Protecting your cloud from the top SaaS security risks can feel overwhelming, but understanding these threats is the first step. While SaaS offers countless benefits, it also exposes businesses to unique vulnerabilities that require proactive defense.
This blog will highlight the top 10 SaaS security risks, explain how they can impact your cloud environment, and offer practical solutions to safeguard your data.
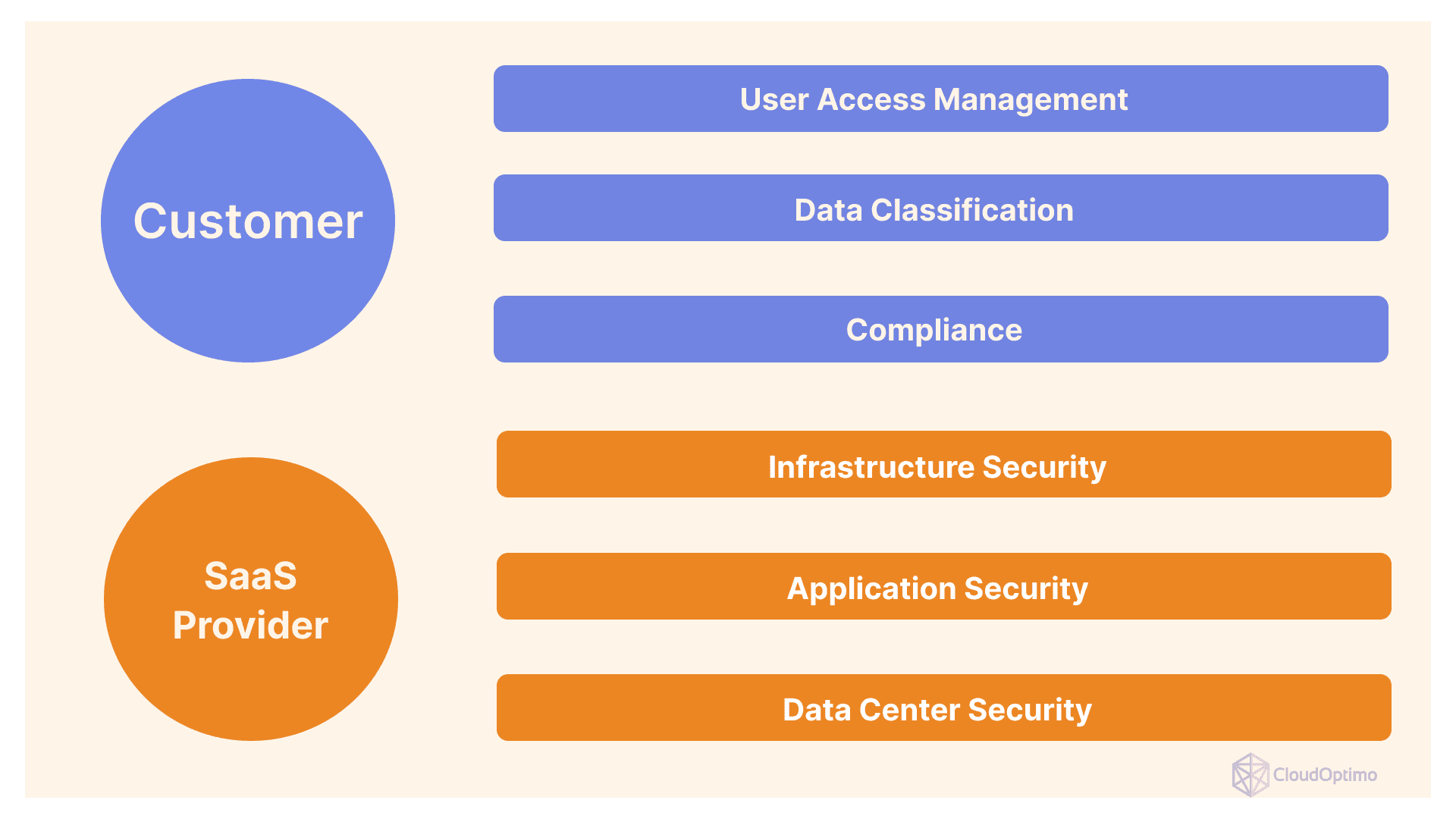
When it comes to SaaS security, it’s crucial to understand the shared responsibility model. While the SaaS provider manages infrastructure, updates, and certain security measures, businesses are responsible for securing their data, user access, and compliance.
