What Is Microsoft Sentinel?
Microsoft Sentinel is Microsoft's cloud-native security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution. Launched in 2019 (originally as Azure Sentinel), it represents Microsoft's answer to the growing need for comprehensive, integrated security monitoring at enterprise scale. Built on Azure's powerful infrastructure, Sentinel provides intelligent security analytics across your entire organization.
Unlike traditional security tools confined to specific environments, Microsoft Sentinel provides a comprehensive view of your entire enterprise, leveraging AI to detect, investigate, and respond to threats before they cause damage. It collects data from users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
Despite its powerful capabilities, many organizations struggle to leverage the potential of Microsoft Sentinel fully. This comprehensive blog bridges the gap between Sentinel's theoretical capabilities and practical implementation, providing concrete strategies, examples, and best practices for security professionals looking to enhance their security operations.
One Platform, Two Critical Functions
What makes Microsoft Sentinel stand out is how it unifies two major areas of security operations - SIEM and SOAR into a single cloud-native solution.
- Security Information and Event Management (SIEM) focuses on visibility and detection. It gathers and analyzes data from across the organization to identify potential security incidents, providing alerting and investigation tools.
- Security Orchestration, Automation, and Response (SOAR) adds automation and coordination. It enables teams to define response workflows, standardize investigation steps, and trigger actions across integrated tools.
Traditionally, organizations had to manage SIEM and SOAR with separate platforms, often leading to delays and inconsistent processes. Sentinel brings these together, reducing complexity and improving response time, especially during high-pressure investigations.
The Real Cost of Getting It Wrong
Security incidents affect more than just financial performance. According to IBM’s 2023 report, the global average cost of a data breach is $4.45 million, marking a 2.3% increase from 2022. Recent 2024 data shows this has now reached $4.88 million, the largest spike since the pandemic.
Loss of customer trust often follows a breach. In some industries, more than 30% of customers stop doing business with a company after a major security failure. Regulatory fines continue to rise. Under laws like GDPR, penalties can reach up to 4% of annual global revenue. Healthcare organizations also face fines under HIPAA, sometimes exceeding $1.5 million per breach.
Security events also disrupt operations. Systems may be taken offline to contain an attack, resulting in significant downtime. Manufacturing companies report hourly losses as high as $50,000, and financial institutions often lose even more during service interruptions.
Legal costs grow quickly due to lawsuits and regulatory investigations. These can last for years, requiring legal and executive attention that could otherwise support core business functions. Focus shifts from strategic growth to risk containment, reducing organizational momentum.
The Hidden Costs of Doing Nothing
Continuing to rely on outdated or fragmented security tools increases both visible and invisible risks. These legacy systems can’t keep pace with evolving threats and complex environments.
When security tools don’t share information, attackers can move between systems without being detected. The longer it takes to identify a breach, the more damage can occur. Teams often spend excessive time manually investigating disjointed alerts, increasing operational costs and diverting attention from strategic initiatives and threat hunting.
These inefficiencies also compromise compliance. Audits demand comprehensive monitoring, and gaps in visibility can lead to longer review processes and higher compliance costs.
Finally, lagging security capabilities delay innovation. Organizations with outdated systems are slower to adopt new technologies, putting them at a disadvantage compared to competitors with stronger, more modern security postures.
Why Organizations Are Rethinking Their Security Approach?
As more organizations move to the cloud and support remote work, the security landscape has shifted. Traditional security models, designed around fixed networks and on-premises systems, are no longer enough. Data now moves across multiple cloud platforms, devices, and networks, often outside the boundaries of traditional IT infrastructure.
Legacy systems often lack the visibility and agility needed to protect modern infrastructures. They were designed for static, on-premises environments and struggle to keep up with cloud-scale data, distributed users, and evolving attack techniques. This disconnect makes it difficult to detect threats early, respond effectively, or even understand what’s happening across the environment.
Security teams face growing pressure to manage more with less - fewer people, more alerts, and a wider attack surface.
