attackers continuously evolve their tactics, rendering signature-based and rule-based threat detection ineffective against zero-day threats and polymorphic malware.
- Manual threat analysis slows response times – Security teams struggle to process vast amounts of cloud activity logs, leading to delayed responses and undetected threats.
- Perimeter-based security doesn't work in the cloud – With multi-cloud environments, remote access, and API-driven integrations, traditional firewall-based defenses fail to provide full visibility.
- Lack of contextual awareness – Traditional tools lack real-time visibility into cloud workloads, user behaviors, and access patterns, making it harder to detect insider threats and account takeovers.
These gaps leave organizations vulnerable to advanced threats such as supply chain attacks, lateral movement by attackers, and credential-based intrusions—all of which can go undetected in a cloud environment until significant damage has already occurred.
How AI is Transforming Cloud Security?

AI-powered security solutions bridge this gap by leveraging machine learning, behavioral analytics, and automation to detect and neutralize threats in real time.
Smarter Threat Detection with AI
AI continuously analyzes vast amounts of cloud traffic, user activity, and system behavior to identify subtle anomalies that traditional security tools might miss. Instead of relying on static rules, AI dynamically learns normal behavior and detects deviations—such as unauthorized credential use or low-and-slow data exfiltration attempts.
Modern AI-driven anomaly detection employs unsupervised learning models, which require no pre-labeled data. Techniques like isolation forests and DBSCAN clustering identify suspicious patterns by analyzing dozens of behavioral factors—such as login times, API activity, and data transfer volumes—simultaneously. Advanced time-series analysis helps distinguish legitimate variations in cloud usage from true security threats.
Adaptive Threat Intelligence
Cyber threats evolve constantly, and AI ensures security systems keep up by learning from real-world attack data. Unlike traditional solutions that rely on predefined signatures, AI-powered security adapts through transfer learning, applying insights from past attacks to detect emerging threats.
To remain effective, modern AI security platforms update their detection models every few hours, maintaining high accuracy while minimizing false positives. This ensures AI can rapidly identify new attack patterns—including zero-day exploits and AI-driven cyberattacks—without requiring frequent manual intervention.
Automated Response & Mitigation
AI doesn’t just detect threats—it also responds to them instantly, reducing human workload and minimizing attacker dwell time. Automated security workflows can:
- Revoke compromised credentials before attackers escalate access.
- Isolate infected workloads to contain potential breaches.
- Flag and restrict suspicious API activity to prevent data leaks.
By integrating AI-driven automation, organizations improve their security posture while freeing security teams to focus on higher-priority threats.
Context-Aware Security Decisions
AI enhances identity and access management by analyzing multiple risk factors in real time, including:
- User behavior patterns (e.g., unusual login locations or device changes).
- Device security posture (e.g., outdated software or compromised endpoints).
- Geolocation data to detect unauthorized access attempts.
This enables risk-based access control, allowing security policies to adapt dynamically. Instead of a one-size-fits-all approach, AI ensures security responses are tailored to each specific threat.
AI vs. Traditional Security: A Quick Comparison
Understanding the key differences between AI-powered security and traditional cloud security can help organizations make informed decisions:
| Feature | Traditional Security | AI-Powered Security |
| Threat Detection | Relies on predefined rules and signatures | Uses machine learning to detect anomalies and unknown threats |
| Response Speed | Manual or semi-automated, can be slow | Fully automated response for real-time threat mitigation |
| Adaptability | Needs frequent manual updates | Continuously learns and adapts to new threats |
| Operational Cost | Requires more human intervention, increasing costs | Reduces labor-intensive tasks, lowering costs |
| Scalability | Struggles with high-volume data analysis | Easily scales to analyze vast amounts of cloud data |
| False Positives | Can be high due to static rules | More precise but still needs fine-tuning |
Key Takeaway: AI-driven security is more adaptive, automated, and scalable than traditional security, but it still requires human oversight and proper implementation for optimal results.
Real-World Impact: Business Benefits of AI-Powered Cloud Security
Faster threat detection
AI drastically reduces attacker dwell time—the time an intruder remains undetected in a system—by detecting and responding to threats in real-time instead of hours or days later. This reduces the risk of data breaches and ransomware incidents.