To better understand the shared responsibility model in SaaS security, consider the following diagram:
The Growing Importance of SaaS Security
The SaaS market has experienced explosive growth in recent years. According to Gartner, the global SaaS market is projected to reach $675 billion by 2024. This rapid adoption brings with it an increased focus on security concerns.
Several factors contribute to the growing importance of SaaS security:
- Valuable Data: SaaS applications often handle sensitive business data, making them attractive targets for cybercriminals.
- Shared Responsibility: Security in SaaS is a shared responsibility between the vendor and the customer, requiring a clear understanding of roles.
- Compliance Requirements: Many industries have strict regulatory requirements for data protection and privacy.
- Interconnected Ecosystems: SaaS applications often integrate with other systems, expanding the potential attack surface.
- Remote Work Trends: The shift towards remote work has accelerated SaaS adoption, necessitating robust security measures.
Understanding and addressing SaaS security risks is crucial for organizations to protect their data, maintain customer trust, and ensure business continuity.
As we explore the most prevalent security risks associated with SaaS applications, it's important to note that these risks can vary in severity and impact depending on the specific SaaS solution and implementation.
Let's dive deeper into each risk and discuss potential mitigation strategies.
Common SaaS Security Risks
To provide a quick overview of the various SaaS security risks we'll be discussing, here's a comparison table:
| Risk | Potential Impact |
| Data Breaches | High |
| Insider Threats | High |
| Account Hijacking | High |
| Insecure APIs | High |
| Data Loss | High |
| Compliance Violations | High |
| Lack of Visibility and Control | Medium |
| Misconfiguration | High |
| Vendor Lock-in | Medium |
Now, let's explore each of these risks in detail, along with real-world examples and mitigation strategies.
Data Breaches
Data breaches are unauthorized access to sensitive information in SaaS applications, which can include customer data, financial information, or intellectual property.
Real-world example: In 2019, Capital One suffered a massive data breach affecting approximately 100 million individuals in the United States and Canada. The breach occurred due to a misconfigured web application firewall that enabled a hacker to access Capital One's AWS cloud server.
Potential attack vectors:
- Exploitation of vulnerabilities in the SaaS application
- SQL injection attacks
- Cross-site scripting (XSS) attacks
- Man-in-the-middle attacks
- Social engineering tactics targeting employees with access to sensitive data
Advanced mitigation strategies:
- Implement end-to-end encryption for sensitive data
- Use data tokenization for highly sensitive information
- Employ AI-powered anomaly detection systems to identify unusual data access patterns
- Conduct regular penetration testing and vulnerability assessments
- Implement a robust incident response plan with regular drills
Key Takeaways:
- Data breaches can have severe financial and reputational consequences
- Encryption, access controls, and regular security audits are crucial
- Employee training is essential to prevent social engineering attacks
Insider Threats
Insider threats involve the misuse of SaaS applications by individuals within the organization, either accidentally or maliciously.
Potential attack vectors:
- Accidental data leakage through improper handling of information
- Credential sharing among employees
- Social engineering targeting employees with high-level access
- Disgruntled employees with access to sensitive data
Advanced mitigation strategies:
- Implement User and Entity Behavior Analytics (UEBA) to detect anomalous user activities
- Use Privileged Access Management (PAM) solutions to control and monitor high-level access
- Implement data loss prevention (DLP) tools with content-aware policies
- Conduct regular security awareness training with simulated phishing exercises
- Implement a zero-trust security model
Key Takeaways:
- Insider threats can be both intentional and unintentional
- Monitoring user behavior and implementing least privilege access are crucial
- Regular security training and clear policies can help mitigate risks
- As we move on to discuss account hijacking, it's important to note that while insider threats and data breaches often originate from within an organization, account hijacking typically involves external actors attempting to gain unauthorized access to SaaS accounts.
