1. What is IAM and Why It Matters
Source: Matrix-iot
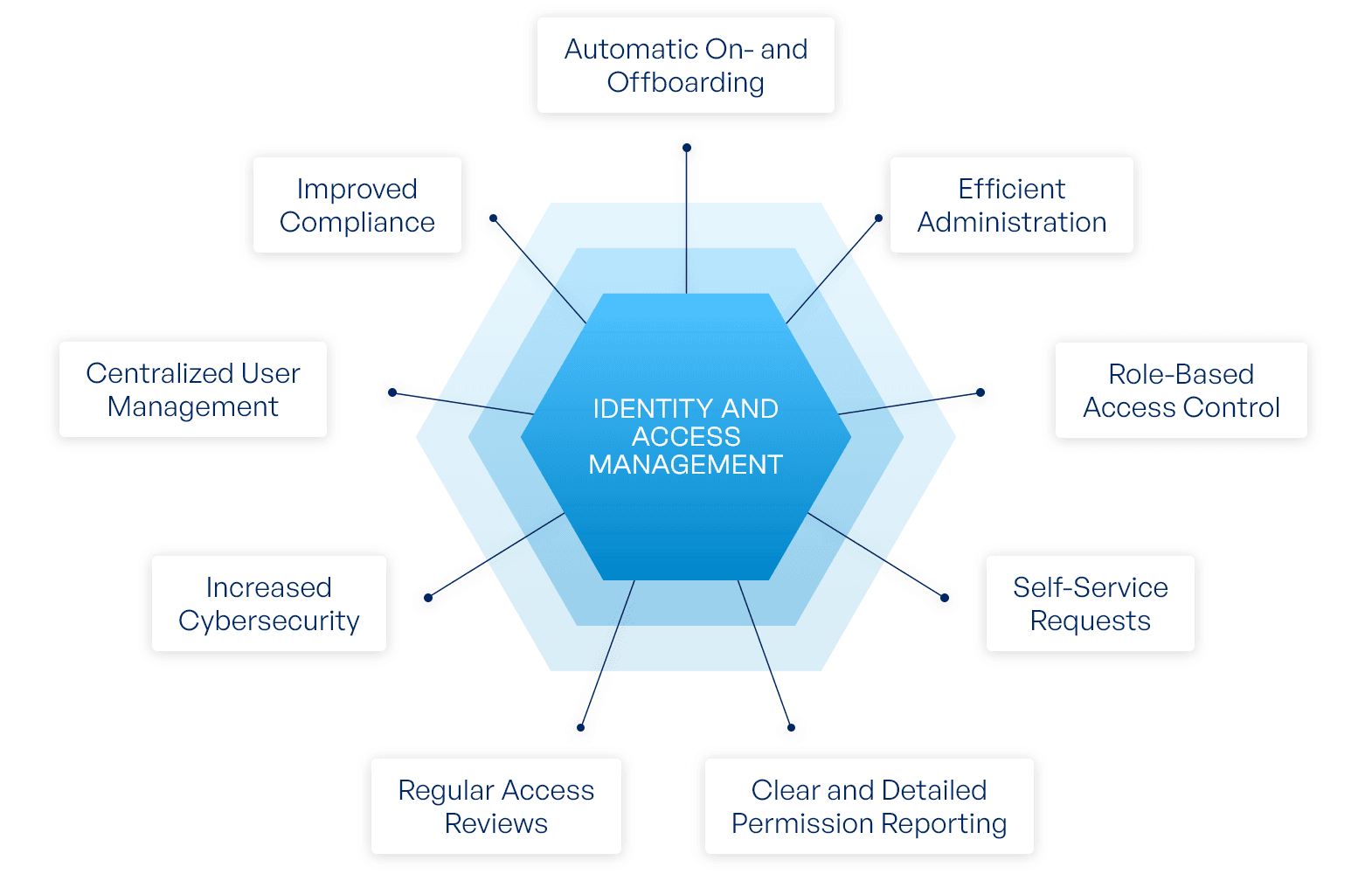
In today’s digital landscape, organizations rely heavily on cloud services to store data, deploy applications, and manage infrastructure. With this increasing reliance comes the critical need to control who has access to what within these environments—this is where Identity and Access Management (IAM) plays a foundational role.
