Welcome to Part 3 of this Terraform blog, where we take a deep dive into advanced concepts and real-world use cases that will help you harness Terraform’s full potential in your infrastructure automation journey. In Part 1 and Part 2, we laid the foundation with core concepts, workflows, and intermediate best practices for managing infrastructure as code. Now, we’ll explore how to automate deployments with CI/CD pipelines, handle complex infrastructure setups, troubleshoot common errors, and implement security best practices.
1. Terraform and CI/CD Integration
In modern development practices, continuous integration and continuous delivery (CI/CD) pipelines are vital for automating and streamlining workflows. Terraform fits naturally into CI/CD pipelines, making it easy to manage infrastructure changes automatically with tools like Jenkins, GitLab CI, and AWS CodePipeline. In this section, we’ll look at how to automate Terraform deployments in Jenkins and GitLab CI, as well as integrate Terraform with AWS CodePipeline.
1.1 Automating Terraform with Jenkins or GitLab CI
Integrating Terraform into CI/CD pipelines is a powerful way to manage infrastructure deployments automatically, reducing manual intervention and ensuring consistency across environments. Let’s break down how to use Terraform with Jenkins and GitLab CI.
Setting up Jenkins for Terraform
To automate Terraform with Jenkins, you need to first install Terraform on your Jenkins server. You can either install it manually or use a plugin like Terraform or ShiningPanda to integrate Terraform seamlessly. Once set up, create a Jenkins job that includes steps like terraform init, terraform plan, and terraform apply to deploy infrastructure.
Here’s a simple example of a Jenkins pipeline for Terraform:
| bash terraform init # Initialize the Terraform working directory terraform plan # Show the execution plan for infrastructure changes terraform apply # Apply the changes to create/update infrastructure |
You can configure Jenkins to automatically trigger this job whenever changes are pushed to your code repository, making infrastructure deployment part of your continuous integration process.
Using GitLab CI/CD with Terraform
In GitLab CI/CD, you can automate Terraform workflows by configuring a .gitlab-ci.yml file in your repository. Here’s an example:
| yaml stages: - init - plan - apply variables: TF_VERSION: "0.14.0" AWS_REGION: "us-east-1" before_script: - terraform --version - terraform init init: stage: init script: - terraform init plan: stage: plan script: - terraform plan apply: stage: apply script: - terraform apply -auto-approve |
By defining stages like init, plan, and apply, GitLab CI automates the deployment of your infrastructure, ensuring that every change is consistently applied.
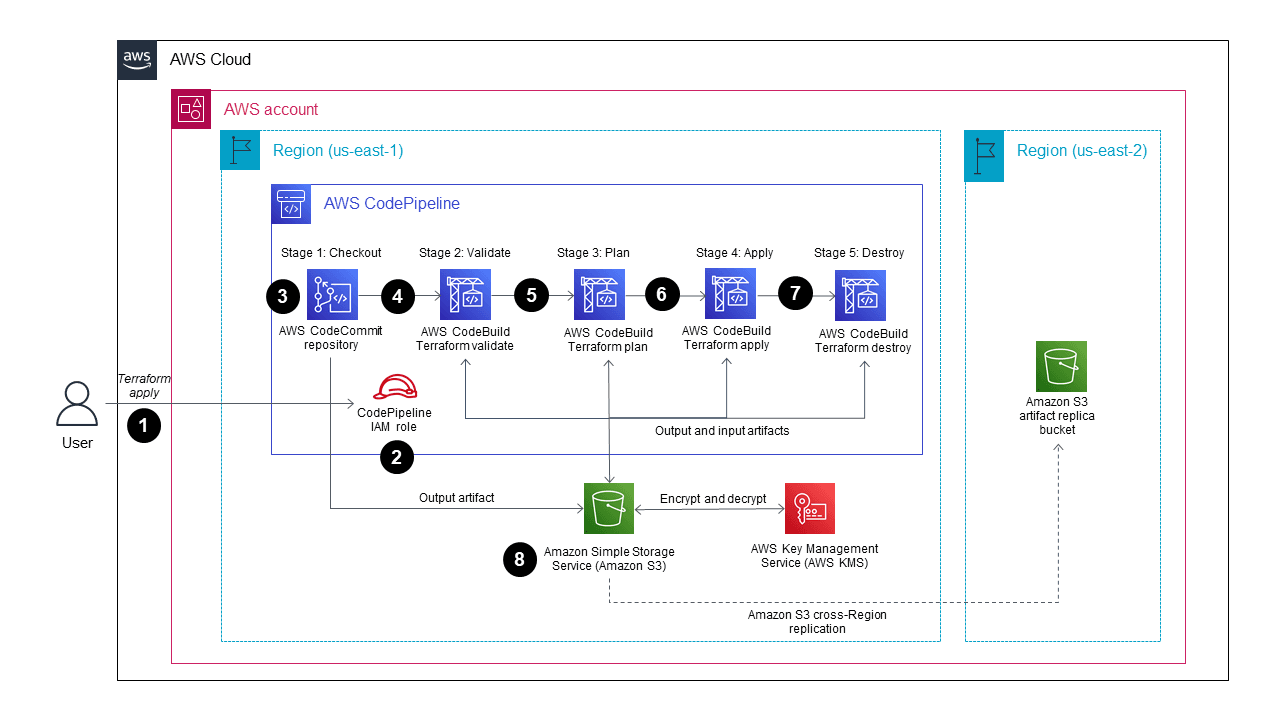
1.2 Using Terraform with AWS CodePipeline
 Source: AWS Docs
Source: AWS Docs
AWS CodePipeline is a fully managed service that automates software deployment, and it can be used to automate Terraform-based infrastructure provisioning. When you integrate Terraform with CodePipeline, you can automate the deployment of infrastructure across multiple stages.