Account Hijacking
Account hijacking occurs when an unauthorized party gains access to a user's SaaS account, often through stolen credentials or exploiting vulnerabilities in the authentication process.
Real-world example: In 2016, Uber suffered a data breach affecting 57 million users. The attackers gained access to a private GitHub repository used by Uber software engineers and used the credentials stored there to access Uber's AWS accounts.
Potential attack vectors:
- Credential stuffing attacks using leaked passwords from other breaches
- Phishing campaigns targeting users with fake login pages
- Brute-force attacks on weak passwords
- Session hijacking through man-in-the-middle attacks
- Exploitation of password reset mechanisms
Advanced mitigation strategies:
- Implement adaptive multi-factor authentication (MFA) that adjusts based on risk factors
- Use passwordless authentication methods, such as biometrics or hardware tokens
- Employ continuous authentication techniques to verify user identity throughout the session
- Implement robust password policies, including password complexity requirements and regular password rotations
- Use machine learning algorithms to detect and prevent anomalous login attempts
Here's a diagram illustrating a multi-layered approach to prevent account hijacking:
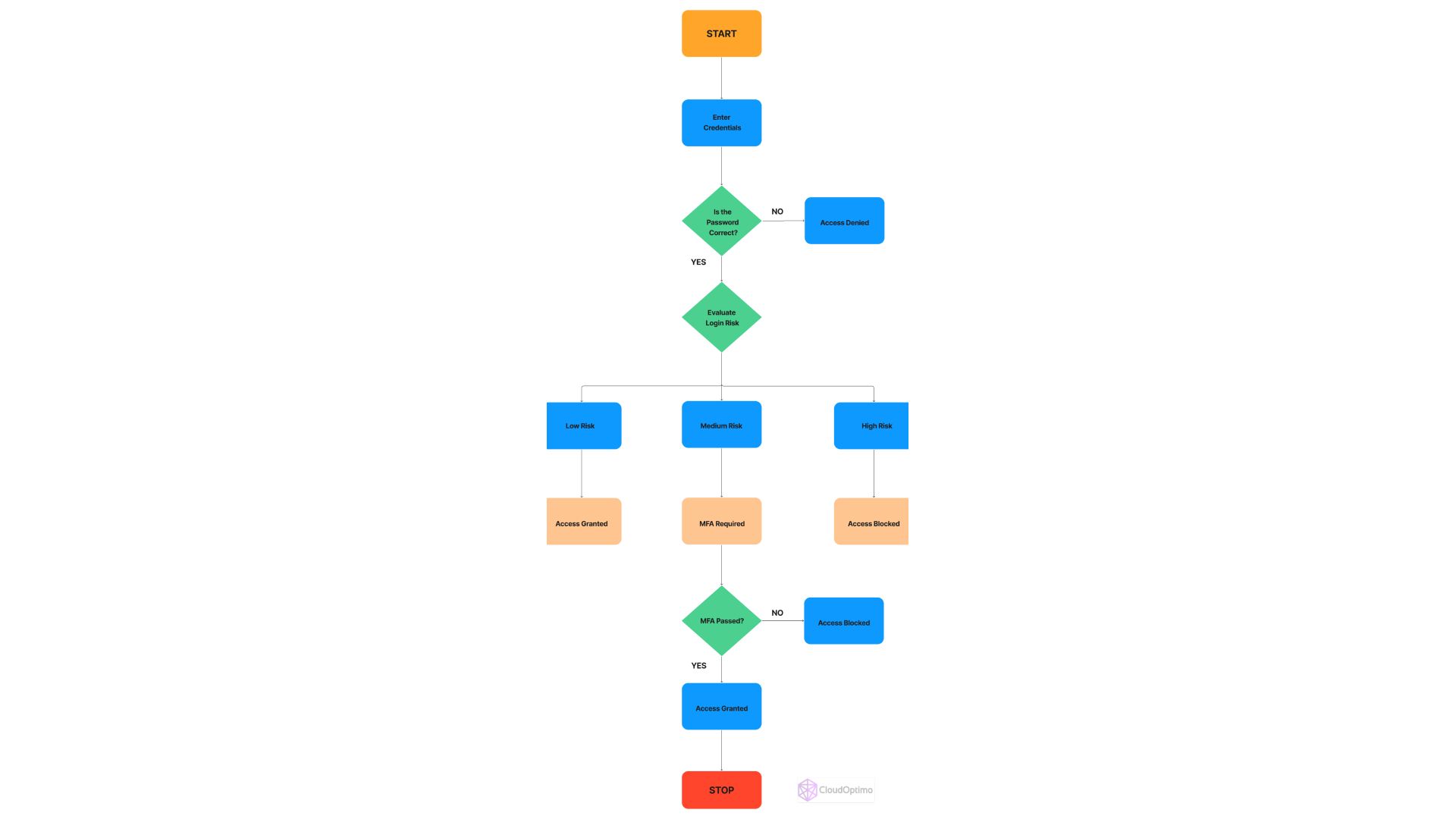
- Key Takeaways:
- Strong authentication mechanisms are crucial to prevent account hijacking
- Multi-factor authentication significantly reduces the risk of unauthorized access
- Continuous monitoring and risk-based authentication enhance security
Insecure APIs
APIs (Application Programming Interfaces) can become a point of vulnerability if not properly secured, potentially allowing attackers to access or manipulate data.
Potential attack vectors:
- Lack of proper authentication and authorization in API endpoints
- Injection attacks (e.g., SQL injection, XML injection)
- Parameter tampering to access unauthorized data
- API rate limiting bypass to perform large-scale data harvesting
- Man-in-the-middle attacks on unsecured API communications
Advanced mitigation strategies:
- Implement OAuth 2.0 with OpenID Connect for secure API authentication and authorization
- Use JSON Web Tokens (JWT) for stateless authentication
- Implement API gateways for centralized security policy enforcement