Lower operational costs
Automating security tasks with AI reduces the burden on security teams, minimizing the need for manual investigations and lowering operational expenses. AI can triage alerts, detect false positives, and suggest remediation steps, allowing security analysts to focus on high-priority incidents.
Stronger compliance
AI simplifies compliance with security frameworks like GDPR, HIPAA, SOC 2, and NIST by automating policy enforcement, monitoring cloud activity for violations, and generating audit-ready reports. Organizations can demonstrate continuous security monitoring with AI-driven logging and analytics.
Enhanced resilience
AI-driven security solutions continuously adapt to evolving threats—unlike static rule-based tools that require frequent manual updates. This ensures organizations remain protected against new attack techniques, insider threats, and AI-driven cyberattacks.
The Evolving Cloud Threat Landscape
Who’s Targeting Cloud Data?
Hackers, cybercriminal groups, and nation-state attackers exploit cloud vulnerabilities for financial gain, espionage, or large-scale disruption.
How Attacks Are Evolving?
- Supply chain attacks: Compromising third-party providers to infiltrate cloud systems.
- Zero-day exploits: Targeting unpatched security flaws before fixes are available.
- Credential theft: Using phishing, brute force, and social engineering to gain access.
- Lateral movement: Expanding access within cloud environments to exfiltrate data.
Lessons from Major Cloud Breaches
Common failures—weak identity controls, misconfigurations, and poor monitoring—have led to massive breaches. AI security detects threats early and automates response, closing these gaps.
Understanding AI-Powered Cloud Security
AI-powered security monitors vast amounts of cloud data in real time, learning normal behavior patterns to quickly detect anomalies, insider threats, and zero-day attacks. By leveraging machine learning, behavioral analytics, and automation, AI enhances cloud security in three key ways:
- Threat Detection – Identifies unusual activity, such as unauthorized access attempts, abnormal data transfers, or compromised accounts.
- Automated Response – Instantly isolates threats, revokes access, and alerts security teams to minimize damage.
- Continuous Adaptation – Learns from past incidents, fine-tuning its detection capabilities to counter new and evolving threats.
The data pipeline powering AI security: Cloud security AI requires a sophisticated data foundation. Leading platforms employ distributed stream processing architectures that can ingest and analyze terabytes of data daily with sub-second latency. This typically involves:
- Data collection layers that gather telemetry from cloud logs, network flow data, identity events, and application-generated signals
- Preprocessing engines that normalize and enrich raw data with contextual metadata—transforming "IP address 192.168.1.1 accessed resource X" into "Developer John Smith's device accessed production database from an unusual location"
- Feature extraction systems that convert raw events into behavioral indicators through stateful aggregation
- Scoring engines that evaluate these features against learned patterns to generate risk scores
This architecture enables the AI to process millions of events per second while maintaining context across weeks of historical data—critical for detecting low-and-slow attacks that develop over extended periods.
By reducing false positives and handling routine security tasks, AI frees up human experts to focus on strategic decision-making.
AI Security: Myths vs. Reality
Myth: AI can fully replace human security teams.
Reality: AI acts as a force multiplier, assisting analysts by filtering threats, prioritizing risks, and automating repetitive tasks—but human expertise remains essential for complex decision-making.
Myth: AI security is infallible.
Reality: AI is only as good as the data it learns from. It requires ongoing tuning, high-quality training data, and human oversight to remain effective and prevent blind spots.
Myth: AI-driven security is only for large enterprises.
Reality: AI-powered security tools are now accessible to businesses of all sizes, offering scalable protection that adapts to different cloud environments.
AI Security Tools for Cloud Protection
AI-powered security tools are transforming cloud protection by detecting threats faster, automating responses, and strengthening access control. Instead of just reacting to attacks, these systems continuously adapt and improve, staying ahead of evolving cyber threats.
Smarter Threat Detection
AI constantly monitors cloud activity, identifying suspicious patterns that traditional tools often miss. It analyzes network traffic in real time, detects unusual login behavior, and proactively hunts for hidden threats. By understanding what "normal" looks like, AI can flag anomalies before they turn into full-blown breaches.
Under the hood: The most advanced detection engines use ensemble learning—combining multiple specialized models rather than relying on a single algorithm. For example, one leading cloud security platform employs:
- Probabilistic graphical models for user behavior profiling with 97.3% precision
- Recursive neural networks for session flow analysis that can identify attack patterns across 1,000+ discrete steps
- Transformer models that understand the semantic context of cloud commands to distinguish between benign misconfigurations and malicious activity
These specialized models outperform general-purpose AI by 35-60% in detection accuracy while reducing computational overhead by focusing only on relevant threat patterns.