Setting up CodePipeline with Terraform
To get started with Terraform and AWS CodePipeline, you’ll first set up stages in your pipeline, such as:
- Source Stage: Pulls Terraform configuration from a Git repository (e.g., GitHub or AWS CodeCommit).
- Build Stage: Executes Terraform commands like terraform init and terraform plan in AWS CodeBuild.
- Deploy Stage: Applies the Terraform changes using terraform apply.
Whenever changes are made to the source repository, CodePipeline will automatically trigger the pipeline to apply those changes. This ensures that your infrastructure is always aligned with your code.
2. Common Use Cases and Real-world Examples
Now that we’ve covered CI/CD integration, let’s explore some practical, real-world scenarios where Terraform shines. These use cases demonstrate how Terraform can simplify complex infrastructure deployments, making them more manageable, repeatable, and scalable.
2.1 Deploying a Web Application Infrastructure with Terraform
Terraform simplifies the process of deploying a web application stack, ensuring that the entire infrastructure is codified and reproducible. Let’s look at a basic setup that deploys a web application using AWS EC2 and RDS.
- Creating EC2 Instances:
Use Terraform to automate the provisioning of EC2 instances for hosting your web servers.
| hcl resource "aws_instance" "web_server" { ami = "ami-xxxxxxxx" instance_type = "t2.micro" tags = { Name = "WebServer" } } |
- Configuring RDS for Database:
Terraform can also provision an RDS instance for your application’s database.
| hcl resource "aws_db_instance" "mydb" { engine = "mysql" instance_class = "db.t2.micro" name = "mydb" username = "admin" password = "password" allocated_storage = 20 } |
- Networking and Security:
Terraform helps set up VPCs, subnets, security groups, and load balancers to ensure proper network isolation and high availability.
| hcl resource "aws_security_group" "web_sg" { name = "web_sg" description = "Allow HTTP and SSH" ingress { from_port = 22 to_port = 22 protocol = "tcp" cidr_blocks = ["0.0.0.0/0"] } ingress { from_port = 80 to_port = 80 protocol = "tcp" cidr_blocks = ["0.0.0.0/0"] } } |
By using Terraform to automate this setup, you ensure that your web application infrastructure is reproducible and version-controlled.
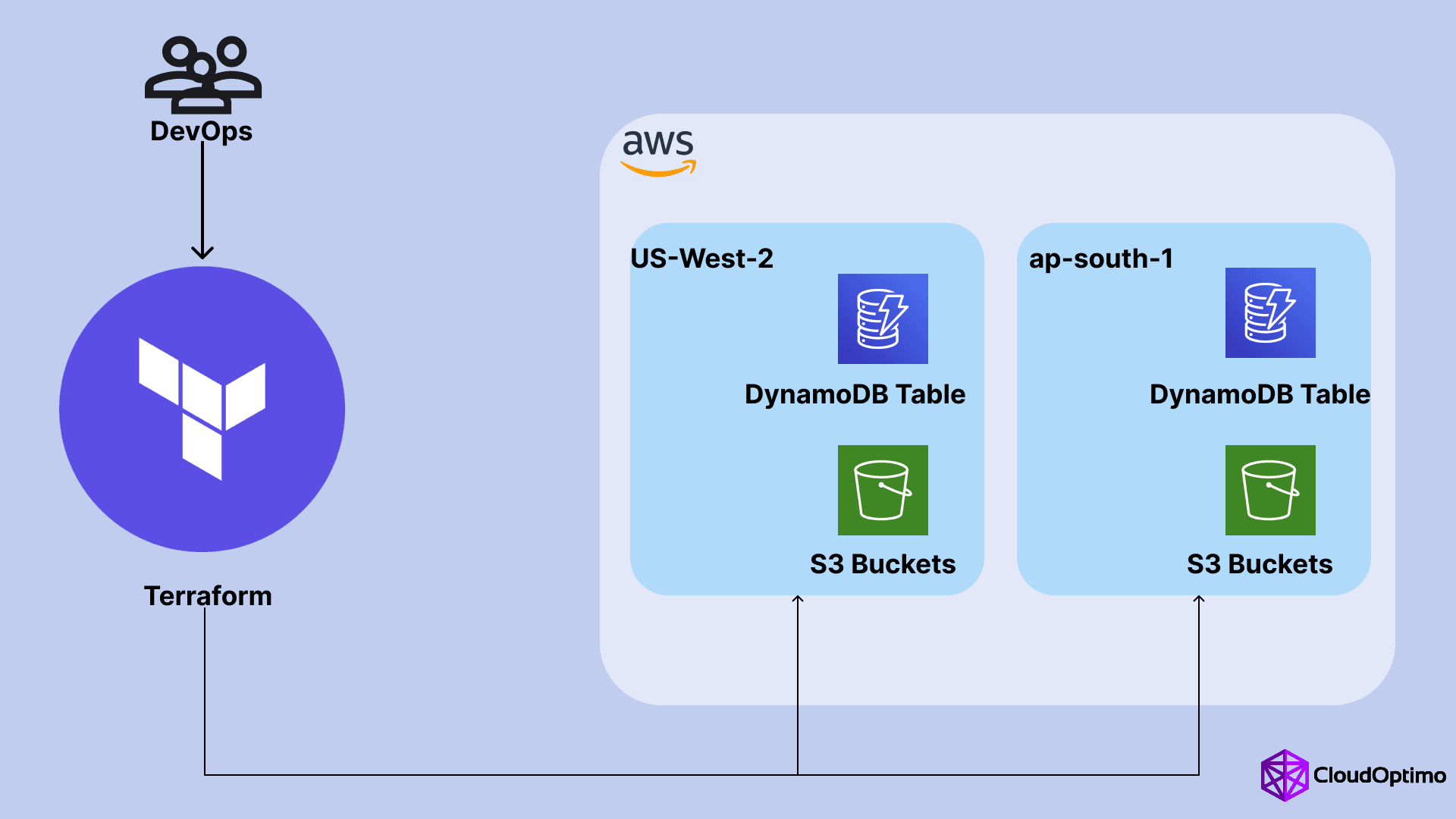
2.2 Managing Multi-Region AWS Deployments
 Deploying infrastructure across multiple AWS regions is key for ensuring availability, disaster recovery, and low-latency access. Terraform makes multi-region deployments straightforward.
Deploying infrastructure across multiple AWS regions is key for ensuring availability, disaster recovery, and low-latency access. Terraform makes multi-region deployments straightforward.
- Configuring Providers for Multiple Regions:
You can define multiple provider blocks to deploy resources across different AWS regions.
| hcl provider "aws" { region = "us-east-1" } provider "aws" { alias = "west" region = "us-west-1" } |
- State Management for Multi-Region Deployments:
Managing state files consistently across regions is crucial. Using remote state backends, like AWS S3 with DynamoDB for state locking, ensures that your state is always synchronized.
2.3 Integrating Terraform with AWS CloudWatch for Monitoring
Terraform can automate the creation of CloudWatch resources for monitoring your AWS infrastructure. Here’s an example of how to create CloudWatch alarms and dashboards using Terraform.
| hcl resource "aws_cloudwatch_alarm" "cpu_high" { alarm_name = "high-cpu-alarm" metric_name = "CPUUtilization" namespace = "AWS/EC2" statistic = "Average" comparison_operator = "GreaterThanThreshold" threshold = 80 period = 300 evaluation_periods = 2 alarm_description = "This metric monitors high CPU utilization" actions_enabled = true } |
This allows you to automatically set up monitoring for your EC2 instances and ensure that you’re alerted to any performance issues.
3. Troubleshooting and Debugging Terraform with AWS
In large-scale or complex infrastructure deployments, issues will inevitably arise. Terraform provides several tools and techniques to troubleshoot and debug configurations efficiently.
3.1 Debugging Terraform Configuration Issues
If your Terraform configurations are encountering errors, here are some strategies to help:
- terraform validate:
This command checks if your Terraform configurations are syntactically correct. It’s a quick way to identify any issues before applying changes.
| bash terraform validate |
- terraform plan:
Running terraform plan provides a detailed view of the changes Terraform will make. This command is valuable for identifying unintended changes.
| bash terraform plan |
- Terraform Logs:
If you're troubleshooting deeper issues, enabling Terraform’s debug logs can provide detailed insight.
| bash export TF_LOG=DEBUG terraform apply |
3.2 Handling Terraform State Conflicts
Terraform state conflicts can occur when multiple team members are working on the same infrastructure. To avoid conflicts:
- Use Remote Backends: Store your Terraform state remotely, such as in S3 with DynamoDB for state locking, to ensure no conflicts.
- State Locking: Prevent concurrent state modifications by using Terraform’s state locking mechanism.
| bash terraform force-unlock LOCK_ID |
This ensures safe and conflict-free collaboration on shared infrastructure.
4. Security Considerations and Best Practices
When working with Terraform, especially in production environments, security is a top priority. Let’s explore some security best practices for managing AWS resources with Terraform.