Challenges in Traditional Security Monitoring
Legacy security tools were not built for the scale, speed, or complexity of cloud environments. They often focus on individual systems or specific layers of infrastructure, leading to inconsistent visibility. These limitations expose critical vulnerabilities:
- Incomplete visibility – Most legacy tools only monitor parts of the environment, leaving blind spots between cloud platforms, on-prem systems, and user devices
- Overwhelming alert volume – Security teams often receive thousands of alerts per day, many of which are false positives or low priority
- Slow investigation and response – Manual analysis across disconnected systems delays action and increases risk
- Poor scalability – On-premises SIEM systems can’t easily adapt to growing data volumes or new workloads
These challenges leave organizations vulnerable to advanced threats that move laterally across environments and exploit the gaps between monitoring systems.
Microsoft Sentinel: A Modern Security Solution
Microsoft Sentinel is built specifically to meet the demands of today’s cloud-first, data-heavy environments. It replaces fragmented tools with a single, integrated platform that delivers real-time insights, automated threat detection, and rapid response.
By connecting data from across your entire ecosystem, Microsoft services, third-party platforms, on-prem infrastructure, and multiple cloud environments, Sentinel gives security teams the clarity they need to act with confidence.
It helps organizations:
- Consolidate data into one view for faster detection and investigation
- Use AI and machine learning to identify suspicious behavior and reduce false positives
- Automate response actions to contain threats without delay
- Scale on demand without hardware or infrastructure limitations
Rather than reacting to incidents after the fact, Sentinel enables security teams to anticipate and neutralize threats before they cause damage. It lays the foundation for a more proactive, agile, and effective security operation.
A Closer Look at What Sentinel Offers
To move beyond limitations of traditional tools, security teams need more than just visibility—they need flexibility, intelligence, and automation. Microsoft Sentinel combines these into a single platform, delivering capabilities that help organizations detect threats early, respond quickly, and continuously adapt to a changing threat landscape.
Here are the key areas where Sentinel supports modern security operations:
- Data Collection – Sentinel connects with a wide range of sources—cloud services, on-prem systems, applications, and network devices—through built-in connectors and APIs. This helps security teams centralize data without relying on multiple tools.
- Threat Detection – It uses built-in analytics and machine learning to identify unusual activity, suspicious access patterns, and known attack behaviors across your digital estate.
- Threat Hunting – Sentinel equips analysts with tools to proactively search for threats, even before alerts are triggered. This helps uncover silent, slow-moving attacks.
- Incident Investigation – With visual timelines, contextual insights, and relationship mapping, Sentinel enables security teams to understand the scope and impact of incidents faster.
- Automated and Guided Response – Playbooks and automation rules help streamline response actions, reducing the time and effort required to contain threats.
- Threat Intelligence Integration – Sentinel brings in threat intelligence from Microsoft and third-party sources, enriching data with external context to strengthen detection accuracy.
Each of these capabilities contributes to a more proactive and efficient security operation, one that scales as your organization grows and adapts as threats evolve.
Practical Scenarios
Microsoft Sentinel is designed to address real-world threats across industries and environments. Here are a few practical use cases that show how it can be applied:
- Insider Threat Detection – Identify unusual user behavior, such as accessing sensitive data from unexpected locations or outside working hours.
- Advanced Persistent Threats (APT) – Detect subtle, long-term attacks involving lateral movement, privilege escalation, and coordinated infiltration.
- Cloud Security Monitoring – Monitor changes in configurations, access controls, and administrative actions across Azure, AWS, and other cloud services.
- IoT and Operational Technology (OT) Monitoring – Extend security visibility to critical industrial systems and smart devices, flagging unusual communication patterns or access attempts.
- Compliance and Audit Readiness – Track access to regulated data, generate reports, and support compliance with standards like GDPR, HIPAA, and ISO 27001.
These examples highlight how Sentinel adapts to various environments, helping organizations of all sizes strengthen their defenses and respond with confidence.