Automating Incident Response
Speed is everything in security. AI-driven response systems act instantly, isolating compromised accounts, blocking malicious activity, and containing threats before they spread. Instead of overwhelming security teams with endless alerts, AI prioritizes the most critical issues and automates routine containment, allowing human experts to focus on complex investigations.
Reinforcing Access Control
AI improves authentication by continuously verifying user activity rather than relying on a single login. Instead of static passwords and outdated access rules, AI evaluates real-time risk factors—like location, device type, and behavior—to decide whether a user should be granted access. If something seems off, it can prompt additional authentication or temporarily restrict privileges.
AI-Powered Cloud Security Solutions: AWS, Azure, and Google Cloud
While AI-driven security is revolutionizing cloud protection, choosing the right tools for your cloud environment is critical. Major cloud providers offer AI-powered security solutions that integrate seamlessly with their platforms, helping businesses detect threats faster, automate responses, and ensure compliance.
AWS: AI-Driven Security for Scalable Cloud Protection
Amazon Web Services (AWS) provides a comprehensive suite of AI-powered security tools designed to protect workloads in the cloud.
- AWS GuardDuty analyzes vast amounts of data to detect anomalies and potential threats in real-time.
- AWS Security Hub centralizes security insights and compliance status across AWS accounts.
- Amazon Macie uses machine learning to classify and protect sensitive data, helping organizations prevent data leaks.
AWS solutions work together to provide continuous monitoring and automated threat detection, reducing response time and improving overall security.
Microsoft Azure: AI-Enhanced Cloud Security and Compliance
Microsoft Azure integrates AI into its security offerings, combining analytics, automation, and identity protection.
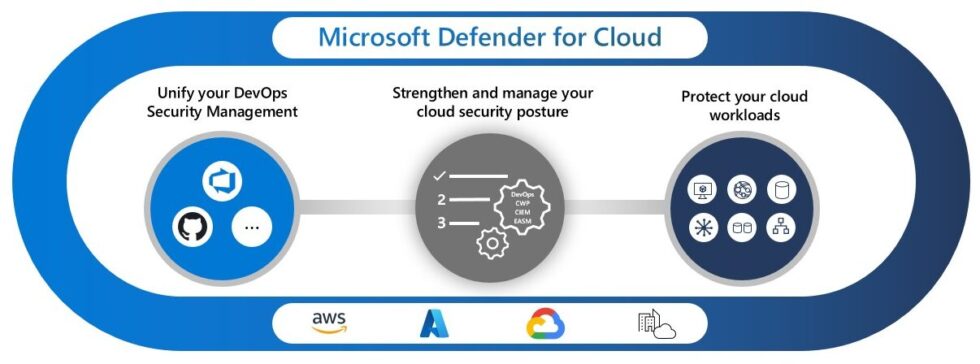
Source - Azure
- Microsoft Defender for Cloud provides AI-driven threat prevention and response across cloud workloads.

Source - Azure
- Azure Sentinel, an AI-powered Security Information and Event Management (SIEM) solution, aggregates and analyzes security data for real-time threat detection.
- Azure AD Identity Protection leverages AI to assess risk levels and detect suspicious login attempts.
With strong compliance capabilities, Azure's AI-powered tools help businesses maintain security while meeting regulatory requirements.
Google Cloud: AI-First Security for a Zero-Trust World
Google Cloud integrates AI security across its ecosystem, focusing on threat intelligence, proactive defense, and zero-trust security models.
- Chronicle Security Operations leverages Google’s AI infrastructure to detect and investigate cyber threats at scale.
- Google Security Command Center provides risk assessments and AI-powered security insights to help organizations manage cloud threats.
- BeyondCorp Enterprise, built on a zero-trust model, ensures secure access by continuously analyzing user and device risk.
Google Cloud’s AI-driven security approach enables faster decision-making, reducing reliance on reactive security measures.
Bringing It All Together: AI Security in Multi-Cloud and Hybrid Environments
Organizations often operate across multiple cloud providers, creating challenges in securing diverse environments. AI-powered security solutions can:
- Unify threat detection across AWS, Azure, and Google Cloud, reducing security silos.