4.1 Managing Security Groups with Terraform
Security groups are a critical part of your AWS infrastructure security. Terraform allows you to automate the creation and management of security groups, ensuring consistent access control.
| hcl resource "aws_security_group" "web_sg" { name = "web_sg" description = "Allow HTTP, HTTPS, and restricted SSH access" # Restrict SSH (port 22) to trusted IPs only for secure access (e.g., your office IP range) ingress { from_port = 22 to_port = 22 protocol = "tcp" cidr_blocks = ["<your-trusted-ip-range>/32"] # Replace with your trusted IP or CIDR block } # Allow HTTP (port 80) from anywhere (but consider moving to HTTPS) ingress { from_port = 80 to_port = 80 protocol = "tcp" cidr_blocks = ["0.0.0.0/0"] # Ensure this is necessary, or restrict further if possible } # Allow HTTPS (port 443) from anywhere, for secure encrypted traffic ingress { from_port = 443 to_port = 443 protocol = "tcp" cidr_blocks = ["0.0.0.0/0"] } } |
This ensures your EC2 instances can securely communicate while restricting unauthorized access.
4.2 Managing Secrets in Terraform
Managing secrets securely is paramount when using Terraform to provision infrastructure. Here are some best practices for handling secrets:
- AWS Secrets Manager:
Store and retrieve secrets like API keys securely using AWS Secrets Manager.
| hcl resource "aws_secretsmanager_secret" "example" { name = "my_secret" } resource "aws_secretsmanager_secret_version" "example" { secret_id = aws_secretsmanager_secret.example.id secret_string = jsonencode({ username = "user", password = "pass" }) } |
- HashiCorp Vault:
For even more security, integrate Terraform with HashiCorp Vault to manage sensitive data.
By following these best practices, you can protect sensitive information and keep your infrastructure secure.
5. Advanced Terraform Strategies
As your expertise with Terraform grows, you will encounter complex scenarios where advanced strategies and techniques are essential to manage infrastructure at scale. In this section, we explore some of these advanced strategies, including immutable infrastructure and disaster recovery planning.
5.1 Immutable Infrastructure with Terraform
Immutable infrastructure is a concept where infrastructure components (like servers or VMs) are never modified after deployment. Instead of updating existing resources, you replace them entirely when changes are needed. This approach reduces the risk of configuration drift and ensures consistency across environments. Terraform supports immutable infrastructure through its resource management capabilities, such as terraform taint and terraform destroy.
Using terraform taint and terraform destroy
To implement immutable infrastructure, you can “taint” a resource, marking it for destruction and replacement on the next apply. Here’s how to do that:
- Taint a Resource:
If you want to replace a resource, you can use the terraform taint command. This marks the resource as tainted, so Terraform will destroy and recreate it during the next apply.
| bash terraform taint aws_instance.example |
- Destroy a Resource:
Alternatively, if you want to explicitly destroy a resource, you can use terraform destroy.
| bash terraform destroy -target=aws_instance.example |
By employing these commands, you ensure that your infrastructure remains in a consistent state without manual updates to existing resources. Each time a change is needed, Terraform replaces the old resources with new, clean instances.
5.2 Terraform for Disaster Recovery Planning
Disaster recovery (DR) is crucial for ensuring business continuity in the face of infrastructure failures. Terraform can help automate disaster recovery plans by codifying your infrastructure setup, allowing for quick and consistent recovery in multiple regions.
Using Terraform for DR Setup
You can set up redundant infrastructure across multiple regions or availability zones, ensuring that in the event of a failure, your infrastructure can be quickly restored.
- Multi-Region Deployment:
You can use Terraform to deploy resources across multiple regions, ensuring high availability and disaster recovery capabilities.
| hcl provider "aws" { region = "us-east-1" } resource "aws_instance" "primary_region" { ami = "ami-xxxxxxxx" instance_type = "t2.micro" availability_zone = "us-east-1a" } provider "aws" { alias = "secondary_region" region = "us-west-1" } resource "aws_instance" "secondary_region" { provider = aws.secondary_region ami = "ami-xxxxxxxx" instance_type = "t2.micro" availability_zone = "us-west-1a" } |
This setup ensures that if one region fails, your application can failover to the secondary region, keeping services up and running.
- Automating Recovery:
Terraform can automate the creation of recovery resources, such as databases, networking configurations, and instances, reducing the time and effort required for manual recovery.
6. Terraform Cloud and Enterprise
As Terraform’s popularity grows within teams and organizations, using Terraform Cloud and Terraform Enterprise has become a critical part of scaling infrastructure management. These platforms offer advanced features like remote state management, collaboration tools, and policy enforcement.
6.1 Introduction to Terraform Cloud and Enterprise
Terraform Cloud and Terraform Enterprise are premium offerings from HashiCorp that provide robust features for team collaboration, secure management of Terraform state, and enhanced security for large-scale deployments.
Benefits of Terraform Cloud
- Remote State Management: Terraform Cloud automatically stores and manages your Terraform state files, ensuring they are securely stored and accessible across teams.
- Collaboration and Access Control: With Terraform Cloud, you can enable role-based access control (RBAC), ensuring that only authorized users can execute certain operations.
- Automation and Policy Enforcement: You can set up policies to automatically enforce best practices or regulatory compliance, ensuring that all infrastructure changes adhere to organizational standards.