Exploring the Main Components
Microsoft Sentinel brings together a set of integrated tools designed to support every stage of the security lifecycle, from detection to response. Understanding these components helps security teams get the most out of the platform and tailor its capabilities to their specific needs.
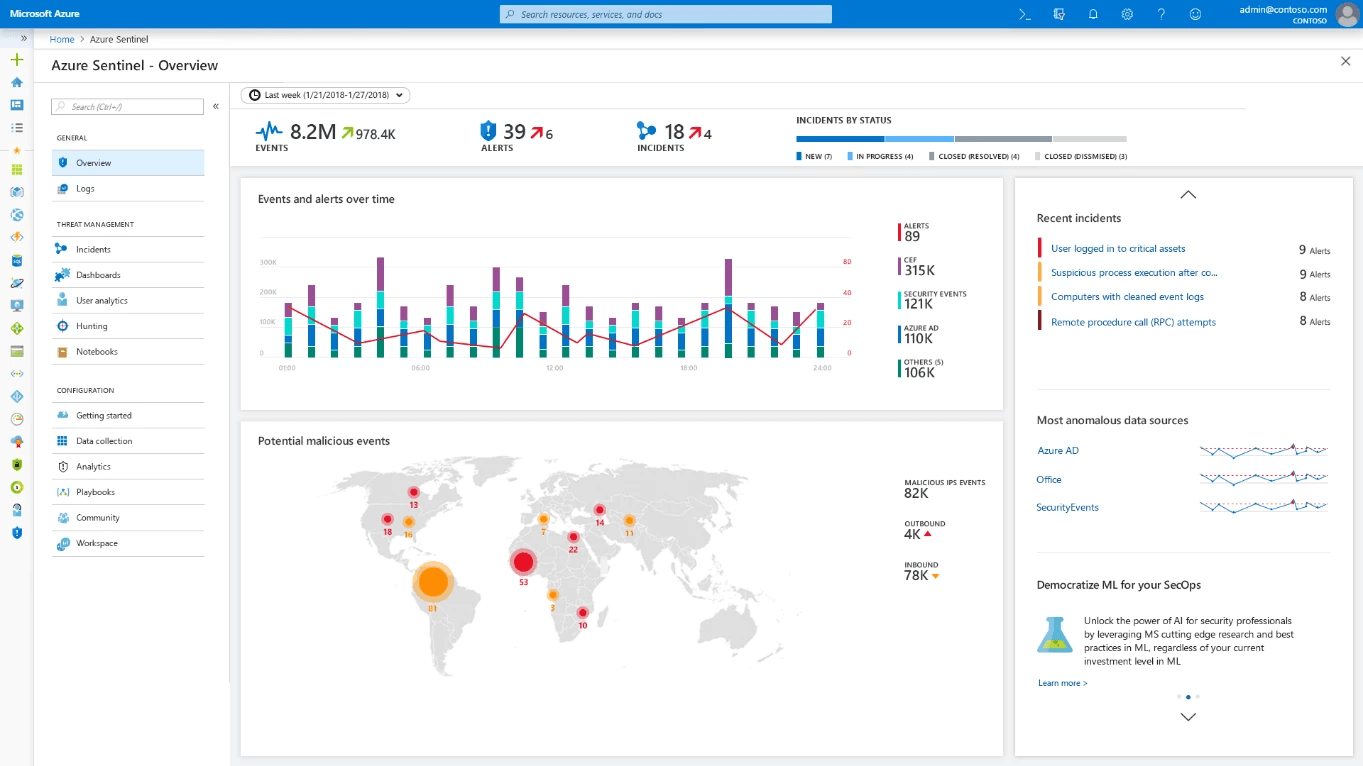
Source - Azure
Turning Data into Insight: Workbooks
Workbooks in Sentinel allow you to visualize and explore your security data through interactive dashboards. They help security teams identify trends, anomalies, and critical changes across their environment by making large volumes of data more accessible and actionable.