IAM refers to the framework of technologies, policies, and processes used to manage digital identities and regulate user access to resources. At its core, IAM ensures that the right individuals and services have the appropriate access to the right resources, at the right time, and for the right reasons.
1.1. Why IAM Is Essential:
- Security: Prevents unauthorized access to sensitive data and critical services.
- Operational Efficiency: Streamlines onboarding/offboarding and access control across teams and services.
- Compliance: Helps meet regulatory and audit requirements by enforcing access policies.
- Scalability: Supports growing infrastructures without compromising security or agility.
Whether you're a startup or a large enterprise, IAM is not just a best practice—it's a necessity for secure cloud operations.
Now that we've covered the fundamentals of IAM, it's time to explore how these principles are implemented in Google Cloud Platform (GCP). Google Cloud IAM provides a flexible, granular, and highly integrated way to manage access across all GCP services.
In the next section, we’ll begin with an introduction to Google Cloud IAM, its purpose, and how it fits into GCP's broader security model.
2. Introduction to Google Cloud IAM
2.1 What is IAM in Google Cloud?
Google Cloud Identity and Access Management (IAM) is the framework used to define and enforce access control policies across Google Cloud services. It determines who can take what action on which resource, offering a centralized way to manage permissions across the cloud environment.
IAM ensures that only authorized users and services have the appropriate levels of access, supporting both security and operational efficiency. Rather than managing access individually at the resource level, IAM allows organizations to apply consistent policies across multiple resources from a central point.
2.2 Why Role Management Matters
Effective role management is critical in maintaining a secure and efficient cloud environment. Assigning excessive permissions can lead to serious security vulnerabilities, while overly restrictive access can disrupt workflows and development processes.
Properly defined roles:
- Enforce the principle of least privilege, limiting access strictly to what is needed.
- Support operational efficiency without unnecessary barriers.
- Simplify compliance with security standards and regulatory requirements.
In environments where resources and teams scale rapidly, precise role management reduces operational risks and maintains security posture.
3. Core Concepts of Google Cloud IAM
IAM is built on four foundational components: Principals, Resources, Permissions, and Policies.
3.1 Principals: Who Can Access
A Principal is an identity that requests access to a Google Cloud resource. Principals can include individual users, groups, service accounts, or entire domains.
| Principal Type | Example |
| User | user:[email protected] |
| Group | group:[email protected] |
| Service Account | serviceAccount:[email protected] |
| Google Workspace Domain | domain:example.com |
Service accounts are essential for providing secure, automated access by applications and services without human intervention.
3.2 Resources: What Can Be Accessed
A Resource represents any entity within Google Cloud that can be configured, managed, or accessed.