Use Cases for Terraform Enterprise
Terraform Enterprise expands on Terraform Cloud with more advanced features for larger teams, such as:
- Private module registry for reusable infrastructure components
- Enhanced security with on-premises deployment options
- Advanced governance and audit logs for compliance tracking
These features make Terraform Cloud and Enterprise a valuable tool for managing infrastructure at scale while ensuring collaboration and security across development teams.
7. Performance and Optimization
In large-scale AWS environments, Terraform’s performance can sometimes become a bottleneck when applying changes. Optimizing the performance of your Terraform runs is crucial to ensure faster execution times and efficient management of your infrastructure.
7.1 Terraform Performance Tuning
Terraform performance can be optimized in several ways, particularly when managing large AWS environments with many resources. Let’s look at some strategies to improve the execution times for terraform apply and terraform plan.
1. Using -target Option
Instead of applying changes to the entire infrastructure, use the -target option to apply changes to specific resources. This can reduce execution time by limiting the scope of Terraform operations.
| bash terraform apply -target=aws_instance.example |
2. Parallelism
Terraform applies resources in parallel by default. However, in some cases, you can tune the -parallelism flag to control the number of concurrent operations. Increasing parallelism can speed up the process, but be careful not to exceed AWS’s API rate limits.
| bash terraform apply -parallelism=10 |
3. Optimize State Management
For large-scale environments, consider using a remote backend (like S3 with DynamoDB for state locking) to ensure efficient and scalable state management. This reduces the load on your local machine and improves performance when collaborating with teams.
4. State File Segmentation
Break down large state files into smaller chunks by using workspaces, modules, or remote backends. This can help reduce the amount of data Terraform needs to track during each apply.
8. Multi-Cloud Strategy and Provider Comparison
While Terraform is most commonly associated with AWS, it supports multiple cloud providers, including Azure, Google Cloud, and more. Adopting a multi-cloud strategy can help reduce the risks associated with vendor lock-in and offer increased flexibility and reliability.
8.1 Comparing Terraform with AWS vs Other Providers
When managing infrastructure with Terraform, you’ll find similarities and differences across cloud providers. Here’s a quick comparison between how Terraform handles AWS resources versus other cloud platforms.
| Feature | AWS | Azure | Google Cloud |
| Provider Configuration | provider "aws" {} | provider "azurerm" {} | provider "google" {} |
| Resource Types | EC2, RDS, Lambda, etc. | Virtual Machines, Storage, etc. | Compute Engine, BigQuery, etc. |
| Authentication | AWS IAM Roles and Policies | Azure Active Directory (AAD) | Google Cloud Service Accounts |
| State Management | S3, DynamoDB for state locking | Azure Storage for state | Google Cloud Storage for state |
| Multi-Region Deployment | Supported across all regions | Limited to selected regions | Supported in all regions |
| Support for Kubernetes | EKS, Fargate | AKS | GKE |
Each cloud provider has unique features, and Terraform makes it easy to integrate with them all. Depending on your needs, you can use Terraform to manage resources in AWS, Azure, and Google Cloud simultaneously, without the need for multiple toolsets.
9. Cloud Migration and Hybrid Cloud Infrastructure
As organizations evolve, many are moving toward hybrid or multi-cloud strategies. Terraform plays a significant role in facilitating these transitions by providing a unified framework to manage infrastructure across cloud platforms and on-premises environments.
9.1 Migrating from AWS CloudFormation to Terraform
If you’ve previously used AWS CloudFormation to manage your infrastructure, migrating to Terraform offers several advantages, such as better state management, easier refactoring, and multi-cloud support. Here’s how you can approach the migration:
- Export CloudFormation Templates:
Start by exporting your CloudFormation templates to understand the current infrastructure configuration. - Convert to Terraform Configuration:
Manually convert the CloudFormation template into Terraform HCL configuration files. While this can be time-consuming, there are tools like cloudformation-to-terraform to help with the conversion process. - Use Terraform’s Import Feature:
For existing AWS resources, use Terraform’s terraform import to bring them under Terraform management.
| bash terraform import aws_instance.example i-xxxxxxxxxx |
By using Terraform, you gain the ability to manage infrastructure in a more flexible and portable way, reducing reliance on AWS-specific tools.
9.2 Managing Hybrid Cloud Infrastructure
A hybrid cloud infrastructure involves integrating on-premises resources with public cloud services. Terraform enables you to manage resources across both environments seamlessly.
Integrating AWS and On-Premises
Terraform can manage both AWS resources and on-premises infrastructure through the use of providers like aws for cloud resources and vsphere for VMware environments.
| hcl provider "aws" { region = "us-west-1" } provider "vsphere" { user = "vcenter_user" password = "vcenter_pass" vsphere_server = "vcenter.local" } resource "aws_instance" "example" { ami = "ami-xxxxxxxx" instance_type = "t2.micro" } resource "vsphere_virtual_machine" "example" { name = "vm_example" resource_pool_id = "resource_pool" datacenter_id = "datacenter" } |
This allows for a seamless hybrid infrastructure setup, where both cloud and on-premise resources are managed through a single tool and workflow.