A well-designed workbook might show:
- Geographic login patterns to highlight suspicious access
- Time-series views of authentication failures or failed MFA challenges
- Correlated activity showing successful logins after repeated failures
While Microsoft provides several templates, the most value comes from tailoring workbooks to match your environment and priorities. By highlighting the metrics that matter most, customized workbooks support faster, more focused investigations.
Automated Detection with Analytics Rules
Analytics rules form the core of Sentinel's detection capabilities, continuously evaluating incoming data against defined patterns to identify potential threats. These rules enable organizations to detect security incidents automatically without constant manual monitoring.
Types of Analytics Rules:
- Scheduled Rules: Run KQL queries at defined intervals to detect specific patterns or conditions
- Microsoft Security Rules: Leverage Microsoft's security research with built-in rules for Microsoft products that are continuously updated by Microsoft threat intelligence
- Fusion Rules: Correlate signals across different products to identify complex attack patterns
- Machine Learning Rules: Identify anomalies without predefined patterns using behavioral analytics for user and entity activities
To ensure effectiveness, it’s important to balance detection depth with precision. Starting with high-fidelity rules, reviewing their performance regularly, and refining them over time helps reduce false positives and maintain alert quality.
Properly tuned analytics rules balance comprehensive coverage with operational efficiency, avoiding alert fatigue, which is a problem in many security operations. The goal is to create a detection system that catches real threats while maintaining manageable alert volumes.
Proactive Threat Hunting
While analytics rules provide automated detection, hunting queries enable security analysts to proactively search for threats that haven't triggered alerts. This proactive approach helps identify sophisticated attacks that might evade automated detection systems.
Hunting Process:
- Hypothesis Formation: Develop theories about potential attacker activities based on threat intelligence and environmental factors
- Query Development: Create KQL queries to test the hypothesis against your data
- Investigation: Analyze results to determine if they represent threats, bookmark interesting results, and create new analytics rules from effective hunting queries
- Iteration: Refine queries based on findings and evolving threat intelligence
Microsoft provides a threat hunting library aligned to the MITRE ATT&CK framework to help teams get started. Over time, building a consistent hunting routine strengthens your ability to detect subtle or novel threats that evade automated detection.
Building an Effective Hunting Program:
- Schedule regular hunting sessions focused on high-risk areas
- Document findings to build organizational knowledge
- Create a feedback loop between hunting and detection
- Leverage the community through GitHub and Sentinel repositories
The most effective security teams balance reactive monitoring with proactive hunting to stay ahead of sophisticated threats. This approach transforms security operations from purely reactive to strategically proactive.
Incidents – Investigating and Responding
When analytics rules detect potential threats, Sentinel groups related alerts into incidents, structured cases that guide investigation and response. Each incident includes timelines, affected entities, and context to help analysts understand what’s happening.
Incident Lifecycle:
- Creation: An incident is generated from one or more alerts
- Assignment: The incident is allocated to a security analyst
- Investigation: The analyst examines evidence and determines the scope
- Response: Actions are taken to address the threat
- Closure: The incident is classified and documented for future reference
Key tools like the incident graph, behavioral timelines, and evidence logs make it easier to connect events and uncover the root cause. Prioritization is also built in, using factors like asset sensitivity, known attack techniques, and threat intelligence.
Incident Prioritization: Sentinel uses several factors to help prioritize incidents, including MITRE ATT&CK tactics and techniques involved, number of affected entities, asset sensitivity, and related threat intelligence.
Best Practices:
- Record all investigation steps taken
- Document evidence found and its interpretation
- Note all remediation actions
- Classify incidents using a consistent taxonomy
Effective incident handling not only resolves immediate threats but also builds institutional knowledge that improves future security operations. This systematic approach ensures consistent investigation quality and enables continuous improvement of security processes.