| Resource Type | Examples |
| Compute | VM Instances, Kubernetes Clusters |
| Storage | Buckets, Objects |
| Databases | BigQuery Datasets, Cloud SQL |
| Networking | VPC Networks, Load Balancers |
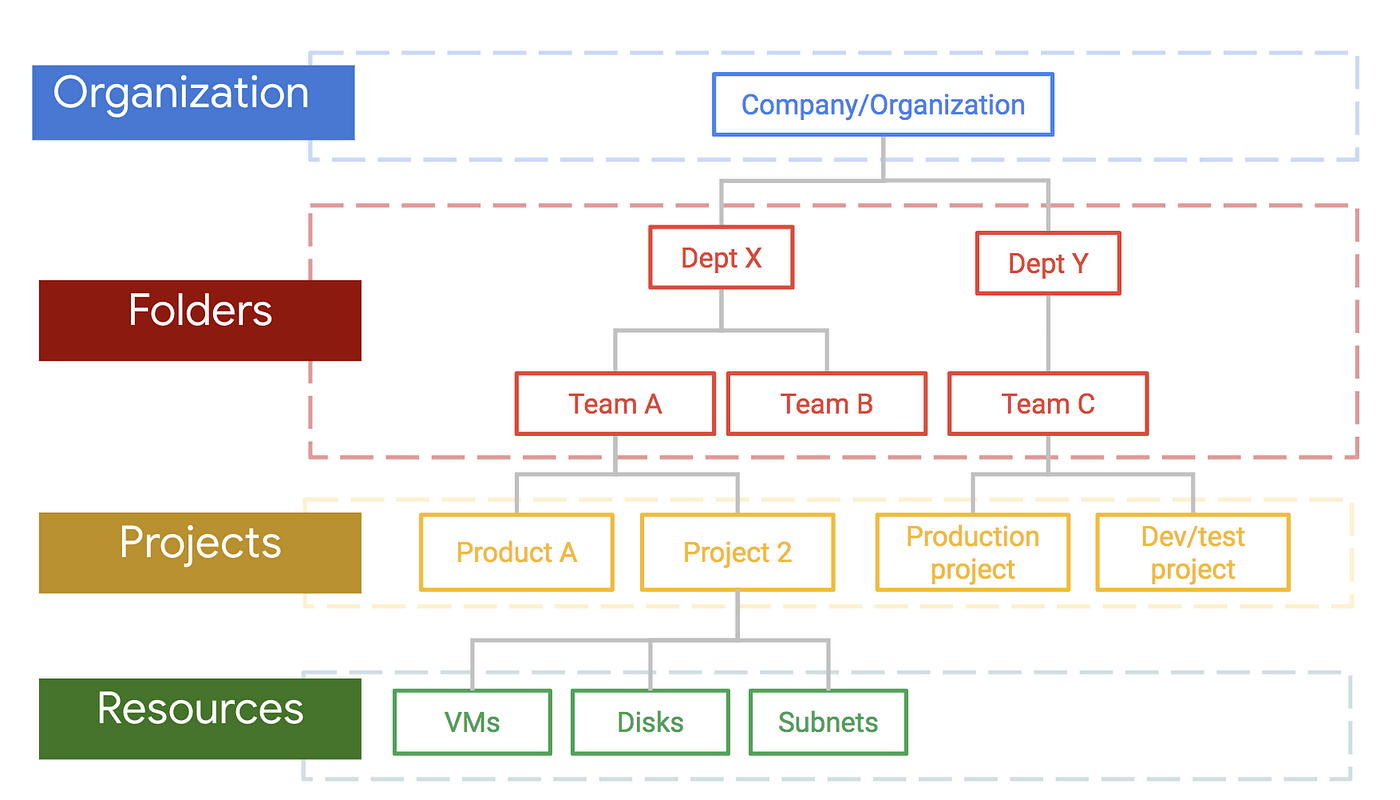
Resources in Google Cloud are organized hierarchically:
IAM policies applied at a higher level (such as an Organization) are inherited by lower levels unless explicitly overridden.
3.3 Permissions: What Actions Are Allowed
Permissions define specific actions that a principal can perform on a resource.
| Permission | Action |
| compute.instances.start | Start a virtual machine |
| storage.objects.list | List objects in a bucket |
| resourcemanager.projects.update | Update project settings |
Permissions are not assigned directly to principals. Instead, they are bundled into roles, simplifying permission management across a cloud environment.
3.4 IAM Policies: Binding Principals to Roles
An IAM Policy binds principals to roles, defining their access to resources.
Example policy (in JSON format):
| json { "bindings": [ { "role": "roles/editor", "members": [ "user:[email protected]" ] } ] } |
- Role: A set of permissions.
- Members: Principals who are granted the role.
IAM policies inherit across the resource hierarchy by default, meaning a role granted at the project level applies to all resources within the project unless explicitly restricted.
4. Understanding IAM Roles
IAM Roles are collections of permissions that grant a specific level of access to a resource. Instead of assigning permissions individually, roles group them together to streamline and standardize access control.