By leveraging Terraform for hybrid cloud and cloud migration, you can create flexible, scalable, and cost-effective infrastructures that span across on-premises and multiple cloud providers.
10. Containers and Kubernetes with Terraform
As organizations shift to cloud-native architectures, managing containerized applications has become a priority. Terraform provides seamless integration with various container platforms like AWS ECS (Elastic Container Service) and EKS (Elastic Kubernetes Service), allowing developers to automate container deployments and manage infrastructure in code.
10.1 Managing ECS and EKS with Terraform
Automating the deployment of containers with Terraform can simplify infrastructure management. ECS and EKS are two popular container orchestration services on AWS, and Terraform provides robust support for managing these services.
ECS with Terraform
Amazon ECS is a fully managed container orchestration service that makes it easy to run, scale, and secure Docker containers. Terraform can automate the creation of ECS clusters, task definitions, and service configurations.
Here’s an example of setting up an ECS cluster with Terraform:
| hcl resource "aws_ecs_cluster" "example" { name = "example-cluster" } resource "aws_ecs_task_definition" "example" { family = "example-task" container_definitions = jsonencode([{ name = "example-container" image = "nginx:latest" cpu = 10 memory = 512 essential = true }]) } resource "aws_ecs_service" "example" { name = "example-service" cluster = aws_ecs_cluster.example.id task_definition = aws_ecs_task_definition.example.arn desired_count = 2 } |
EKS with Terraform
Amazon EKS is a fully managed Kubernetes service, and Terraform helps automate the configuration of Kubernetes clusters and deployment of containerized workloads.
Example of configuring an EKS cluster:
| hcl provider "aws" { region = "us-west-2" } module "eks" { source = "terraform-aws-modules/eks/aws" cluster_name = "example-cluster" cluster_version = "1.18" subnets = data.aws_subnets.selected.ids vpc_id = data.aws_vpc.selected.id } |
With this setup, you can create and scale Kubernetes clusters in AWS with ease, all managed through Terraform.
10.2 Terraform for Docker Infrastructure
Docker is a containerization platform that enables developers to create, deploy, and run applications in containers. Terraform can manage Docker containers and integrate with Docker environments to automate container deployment.
Managing Docker Containers
The Terraform docker provider allows you to manage Docker containers and images, simplifying the deployment of containerized applications.
Example of managing Docker containers with Terraform:
| hcl provider "docker" {} resource "docker_container" "example" { name = "example-container" image = "nginx:latest" ports { internal = 80 external = 8080 } } |
Building Docker Images
Terraform can also be used to build and deploy Docker images, allowing developers to automate the process of creating container images for their applications.
| hcl resource "docker_image" "example" { name = "myapp:latest" build { context = "./app" } } |
By managing Docker with Terraform, developers can ensure consistency and automation in their container deployments.
11. Using Terraform with AWS Services
Terraform extends its capabilities beyond basic infrastructure management. AWS services like Elastic Beanstalk, Redshift, and SageMaker are also supported by Terraform, enabling developers to manage these advanced services as part of their infrastructure as code.
11.1 Terraform for AWS Elastic Beanstalk
AWS Elastic Beanstalk is a Platform as a Service (PaaS) offering that simplifies the deployment of applications. Terraform allows for the automation of Elastic Beanstalk environment creation, configuration, and updates.
Here’s an example of configuring an Elastic Beanstalk environment with Terraform:
| hcl resource "aws_elastic_beanstalk_application" "example" { name = "example-app" description = "My Example App" } resource "aws_elastic_beanstalk_environment" "example" { name = "example-env" application = aws_elastic_beanstalk_application.example.name solution_stack_name = "64bit Amazon Linux 2 v3.3.6 running Node.js" } |
This setup allows for easy and repeatable deployment of applications on Elastic Beanstalk.
11.2 Terraform for AWS Redshift
AWS Redshift is a fully managed data warehousing service. Using Terraform to manage Redshift clusters and configurations helps automate the deployment and scaling of data warehouses.
Example configuration:
| hcl resource "aws_redshift_cluster" "example" { cluster_identifier = "example-cluster" database_name = "dev" master_username = "admin" master_password = "password" node_type = "dc2.large" number_of_nodes = 2 } |
Terraform simplifies the management of Redshift clusters, making it easier to scale and maintain your data warehousing infrastructure.
11.3 Terraform for AWS SageMaker
AWS SageMaker helps with machine learning model building and deployment. Terraform can automate the setup of SageMaker environments and model deployments, enabling faster and more consistent ML workflows.
Example of using Terraform for SageMaker:
| hcl resource "aws_sagemaker_model" "example" { name = "example-model" primary_container { image = "123456789012.dkr.ecr.us-west-2.amazonaws.com/my-image:latest" } } |
By managing SageMaker with Terraform, you can streamline the process of deploying machine-learning models into production environments.
12. Integrating Terraform with AWS Marketplace Solutions
AWS Marketplace offers a wide range of pre-configured software solutions that can be deployed with just a few clicks. Terraform allows you to integrate with AWS Marketplace solutions and automate their deployment and configuration.