Automating Response with Playbooks
Playbooks enable Sentinel to take immediate action when specific threats are identified. These automated workflows are built on Azure Logic Apps and can handle everything from basic notifications to complex remediation tasks. They represent pre-defined workflows that execute automatically when specific conditions are met.
Common playbook scenarios include:
- Enrichment Playbooks: Add context to incidents through IP address geolocation and reputation lookup, user information retrieval from Active Directory, and asset criticality classification
- Notification Playbooks: Alert stakeholders based on incident attributes by escalating critical incidents to senior team members, notifying asset owners about compromised resources, and updating relevant teams through Teams or Slack
- Remediation Playbooks: Take corrective action automatically, including resetting compromised credentials, isolating affected endpoints, blocking malicious IPs at the firewall, and disabling suspicious accounts
For example, a playbook responding to a compromised account might:
When triggered by an incident with a compromised account tag, the playbook executes these actions:
- Get user details from Azure AD
- If the user is privileged, send a high-priority alert to the SOC Slack channel and create a ServiceNow high-priority ticket
- Reset user password
- Disable any active sessions
- Add a comment to the incident with actions taken
As with any automation, careful design and testing are essential. Start with clear, narrowly scoped actions, include fallback steps for failures, and keep documentation up to date as your processes evolve.
Balancing automation with human oversight is critical. While playbooks excel at the consistent execution of established procedures, complex incidents still require human judgment and decision-making.
Making the Most of Automation
Automation is one of the most powerful ways to improve the efficiency and consistency of your security operations. However, not every task should be automated. Understanding where automation adds value and where it doesn't is critical to building a reliable and resilient system.
Where Automation Delivers the Most Value
Tasks that are repetitive, time-consuming, and consistent in execution are prime candidates for automation. These include routine data enrichment, evidence collection, and standardized notification workflows. Automating these processes saves time, reduces human error, and ensures consistent response quality.
For example, collecting reputation data for an IP address or retrieving user details from a directory service can be safely and effectively automated. Similarly, known-good remediation actions such as disabling compromised accounts or blocking malicious IPs can often be performed automatically under well-defined conditions.
Other areas, like generating reports or documenting actions taken during incident handling, also benefit from automation, freeing analysts to focus on more complex responsibilities.
When Human Oversight Remains Essential
Despite its benefits, automation has limitations. Certain decisions and actions still require human judgment, especially those involving context, ambiguity, or potential business impact.
Determining whether an alert is a true positive, conducting complex investigations across multiple systems, or making decisions that affect user access to critical services are tasks that demand human analysis. Public communications and strategic shifts in response to evolving threats are also areas where automation should not replace expert oversight.
Maturing Your Automation Approach
Organizations typically evolve through several stages of automation maturity:
- Manual – All actions handled by analysts
- Assisted – Tools support decisions, but execution is manual
- Semi-automated – Routine tasks are automated, critical steps remain manual
- Highly automated – Most workflows are automated, with humans in supervisory roles
- Autonomous – AI systems manage full processes with minimal oversight
Most organizations should aim for stage 3 or 4, maintaining human insight for critical decisions while eliminating mundane tasks. This approach maximizes efficiency while preserving the strategic value of human expertise.
Common Automation Scenarios with Sentinel
Sentinel uses Azure Logic Apps to enable flexible automation through playbooks. Here are a few practical examples that demonstrate how automation can be safely applied:
- Brute Force Attack Response:
When repeated authentication failures occur, the system checks whether the source IP belongs to your organization. If it's external and flagged as malicious by threat intelligence sources, the IP is added to a block list. Internal activity, by contrast, is flagged for investigation via a ServiceNow ticket, with all steps documented in the related incident. - Phishing Campaign Detection:
When multiple users report suspicious emails, automation extracts relevant indicators, such as sender, subject, or embedded links and scans all mailboxes for similar messages. Malicious emails are purged, indicators are sent to Defender for Office 365, and users are notified. - Unusual Sensitive Data Access:
If a user accesses sensitive resources outside of normal change windows or patterns, automation retrieves user context, checks historical behavior, and determines whether access should be escalated. In high-risk cases, access can be temporarily suspended pending review.