4.1 Basic Roles (Owner, Editor, Viewer)
Basic Roles are predefined, high-level roles introduced in the early versions of Google Cloud IAM. They provide broad access to all resources within a project.
| Role | Capabilities |
| Owner | Full control over all resources, including IAM management |
| Editor | Create, modify, and delete most resources |
| Viewer | Read-only access to all resources |
Important Consideration:
Basic roles are overly permissive and are not recommended for production environments where strict access control is necessary.
4.2 Predefined Roles
Predefined Roles are curated by Google Cloud to offer granular, service-specific permissions. These roles are aligned with particular services and use cases, providing more controlled access than basic roles.
| Predefined Role | Purpose |
| roles/storage.objectViewer | Read-only access to Cloud Storage objects |
| roles/compute.instanceAdmin.v1 | Full management of Compute Engine instances |
| roles/bigquery.dataEditor | Modify BigQuery datasets |
Predefined roles support finer access control and better adherence to the principle of least privilege.
4.3 Custom Roles
Custom Roles allow organizations to define roles tailored precisely to their operational and security requirements by selecting specific permissions.
Creating a custom role using the gcloud CLI:
| bash gcloud iam roles create myCustomRole \ --project=my-project-id \ --title="My Custom Role" \ --permissions="compute.instances.start,compute.instances.stop" \ --stage="GA" |
Custom roles are ideal when predefined roles do not align closely enough with business needs. However, they require careful governance to prevent complexity and ensure consistent security practices.
5. Role Hierarchies in Google Cloud IAM
5.1 How Roles Build on Permissions
In Google Cloud IAM, roles are structured by grouping specific permissions together. Permissions are the most granular level of access control, defining exact actions such as reading a storage object or starting a virtual machine. Roles aggregate these permissions to simplify management.
For example:
- The permission compute.instances.start allows starting a VM.
- The predefined role roles/compute.instanceAdmin.v1 bundles this permission with others related to VM management.
This structure ensures that administrators can manage access by assigning roles rather than handling hundreds of individual permissions manually.
5.2 Relationship Between Basic, Predefined, and Custom Roles
The three types of roles in Google Cloud IAM serve different purposes within the hierarchy:
| Role Type | Description | Use Case |
| Basic Roles | Broad access across all resources within a project | Legacy projects or initial setup |
| Predefined Roles | Service-specific roles curated by Google with fine-grained permissions | Standard production environments |
| Custom Roles | User-defined roles tailored to specific needs | Specialized workflows or internal tools |
Basic Roles cover a wide range of permissions but lack fine control.
Predefined Roles offer a balance of security and usability by aligning permissions with typical operational tasks.
Custom Roles allow maximum flexibility but require careful design and maintenance.
5.3 How Role Hierarchy Impacts Resource Access
In Google Cloud, access decisions are made based on roles assigned at various levels of the resource hierarchy:
Source: Medium
A role assigned at a higher level (such as an Organization or Folder) automatically applies to all child resources unless explicitly overridden.
Key impacts:
- Efficiency: Assigning roles at the Organization or Folder level can quickly grant access across multiple projects.
- Risk Management: Broad assignments can unintentionally overexpose sensitive resources if not managed carefully.
- Granularity: Assigning roles closer to the resource level allows more precise control, minimizing the scope of access.
Effective use of role hierarchies enables scalable and secure access management across complex environments.
6. Managing Access at Different Resource Levels
6.1 Organization-Level IAM Policies
At the Organization level, IAM policies set broad access controls that apply to all resources within the organization unless overridden.
Assigning roles here is suitable for administrative functions such as security auditing, billing management, and global IT administration.
Best Practice:
Use Organization-level policies sparingly and only for roles that genuinely require global access across the entire organization.
6.2 Folder-Level IAM Policies
Folders group projects for organizational and policy management purposes. IAM policies at the folder level provide a middle ground between organization-wide and project-specific access.
Typical uses:
- Grouping projects by department (e.g., Finance, Development, Marketing).
- Assigning department-specific administrators or auditors.
Advantages:
Folder-level policies streamline access management without granting unnecessary organization-wide permissions.