- Employ AI-powered API behavior analysis to detect anomalies
- Use API security testing tools to identify vulnerabilities in API implementations
Here's an example of securing an API endpoint using OAuth 2.0 and JWT in Python with the Flask framework:
| from flask import Flask, request, jsonify from flask_jwt_extended import JWTManager, jwt_required, create_access_token, get_jwt_identity from functools import wraps import os app = Flask(__name__) app.config['JWT_SECRET_KEY'] = os.environ.get('JWT_SECRET_KEY') jwt = JWTManager(app) def admin_required(fn): @wraps(fn) def wrapper(*args, **kwargs): current_user = get_jwt_identity() if current_user.get('role') != 'admin': return jsonify({"msg": "Admin access required"}), 403 return fn(*args, **kwargs) return wrapper @app.route('/login', methods=['POST']) def login(): username = request.json.get('username', None) password = request.json.get('password', None) # Validate credentials (replace with your actual authentication logic) if username != 'admin' or password != 'secretpassword': return jsonify({"msg": "Bad username or password"}), 401 access_token = create_access_token(identity={'username': username, 'role': 'admin'}) return jsonify(access_token=access_token), 200 @app.route('/api/sensitive-data', methods=['GET']) @jwt_required @admin_required def get_sensitive_data(): # Your sensitive data logic here return jsonify({"sensitive_data": "This is sensitive information"}), 200 if __name__ == '__main__': app.run(ssl_context='adhoc') # Use HTTPS in production |
This example demonstrates:
- JWT-based authentication
- Role-based access control
- HTTPS enforcement
- Separation of authentication and authorization logic
Key Takeaways:
- Properly securing APIs is crucial for protecting data in SaaS applications
- Use industry-standard authentication and authorization protocols
- Regularly test and monitor API security
As we transition to discussing data loss, it's important to note that while insecure APIs can lead to unauthorized data access, data loss often involves the unintentional destruction or corruption of data within the SaaS environment.
Data Loss
Data loss in SaaS environments can occur due to various reasons, including accidental deletion, hardware failures, malicious actions, or data corruption during synchronization.