- Automate response actions across different platforms for consistent cloud security policies.
- Enhance visibility with AI-driven insights, helping teams proactively address threats before they escalate.
Choosing the right combination of AI security tools depends on your specific cloud infrastructure and business needs.
AI-Powered Cloud Security and Compliance
With cloud adoption growing, organizations must navigate complex regulatory requirements to protect sensitive data and maintain compliance. AI is helping businesses streamline security processes while ensuring they meet industry standards.
How AI Helps Meet Compliance Standards?
AI-driven security solutions assist organizations in adhering to key regulations such as GDPR, HIPAA, SOC 2, and PCI DSS. By continuously monitoring cloud environments, AI can:
- Automate compliance checks, reducing manual auditing efforts.
- Detect security misconfigurations that could lead to violations.
- Provide real-time alerts to help security teams take corrective action.
Automating Security Audits and Risk Assessments
Traditional compliance audits can be time-consuming and error-prone. AI-powered tools help by:
- Scanning cloud environments for security gaps and misconfigurations.
- Generating compliance reports automatically, making it easier for businesses to demonstrate adherence to regulations.
- Predicting potential compliance risks before they become issues.
Balancing Data Privacy and Cloud Security
One of the biggest challenges in cloud security is protecting user privacy while ensuring strong security measures. AI-powered security solutions:
- Use advanced encryption techniques to secure sensitive data.
- Implement privacy-preserving AI models, ensuring compliance without compromising user confidentiality.
- Enable continuous monitoring to detect unauthorized data access.
By leveraging AI, organizations can strengthen cloud security while reducing the complexity of regulatory compliance.
The Human Element in AI Cloud Security
While AI takes on the heavy lifting, security teams still play a crucial role. Their focus is shifting from manual monitoring to overseeing AI-driven processes, fine-tuning detection models, and analyzing high-level threats. This evolution requires new skills in AI oversight, automation management, and strategic threat intelligence.
Adopting AI security isn’t just about implementing technology—it’s about building trust and understanding across an organization. Employees need to see AI as a partner, not a replacement. Clear communication, hands-on training, and real-world examples of AI success can help security teams embrace automation rather than resist it.
Implementing AI Security in Cloud Environments
Successfully integrating AI into cloud security starts with understanding where your defenses stand today and how AI can enhance them. A well-planned approach ensures AI works seamlessly with existing security frameworks while addressing real threats.
Assessing Your Cloud Security Posture
Before adopting AI-driven security solutions, organizations need a clear picture of their current security landscape. This means evaluating existing defenses, identifying vulnerabilities, and assessing AI readiness. Knowing where gaps exist helps in selecting AI tools that provide the most impact.
Choosing the Right AI Security Solutions
AI-powered security should fit naturally into cloud environments rather than being an add-on that complicates workflows. The best solutions integrate with existing cloud security frameworks, compliance requirements, and incident response processes, ensuring smooth implementation and maximum effectiveness.
Running an Effective AI-Driven Cloud Security Program
AI isn't just about detection—it's about efficiency. The real challenge is making sure AI enhances security operations without overwhelming teams.
Managing Alerts Without Alert Fatigue
Security teams often face an overload of alerts, many of which turn out to be false positives. AI helps filter and prioritize threats, ensuring analysts focus on what truly matters rather than being buried under a flood of notifications.
Performance metrics that matter: When evaluating AI security systems, focus on actionable indicators rather than marketing claims. The most reliable platforms achieve:
- False positive rates below 0.5% in production environments
- 85%+ reduction in tier-1 security alerts requiring human review
- Mean-time-to-detection improvements of 76% or greater versus traditional tools
- Automated investigation of 95%+ of initial security signals
These benchmarks represent the practical value of AI security—reducing analyst workload while accelerating threat detection and response.
Streamlining Investigations and Response
When a breach attempt occurs, AI accelerates forensic analysis by connecting the dots between different attack signals. Instead of manually piecing together logs, security teams get a clear view of attack patterns, helping them respond faster and more effectively.
Making the Business Case for AI Cloud Security
For AI security to succeed, executive support is essential. Leadership teams want to know why AI is worth the investment and how it impacts business operations.