12.1 Deploying AWS Marketplace Software with Terraform
With Terraform, you can automate the deployment of AWS Marketplace products, saving time and reducing the complexity of setting up third-party software. To deploy AWS Marketplace software, you’ll typically use AWS resources like EC2, Lambda, or S3.
Example:
| hcl resource "aws_instance" "marketplace_example" { ami = "ami-xxxxxxxx" # AWS Marketplace AMI ID instance_type = "t2.medium" } |
Terraform helps integrate these third-party solutions into your infrastructure, ensuring that they are deployed consistently across environments.
13. Managing Large-Scale Infrastructure with Terraform
As organizations grow, managing large-scale infrastructure with Terraform requires careful planning, efficient workflows, and best practices to maintain consistency and scalability.
13.1 Managing Infrastructure for Large Organizations
For large organizations, Terraform can handle the complexity of deploying and managing infrastructure at scale. Organizing Terraform code using workspaces and version control ensures efficient team collaboration and consistency across environments.
Using Multiple Workspaces
Workspaces allow you to manage different environments (such as dev, staging, and production) within the same Terraform configuration. This enables clean separation between environments.
Example:
| bash terraform workspace new dev terraform workspace new prod |
Collaboration with Version Control
Storing Terraform code in version-controlled repositories (like Git) allows teams to collaborate on infrastructure changes safely. Each change can be tracked, reviewed, and deployed consistently.
13.2 Terraform and AWS Organizations
AWS Organizations allows you to manage multiple AWS accounts, providing consolidated billing and centralized governance. Terraform integrates with AWS Organizations to help manage resources across multiple accounts.
Example:
| hcl resource "aws_organizations_organizational_unit" "example" { name = "example-ou" parent_id = aws_organizations_organization.example.id } |
Terraform simplifies resource management across multiple accounts, ensuring that large organizations can scale their infrastructure with ease.
14. Terraform’s Role in DevOps
Terraform plays a significant role in DevOps by automating infrastructure management and integrating with CI/CD pipelines. This section explores Terraform’s contributions to DevOps, including testing infrastructure and automating delivery.
14.1 Terraform and Infrastructure Testing in a DevOps Pipeline
Integrating Terraform into a DevOps pipeline ensures infrastructure is tested before deployment. Tools like Test Kitchen, terraform validate, and custom scripts can be used to validate Terraform configurations before applying changes.
Example of testing Terraform configuration:
| bash terraform validate |
This command checks your configuration for syntax errors, ensuring that it’s ready for deployment.
14.2 Infrastructure as Code in Continuous Delivery
Terraform supports continuous delivery by enabling the automated creation, modification, and destruction of infrastructure resources as part of a CI/CD pipeline. Tools like Jenkins, GitLab CI, and CircleCI can integrate with Terraform to provide automated infrastructure delivery.
15. Terraform Code Structuring and Scaling
As your Terraform codebase grows, proper structuring and management are essential for scalability, maintainability, and collaboration.
15.1 Terraform Code Structuring and Repository Layouts
A well-organized Terraform codebase is crucial for large projects. Structuring your code into modules, defining clear naming conventions, and separating code into directories for different environments are best practices for maintaining clarity.
| Example layout: css . ├── main.tf ├── variables.tf ├── outputs.tf └── modules/ ├── network/ ├── compute/ └── database/ |
15.2 Managing Multiple Environments in Terraform
Terraform’s workspace and module system help you manage multiple environments (dev, staging, production). By isolating configurations for each environment, you can prevent cross-environment issues.
16. Emerging Terraform Features
Terraform continues to evolve, with new features and integrations that enhance its capabilities for managing infrastructure at scale.
16.1 Terraform and the HashiCorp Ecosystem
Terraform integrates seamlessly with other HashiCorp tools like Consul, Vault, and Packer. These integrations allow you to manage service discovery, secret management, and infrastructure provisioning in a unified way.
Example of using Terraform with Vault:
| hcl provider "vault" {} resource "vault_generic_endpoint" "example" { path = "secret/data/example" data_json = jsonencode({ username = "admin" password = "secret" }) } |
16.2 The Future of Terraform (e.g., Terraform CDK)
The future of Terraform includes exciting new features like the Terraform Cloud Development Kit (CDK), which allows developers to use familiar programming languages (such as Python, Go, or JavaScript) to define infrastructure, expanding Terraform’s versatility and ease of use.
17. Serverless Infrastructure with Terraform
17.1 Managing Serverless Applications with Terraform
Serverless architectures are growing in popularity for their ability to simplify operations and reduce overhead by allowing developers to focus purely on code rather than server management. Terraform enables the seamless deployment and management of serverless resources like AWS Lambda, API Gateway, and DynamoDB.