Real-world example: In 2019, Myspace announced that it had lost all music uploaded to its site before 2015 during a server migration, affecting up to 50 million songs from 14 million artists.
Potential causes:
- Hardware failures in the SaaS provider's infrastructure
- Malware or ransomware attacks
- Data corruption during migration or synchronization processes
- Natural disasters affecting data centers
- Accidental deletion by users or administrators
Advanced mitigation strategies:
- Implement a comprehensive backup and disaster recovery plan
- Use versioning and recycle bin features provided by the SaaS application
- Employ third-party backup solutions specifically designed for SaaS data
- Implement data loss prevention (DLP) tools to prevent accidental data leakage
- Use blockchain technology to create immutable audit trails of critical data changes
Key Takeaways:
- Regular backups and disaster recovery planning are essential
- Use multiple data protection mechanisms for comprehensive coverage
- Encrypt data at rest and in transit to prevent unauthorized access in case of a breach
Compliance Violations
Compliance violations in SaaS environments can lead to severe legal and financial consequences, especially in industries with strict regulatory requirements.
Potential compliance standards:
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI DSS)
- California Consumer Privacy Act (CCPA)
- Sarbanes-Oxley Act (SOX)
Advanced mitigation strategies:
- Conduct regular compliance audits and risk assessments
- Implement data classification and governance policies
- Use compliance management software like CloudOptimo’s OptimoSecurity to track and manage compliance requirements
- Employ data discovery and mapping tools to understand data flows and storage locations
- Implement privacy-enhancing technologies (PETs) such as homomorphic encryption for sensitive data processing
- Key Takeaways:
- Understand the specific compliance requirements for your industry and region
- Regularly review and update compliance policies and procedures
- Invest in compliance management tools and expertise
- As we move on to discuss the lack of visibility and control in SaaS environments, it's important to note that this challenge often compounds the difficulty of maintaining compliance and preventing data loss.
Lack of Visibility and Control
The distributed nature of SaaS applications can lead to reduced visibility and control over data and user activities, making it challenging to maintain security and compliance.
Real-world example: In 2020, Zoom faced criticism for routing some calls through China and for claiming to offer end-to-end encryption when it did not. This highlighted the importance of transparency and control in SaaS applications, especially for sensitive communications.
Challenges:
- Limited access to infrastructure logs and security events
- Difficulty in tracking data movement and access across multiple SaaS applications
- Lack of control over the underlying infrastructure and security measures
- Reduced visibility into user activities and potential insider threats
- Challenges in conducting thorough security assessments and audits
Advanced mitigation strategies:
- Implement Cloud Access Security Brokers (CASBs) for centralized visibility and control
- Use Security Information and Event Management (SIEM) solutions to aggregate and analyze logs
- Employ User and Entity Behavior Analytics (UEBA) to detect anomalous activities
- Implement a zero-trust security model with continuous authentication and authorization
- Use API security and management tools to monitor and control data flows between applications
Key Takeaways:
- Invest in tools that provide centralized visibility across multiple SaaS applications
- Implement continuous monitoring and analytics to detect security incidents
- Establish clear policies and procedures for data access and user activity monitoring
Misconfiguration
Misconfigurations in SaaS applications can lead to security vulnerabilities, data exposure, and compliance violations.
Common misconfigurations:
- Overly permissive access controls
- Insecure default settings
- Incorrect network configurations
- Unencrypted data storage
- Inadequate logging and monitoring settings
Advanced mitigation strategies:
- Implement Infrastructure-as-code (IaC) practices to ensure consistent and secure configurations
- Use configuration management tools with built-in security checks
- Employ cloud security posture management (CSPM) solutions like CloudOptimo’s OptimoSecurity for continuous monitoring and remediation
- Implement least privilege access controls and regularly review permissions
- Conduct regular configuration audits and vulnerability assessments
- Key Takeaways:
- Regularly review and update SaaS configurations
- Use automation to ensure consistent and secure configurations
- Implement the principle of least privilege for all access controls
Vendor Lock-In
Vendor lock-in can pose security risks by limiting an organization's ability to switch providers or implement additional security measures.