These workflows demonstrate how automation improves response times and reduces manual workload, while keeping critical decision points under human control.
To realize the full benefit of automation in Microsoft Sentinel, well-structured playbooks are essential. Poorly designed or insecure automation can introduce risks or operational complexity. The following principles outline how to design, manage, and secure playbooks for effective and safe automation.
Integrating Microsoft Sentinel Within the Broader Security Ecosystem
Microsoft Sentinel's true strength lies in how it connects with Microsoft's wider suite of security tools, creating a layered defense that covers every part of your environment. Leveraging these integrations helps you build a security strategy that is both comprehensive and efficient.
Key Defender Integrations
Microsoft Defender for Cloud
Formerly Azure Security Center, this service manages security posture and threat protection for Azure resources. With Sentinel, you gain unified incident views across cloud workloads and enriched context for faster investigations.
Microsoft Defender for Endpoint
This platform protects desktops, servers, and mobile devices. Sentinel’s integration delivers advanced endpoint telemetry, correlates incidents automatically, and can trigger endpoint response actions directly from Sentinel.
Microsoft Defender for Identity
Monitoring Active Directory, this tool detects identity-based attacks such as Pass-the-Hash and Kerberoasting. Sentinel enriches investigations with user entity data and connects activity from on-premises and cloud identities.
Microsoft Defender for Office 365
Protecting email and collaboration tools, this integration enables coordinated detection of phishing and other email threats, with automated response actions to contain attacks quickly.
Each Defender product provides specialized detection capabilities that complement Sentinel's broad visibility, creating a defense-in-depth security model that addresses multiple attack vectors simultaneously.
Using Microsoft 365 Defender with Sentinel
Microsoft 365 Defender brings extended detection and response (XDR) across endpoints, identities, email, and apps. When paired with Sentinel, it creates a powerful, unified security operations platform combining XDR’s deep detections with Sentinel’s customizable analytics and broader data ingestion.
- Incidents identified in Microsoft 365 Defender automatically appear in Sentinel, with investigation details synchronized both ways.
- Analysts can share queries between platforms, using similar query languages, enabling cross-product threat hunting and correlation.
- This integration allows organizations to use Microsoft 365 Defender for focused, Microsoft-specific threats while relying on Sentinel for wider visibility and integration of diverse data sources.
Organizations gain the most value when they use M365D for specialized detections while leveraging Sentinel for broader correlation and custom use cases. This approach maximizes the investment in both platforms.
Extending Monitoring Beyond Microsoft
While Microsoft Sentinel integrates seamlessly with Microsoft products, its value extends to multi-platform environments through extensive third-party integrations. This capability enables organizations to maintain comprehensive security monitoring regardless of their technology stack.
- Cloud Platforms
For organizations running workloads across multiple clouds, Sentinel supports deep integration with major providers like AWS and Google Cloud. By ingesting AWS CloudTrail and Google Cloud audit logs, Sentinel ensures you can track administrative changes and suspicious activities consistently across your entire cloud estate. Kubernetes monitoring adds visibility into containerized applications, which are increasingly targeted by attackers. Without these integrations, blind spots emerge that can allow attacks to go unnoticed.
- Security Solutions
Many organizations rely on best-of-breed security products from different vendors. Sentinel integrates with leading firewall and endpoint platforms such as Check Point, Palo Alto Networks, and CrowdStrike to consolidate threat telemetry in one place. This unified approach allows faster correlation of events, like linking a suspicious network connection with endpoint behavior, helping security teams detect complex attack patterns that siloed tools might miss.
- Identity and Application Services
Identity remains a critical attack vector, and Sentinel’s integration with identity providers like Okta and Duo strengthens detection of credential misuse or unusual access. Similarly, monitoring cloud applications such as Salesforce or DNS traffic through Cisco Umbrella enables earlier identification of phishing attempts or compromised accounts. Collecting this data centrally means alerts are more contextual and actionable.