Understanding Costs and ROI
The cost of AI-driven security depends on business size, cloud complexity, and regulatory requirements. However, the return on investment is clear—reduced breach risks, lower downtime, and more efficient security operations translate into significant cost savings.
Securing Leadership Buy-In
To get executive approval, security leaders must frame AI security as a business enabler rather than just a technical upgrade. Demonstrating how AI reduces financial risk, strengthens compliance, and improves operational efficiency makes the case for investment much stronger.
AI’s Limitations & Ethical Considerations in Cloud Security
While AI is transforming cloud security, it has inherent limitations that organizations must address. Over-reliance on AI without understanding its challenges can lead to security gaps.
False Positives & False Negatives
AI-driven threat detection analyzes vast amounts of data, but it is not always accurate.
- False positives occur when the system flags legitimate activities as threats, leading to unnecessary alerts and operational slowdowns.
- False negatives occur when AI fails to detect actual threats, leaving systems vulnerable to attack.
Excessive false positives can overwhelm security teams, while false negatives can result in undetected breaches.
Bias in AI Decision-Making
AI models are trained on historical data, which may contain biases that affect security decisions.
- AI may incorrectly categorize certain user behaviors as high-risk due to incomplete or biased training data.
- Bias in AI-based access control can lead to unintended restrictions or security blind spots.
Organizations must ensure AI models are trained on diverse and representative datasets to minimize bias.
The Need for Human Oversight
AI should enhance, not replace, human decision-making in security operations.
- Security teams must monitor AI-driven alerts and validate decisions to ensure accuracy.
- AI models require ongoing adjustments to adapt to new threats.
A balance between automation and human expertise is essential to avoid security failures.
Ethical Use of AI in Cloud Security
AI-driven security measures must align with privacy laws and ethical guidelines.
- AI should provide transparency in how security decisions are made.
- Organizations must remain accountable for AI-driven actions and ensure compliance with regulations such as GDPR and CCPA.
Key Takeaway: AI is a powerful tool for cloud security, but it must be properly monitored, trained, and supplemented by human expertise to avoid unintended risks.
Common Pitfalls in AI Cloud Security Adoption
AI-powered security can enhance cloud protection, but organizations often face challenges in implementation. Here are some common pitfalls and how to avoid them.
Not Properly Training AI Models
AI security tools must be trained on diverse, high-quality data to function effectively.
- Poorly trained AI models can result in inaccurate threat detection.
- Failure to update AI models regularly can leave systems vulnerable to emerging threats.
Solution: Continuously train AI models with real-world attack data and refine algorithms based on evolving threats.
Ignoring the Need for Human Oversight
AI security tools are not infallible, and complete reliance on automation can be risky.
- AI may misinterpret security events, requiring human intervention for accurate decision-making.
- Overreliance on automation can lead to missed security gaps.
Solution: Implement a "human-in-the-loop" approach where security professionals validate AI-driven security actions.
Failing to Integrate AI Security with Existing Cloud Tools
AI-powered security must work in tandem with an organization’s existing security infrastructure.
- Lack of integration can create gaps in security coverage.
- Fragmented monitoring can make it difficult to detect and respond to threats efficiently.
Solution: Ensure AI security solutions seamlessly integrate with cloud-native security tools like AWS GuardDuty, Azure Security Center, and Google Security Command Center.
Overlooking Compliance & Privacy Implications
AI security solutions must adhere to regulatory requirements.
- Mishandling sensitive data with AI-driven analytics can result in compliance violations.
- AI systems should be designed to align with industry standards such as GDPR, CCPA, and HIPAA.
Solution: Implement privacy-first AI security measures and ensure AI-driven threat detection aligns with compliance standards.
Key Takeaway: AI security is powerful, but success depends on proper training, human oversight, integration, and regulatory compliance.
The Future of AI-Powered Cloud Security
AI-Driven Security Automation
Future advancements will see AI handling more security operations autonomously, reducing the burden on human teams.
The Rise of AI-Powered Cyber Threats
As organizations adopt AI security, attackers are also leveraging AI to launch more sophisticated attacks, making AI security an ongoing necessity.
Your Action Plan: Getting Started with AI Cloud Security
Step-by-Step Roadmap
- Assess current cloud security posture.
- Identify AI security tools that fit business needs.
- Develop a structured AI security implementation plan.
- Train teams and establish monitoring processes.
- Continuously measure effectiveness and optimize AI security models.