Real-world example: In 2020, many organizations using Zoom for video conferencing faced challenges when trying to implement additional security measures or switch to alternative providers due to deep integration with Zoom's proprietary systems.
Security implications:
- Difficulty in data migration and potential data loss during transitions
- Limited ability to implement custom security measures
- Dependence on the vendor's security practices and update schedules
- Potential service disruptions if the vendor faces issues or goes out of business
Advanced mitigation strategies:
- Develop a multi-cloud or hybrid cloud strategy to reduce dependence on a single vendor
- Use open standards and APIs where possible to ensure interoperability
- Implement data portability measures, including regular data exports and backups
- Conduct thorough vendor assessments before committing to a SaaS solution
- Negotiate favorable contract terms, including data ownership and exit clauses
Key Takeaways:
- Consider vendor lock-in risks when selecting SaaS providers
- Maintain data portability to ensure flexibility in changing providers
- Use open standards and APIs to reduce dependence on proprietary systems
Shadow IT
Shadow IT refers to the use of unauthorized SaaS applications by employees, which can introduce significant security risks.
Associated risks:
- Uncontrolled data sharing and potential data leakage
- Lack of visibility into data processing and storage
- Compliance violations due to unauthorized data handling
- Increased attack surface due to unmanaged applications
Advanced mitigation strategies:
- Implement Cloud Access Security Brokers (CASBs) to detect and manage shadow IT
- Use Data Loss Prevention (DLP) tools to monitor and control data flows
- Develop and enforce clear policies on SaaS application usage
- Provide a streamlined process for requesting and approving new tools
- Conduct regular security awareness training on the risks of shadow IT
Here's a diagram illustrating a comprehensive shadow IT management strategy:

- Key Takeaways:
- Implement tools to detect and manage shadow IT
- Develop clear policies and educate employees on SaaS usage
- Provide a streamlined process for requesting new applications
SaaS Security Vulnerabilities
Let's explore some specific vulnerabilities that can affect SaaS applications and how to address them.
Cross-Site Scripting (XSS)
XSS attacks involve injecting malicious scripts into web applications, which are then executed in the user's browser. In SaaS applications, XSS can lead to session hijacking, data theft, or defacement of the application.
Prevention techniques:
- Implement proper input validation and output encoding
- Use Content Security Policy (CSP) headers
- Employ framework-specific XSS protection features
- Regularly scan for and patch XSS vulnerabilities
Example of a reflected XSS vulnerability:
| #!/bin/bash # Function to escape HTML characters escape_html() { echo "$1" | sed 's/&/\&/g; s/</\</g; s/>/\>/g; s/"/\"/g; s/'"'"'/\'/g' } # Simulating an incoming query query_string="$1" # If no query is provided if [ -z "$query_string" ]; then echo "Please provide a query string." exit 1 fi # Escaping HTML characters from the query escaped_query=$(escape_html "$query_string") # Simulating the response echo "Search results for: $escaped_query" |
SQL Injection
SQL injection attacks can allow attackers to manipulate database queries, potentially leading to unauthorized data access or modification.
Prevention techniques:
- Use parameterized queries or prepared statements
- Implement proper input validation and sanitization
- Apply the principle of least privilege to database accounts
- Regularly update and patch database management systems
Example of preventing SQL injection:
| # Vulnerable code cursor.execute("SELECT * FROM users WHERE username = '" + username + "'") # Secure code using parameterized query cursor.execute("SELECT * FROM users WHERE username = ?", (username,)) |
CSRF (Cross-Site Request Forgery)
CSRF attacks trick users into performing unintended actions on a web application where they're authenticated. This can lead to unauthorized transactions or data modifications.
Prevention techniques:
- Implement anti-CSRF tokens in forms and AJAX requests
- Use SameSite cookie attribute
- Verify the Origin and Referer headers for sensitive actions
- Implement proper session management
Example of CSRF protection using a token:
| from flask import Flask, session, request from flask_wtf.csrf import CSRFProtect app = Flask(__name__) csrf = CSRFProtect(app) @app.route('/transfer', methods=['POST']) @csrf.exempt def transfer_funds(): if request.form['csrf_token'] != session['csrf_token']: abort(403) # Process the transfer |
Broken Authentication
Weak authentication mechanisms can lead to account compromise and unauthorized access to sensitive data.