- Custom and Legacy Data Sources
Every environment has unique components, and Sentinel’s flexible ingestion methods (CEF, Syslog, REST APIs, Azure Functions) allow you to bring in custom logs and legacy system data. This ensures that no part of your infrastructure is left unmonitored, providing a holistic security view and preventing attackers from exploiting gaps in visibility.
When implementing cross-platform monitoring, organizations should normalize data fields for consistent analysis, create cross-platform detection rules, establish entity mapping between systems, and document data source coverage and blind spots.
In addition to collecting data, this integrated method makes connections throughout your whole security environment, transforming distinct signals into insightful data. It empowers your security team to detect, investigate, and respond to threats faster and more effectively, regardless of where they originate.
Your First 90 Days with Microsoft Sentinel
A phased plan in the first 90 days helps you focus on what matters most early on, while setting the stage for future expansion.
Days 1–30: Start with the Essentials
The first month is about laying the groundwork and getting quick wins. Begin by connecting your core Microsoft environments - such as Microsoft 365, Azure AD, and Defender products. These integrations alone will give you visibility into user activity, cloud access, and common threats.
Use built-in detection rules to catch well-known attacks like suspicious logins or privilege misuse. These rules work out of the box and help your team respond faster while you’re still learning the platform.
Set up alerts so critical threats are brought to your attention without delay. At this stage, focus on the highest-priority scenarios and build confidence in your ability to respond effectively.
Days 31–60: Expand Coverage, Improve Efficiency
Once you’ve established a basic level of visibility, expand Sentinel’s reach to other parts of your environment. This could include cloud services, third-party security tools, or network infrastructure.
Begin using automation to reduce repetitive manual tasks. For example, when certain types of alerts are triggered, you can automatically collect supporting data or notify the right people. This helps reduce response time and keeps your team focused on meaningful work.
Introduce dashboards that show what’s happening across your environment in real time. These help your team prioritize and track trends more easily.
Days 61–90: Fine-Tune and Build for Scale
Now it’s time to optimize what you’ve built. Review your detections and alerts - are they useful? Are they too noisy? Refine the system so it shows you what matters and filters out what doesn’t.
Build stronger workflows for responding to common security events. This includes outlining roles, documenting processes, and automating repetitive steps with confidence.
Start thinking about long-term value. This could include integrating threat intelligence, planning for advanced detection techniques, or building reporting for compliance.
Key Metrics to Monitor
Metric | Why It Matters | How to Measure in Sentinel |
Mean Time to Detect (MTTD) | Measures the speed of detection | Incident creation timestamp vs. alert time |
Mean Time to Respond (MTTR) | Tracks resolution speed | Incident open-to-close time |
Alert-to-Incident Ratio | Evaluate rule efficiency | Number of alerts grouped into each incident |
Rule Effectiveness | Measures false positive reduction | % of incidents closed as True Positive |
Coverage Expansion | Tracks visibility growth | Number of connected data sources + workbook coverage |
Pitfalls to Avoid
- Skipping Source Prioritization: Connecting too many systems without purpose can lead to noisy alerts.
- Over-Automation Too Early: Avoid automatic blocking or deletions before building context and trust.
- Neglecting Tuning Cycles: Rules and thresholds must be reviewed often, especially in dynamic cloud environments.
- Poor Documentation: Future scaling depends on detailed runbooks, config baselines, and ownership tracking.
- Ignoring Threat Context: Use threat intelligence connectors and enrichments to build actionable alerts, not just detections.
Final Thought
This 90-day roadmap enables a phased, achievable deployment plan for Microsoft Sentinel. It allows your team to demonstrate early wins, refine detection and response, and lay the groundwork for future advanced capabilities. Whether you’re starting from scratch or transitioning from another SIEM, this structured approach ensures value and operational confidence without overextending resources.