Here’s how to use Terraform to manage serverless applications:
AWS Lambda: Terraform simplifies the deployment of Lambda functions. You can define your Lambda’s runtime, handler, and permissions in a .tf file to automate deployment.
| hcl resource "aws_lambda_function" "example_lambda" { filename = "function.zip" function_name = "example_lambda" role = aws_iam_role.lambda_exec.arn handler = "index.handler" runtime = "nodejs14.x" } |
- API Gateway: With Terraform, you can set up API Gateway, link it to Lambda functions, and configure routes. It automates the process of exposing Lambda functions to HTTP requests.
| hcl resource "aws_api_gateway_rest_api" "example_api" { name = "example_api" description = "API for Lambda function" } resource "aws_api_gateway_resource" "lambda_resource" { rest_api_id = aws_api_gateway_rest_api.example_api.id parent_id = aws_api_gateway_rest_api.example_api.root_resource_id path_part = "example" } resource "aws_api_gateway_method" "lambda_method" { rest_api_id = aws_api_gateway_rest_api.example_api.id resource_id = aws_api_gateway_resource.lambda_resource.id http_method = "GET" authorization = "NONE" } resource "aws_api_gateway_integration" "lambda_integration" { rest_api_id = aws_api_gateway_rest_api.example_api.id resource_id = aws_api_gateway_resource.lambda_resource.id http_method = aws_api_gateway_method.lambda_method.http_method integration_http_method = "POST" type = "AWS_PROXY" uri = "arn:aws:apigateway:${data.aws_region.current.name}:lambda:path/2015-03-31/functions/${aws_lambda_function.example_lambda.arn}/invocations" } |
- DynamoDB for Serverless Data Storage: Use DynamoDB to store and manage data in serverless applications. Terraform provides an easy way to manage tables, set up keys, and configure throughput.
| hcl Copy resource "aws_dynamodb_table" "example_table" { name = "example-table" hash_key = "id" read_capacity = 5 write_capacity = 5 attribute { name = "id" type = "S" } } |
- By using Terraform, these serverless resources can be deployed consistently, reducing human error and speeding up deployment cycles.
18. Cost Management with Terraform
18.1 Managing Cloud Costs with Terraform
Cost management is a crucial aspect of infrastructure management, especially when working with cloud providers like AWS. Terraform provides several mechanisms to optimize cloud spending by enforcing best practices and automating the lifecycle of resources.
Key strategies for managing cloud costs with Terraform:
Right-Sizing Resources: With Terraform, you can ensure that you provision the appropriate size of resources based on your requirements. For example, using the right EC2 instance type can significantly reduce costs.
| hcl resource "aws_instance" "example" { ami = "ami-0c55b159cbfafe1f0" instance_type = "t3.micro" # Use cost-effective instance types for non-critical workloads } |
- Auto-Scaling: Use AWS Auto Scaling to ensure that your resources scale based on demand, preventing you from overpaying during low-traffic periods.
| hcl resource "aws_autoscaling_group" "example" { desired_capacity = 2 max_size = 5 min_size = 1 launch_configuration = aws_launch_configuration.example.id vpc_zone_identifier = [aws_subnet.example.id] } |
- Automating Shutdown of Unused Resources: Terraform allows you to automate the shutdown of unused resources, saving costs during non-peak hours. For example, stopping non-critical EC2 instances at night.
Cost Allocation Tags: Terraform can manage cost allocation tags in AWS, enabling better tracking of resource usage and associated costs.
| hcl resource "aws_instance" "example" { ami = "ami-0c55b159cbfafe1f0" instance_type = "t2.micro" tags = { "Environment" = "Dev" "Owner" = "Team A" } } |
By following these best practices, you can ensure that your cloud infrastructure remains cost-efficient while maintaining high availability and performance.
19. Conclusion
19.1 Summary of Key Takeaways
In this blog, we’ve walked you through various aspects of using Terraform to automate and manage AWS infrastructure. Here are the key takeaways:
- Terraform Basics: You’ve learned the core concepts like providers, resources, modules, and variables, and how they are used to manage AWS resources.
- Advanced Features: We explored advanced techniques such as immutable infrastructure, managing state, and working with multiple environments using workspaces.
- Real-World Examples: You saw practical examples of deploying applications, managing multi-region AWS deployments, and automating serverless applications.
- Cost Management: We covered strategies for optimizing cloud costs using right-sizing, auto-scaling, and automating resource shutdowns.
- Future Trends: We also discussed Terraform’s future direction, including the Terraform CDK and integration with other HashiCorp tools.
By mastering these techniques, you can confidently use Terraform to build, deploy, and maintain scalable and cost-effective cloud infrastructure.
19.2 Looking Ahead: Terraform's Future with AWS
Looking ahead, Terraform will continue to evolve and expand, bringing more powerful features to streamline infrastructure management. Some trends to watch out for:
- Terraform Cloud Development Kit (CDK): This new tool is set to allow developers to define infrastructure using high-level programming languages like Python, TypeScript, and JavaScript, further extending Terraform’s capabilities.
- New AWS Services Support: As AWS continues to release new services, Terraform will likely add support for these, allowing you to manage them via Infrastructure as Code.
- Improved Cost and State Management: Expect to see even more advanced features for managing state files, collaborating with teams, and integrating cost optimization directly into Terraform workflows.
Terraform will remain an integral tool for developers and DevOps teams as it evolves to meet the needs of modern cloud infrastructure management.