Prevention techniques:
- Implement multi-factor authentication
- Use secure session management practices
- Enforce strong password policies
- Implement account lockout mechanisms
Example of implementing multi-factor authentication:
| from flask import Flask, session, request from pyotp import TOTP app = Flask(__name__) @app.route('/login', methods=['POST']) def login(): username = request.form['username'] password = request.form['password'] totp_code = request.form['totp_code'] if authenticate_user(username, password): if verify_totp(username, totp_code): session['authenticated'] = True return "Login successful" return "Login failed" def verify_totp(username, totp_code): user_secret = get_user_totp_secret(username) totp = TOTP(user_secret) return totp.verify(totp_code) |
Sensitive Data Exposure
Improper handling of sensitive data can lead to unauthorized access or data breaches.
Prevention techniques:
- Encrypt sensitive data at rest and in transit
- Implement proper key management practices
- Use secure protocols for data transmission (e.g., TLS 1.3)
- Apply data masking techniques for sensitive information
- Implement proper access controls and auditing
Example of implementing encryption for sensitive data:
| from cryptography.fernet import Fernet def encrypt_sensitive_data(data): key = Fernet.generate_key() f = Fernet(key) encrypted_data = f.encrypt(data.encode()) return encrypted_data, key def decrypt_sensitive_data(encrypted_data, key): f = Fernet(key) decrypted_data = f.decrypt(encrypted_data).decode() return decrypted_data # Usage sensitive_info = "This is sensitive information" encrypted, key = encrypt_sensitive_data(sensitive_info) # Store encrypted data and key securely # When needed decrypted = decrypt_sensitive_data(encrypted, key) |
Best Practices for SaaS Security
Now that we've explored the various security risks and vulnerabilities associated with SaaS applications, let's discuss best practices for both organizations and end-users to enhance their SaaS security posture.
For Organizations
- Implement a Robust Identity and Access Management (IAM) Strategy
- Use Single Sign-On (SSO) solutions to centralize authentication
- Enforce multi-factor authentication (MFA) for all users
- Regularly review and audit user access privileges
- Implement role-based access control (RBAC) to ensure least privilege
- Develop a Comprehensive SaaS Governance Policy
- Create guidelines for SaaS application selection and adoption
- Establish processes for security assessments of new SaaS providers
- Define data classification and handling procedures for SaaS applications
- Regularly review and update the governance policy
- Enhance Visibility and Monitoring
- Implement Cloud Access Security Brokers (CASBs) for centralized visibility
- Use Security Information and Event Management (SIEM) solutions
- Set up alerts for suspicious activities or policy violations
- Conduct regular security audits and penetration testing
- Ensure Data Protection and Privacy
- Encrypt sensitive data both at rest and in transit
- Implement data loss prevention (DLP) tools
- Regularly backup critical data and test restoration procedures
- Ensure compliance with relevant data protection regulations (e.g., GDPR, CCPA)
- Foster a Security-Aware Culture
- Provide regular security awareness training for all employees
- Educate users on the risks of shadow IT and the importance of following security policies
- Encourage reporting of suspicious activities or potential security incidents
- Conduct simulated phishing exercises to test and improve user awareness
- Establish Incident Response and Business Continuity Plans
- Develop and regularly update incident response procedures
- Conduct tabletop exercises to test response capabilities
- Establish clear communication channels for reporting and managing security incidents
- Create and maintain business continuity and disaster recovery plans
- Manage Third-Party Risk
- Conduct thorough due diligence on SaaS providers
- Regularly review SaaS providers' security practices and certifications
- Include security and compliance requirements in contracts with SaaS providers
- Implement a vendor risk management program
- Secure API Integrations
- Use secure authentication methods for API access (e.g., OAuth 2.0, API keys)
- Implement proper error handling to prevent information leakage
- Monitor API usage for unusual patterns or potential abuse
- Regularly update and patch API endpoints
For End-Users
- Practice Good Password Hygiene
- Use strong, unique passwords for each SaaS application
- Consider using a password manager to generate and store complex passwords
- Never share passwords or use easily guessable information
- Enable Multi-Factor Authentication
- Activate MFA on all SaaS accounts that support it
- Use app-based authenticators or hardware tokens instead of SMS-based MFA when possible
- Be Cautious with Third-Party Integrations
- Only grant necessary permissions when connecting third-party apps to your SaaS accounts
- Regularly review and revoke access for unused or unnecessary integrations
- Stay Vigilant Against Phishing Attempts
- Be skeptical of unsolicited emails or messages asking for login credentials
- Verify the authenticity of login pages before entering credentials
- Report suspicious emails or activities to your IT department
- Keep Devices and Software Updated
- Regularly update your operating system, browsers, and other software
- Use reputable antivirus software and keep it up to date
- Be Mindful of Public Wi-Fi Usage
- Avoid accessing sensitive SaaS applications on public Wi-Fi networks
- Use a VPN when connecting to public networks if necessary
- Follow Data Handling Guidelines
- Adhere to your organization's data classification and handling policies
- Be cautious when sharing sensitive information through SaaS applications
- Report Security Concerns Promptly
- If you suspect a security breach or notice suspicious activity, report it immediately to your IT department or the SaaS provider's support team
The Future of SaaS Security
As SaaS adoption continues to grow and evolve, so too will the security landscape surrounding it. Here are some trends and developments we can expect to see in the future of SaaS security:
- AI and Machine Learning Integration
- Advanced threat detection using AI-powered analytics
- Automated response to security incidents
- Predictive security measures based on user behavior analysis
- Zero Trust Architecture
- Shift towards a "never trust, always verify" approach
- Continuous authentication and authorization for all users and devices
- Microsegmentation of networks and applications
- Increased Focus on Privacy
- More stringent data protection regulations globally
- Privacy-enhancing technologies becoming standard in SaaS applications
- Greater emphasis on data sovereignty and localization
- Edge Computing and SaaS
- Integration of edge computing with SaaS for improved performance and security
- Distributed security measures to protect data at the edge
- Blockchain for Enhanced Security
- Use of blockchain technology for secure, decentralized identity management
- Immutable audit trails for critical transactions and data changes
- DevSecOps Integration
- Tighter integration of security practices into the development lifecycle of SaaS applications
- Automated security testing and vulnerability scanning in CI/CD pipelines
- Unified Security Platforms
- Convergence of various security tools (CASB, SIEM, DLP, etc.) into unified platforms
- Improved orchestration and automation of security processes
- IoT and SaaS Security Convergence
- Addressing security challenges arising from the integration of IoT devices with SaaS applications
- Development of specialized security measures for IoT-enabled SaaS solutions
As these trends unfold, organizations and individuals must stay informed and adapt their security strategies accordingly to protect their data and systems in the ever-evolving SaaS landscape.
FAQs
Q: How often should we conduct security assessments of our SaaS providers?
A: It's recommended to conduct thorough assessments annually, with continuous monitoring in between. However, the frequency may vary based on the criticality of the data and services provided.
Q: What's the difference between encryption and tokenization in SaaS security?
A: Encryption transforms data into an unreadable format using an encryption key, while tokenization replaces sensitive data with non-sensitive tokens. Tokenization can be more secure for certain types of data as the original data is stored separately.
Q: How can we ensure compliance when using multiple SaaS providers?
A: Implement a centralized compliance management system, conduct regular audits, use Cloud Access Security Brokers (CASBs) for visibility, and ensure clear data classification and handling policies across all providers.
Q: What are the security implications of integrating multiple SaaS applications?
A: Integration can increase the attack surface and complexity of the environment. Ensure secure API usage, implement proper access controls, monitor data flows between applications, and regularly review integration configurations.
Q: How can we balance security and user experience in SaaS applications?
A: Focus on user-friendly security measures like Single Sign-On (SSO), risk-based authentication, and clear security policies. Provide regular training to help users understand the importance of security measures.