6.3 Project-Level IAM Policies
Projects are the fundamental units where Google Cloud resources are created and managed.
IAM policies at the project level are most common, providing specific teams with the access they need to develop, deploy, and manage applications.
Considerations:
- Restrict roles to the minimum necessary for project operations.
- Separate production and development projects to manage access independently.
Project-level policies offer a good balance between manageability and security for most use cases.
6.4 Resource-Level IAM Policies
For highly sensitive or critical assets, it is possible to apply IAM policies directly to individual resources such as storage buckets, BigQuery datasets, or Compute Engine instances.
Benefits:
- Fine-grained access control.
- Protection of sensitive data even within broader project contexts.
Drawback:
Managing too many resource-level policies can increase administrative overhead and complicate auditing.
Use resource-level policies selectively where additional control is necessary beyond project-level settings.
7. IAM Best Practices for Role Management
7.1 Principle of Least Privilege
The Principle of Least Privilege states that principals should be given the minimum permissions necessary to perform their tasks — no more, no less.
Benefits include:
- Reduced security risks.
- Minimized potential impact of compromised accounts.
- Improved compliance posture.
When assigning roles, always prefer the most restrictive role that still allows the user or service to function effectively.
7.2 Using Predefined Roles Over Basic Roles
Whenever possible, use Predefined Roles instead of Basic Roles.
Predefined Roles:
- Provide more precise access aligned with specific services and tasks.
- Reduce the likelihood of over-privileging users.
- Are regularly updated by Google Cloud to adapt to service changes.
Basic Roles:
- Cover too many permissions.
- Lack fine-grained control.
- Increase risk, especially in production environments.
Migrating away from Basic Roles to Predefined Roles is a key step in maturing cloud security practices.
7.3 Creating and Managing Custom Roles Responsibly
Custom roles are powerful but should be used with care.
Best Practices for Custom Roles:
- Create them only when predefined roles do not meet operational needs.
- Assign only the necessary permissions after careful review.
- Document custom roles thoroughly, including their intended use and the permissions they include.
- Regularly audit custom roles to ensure they remain aligned with security policies and operational requirements.
Poorly managed custom roles can lead to "role sprawl," increasing the difficulty of maintaining and auditing access controls over time.
8. Advanced Topics in Google Cloud IAM
8.1 Conditional Role Bindings
Conditional Role Bindings allow IAM policies to grant permissions only if certain conditions are met. Conditions can be based on attributes like request time, resource tags, or identity properties.
Example (JSON format):
| json { "bindings": [ { "role": "roles/storage.objectViewer", "members": [ "user:[email protected]" ], "condition": { "title": "AllowOnlyDuringBusinessHours", "expression": "request.time.getHours() >= 9 && request.time.getHours() <= 17" } } ] } |
Use cases include restricting access to working hours, controlling permissions based on network locations, and setting resource-specific access controls.
8.2 IAM Deny Policies (Newer Feature)
IAM Deny Policies explicitly block certain actions, even when a user has roles that would otherwise allow them.
Deny policies take precedence over allow policies, offering a critical safeguard mechanism.
Key characteristics:
- Applied across organizations, folders, or projects.
- Support conditional expressions to fine-tune their enforcement.
- Useful for protecting critical resources from deletion or modification.
Example: Prevent any user from deleting Cloud Storage buckets in a production project.
8.3 Role Granting via Service Accounts
Service accounts can be both recipients of roles and delegators of permissions. A common practice is granting a user permission to impersonate a service account, enabling scoped, time-limited access to resources.
Command to allow service account impersonation:
| bash gcloud iam service-accounts add-iam-policy-binding [email protected] \ --member="user:[email protected]" \ --role="roles/iam.serviceAccountTokenCreator" |
This model enhances automation security and helps enforce least privilege for applications and automation scripts.
8.4 Cross-Project and Cross-Organization Access Management
In multi-project or multi-organization environments, it is often necessary to allow cross-boundary access.
Common strategies:
- Grant roles across projects by referencing fully-qualified member identities.
- Implement shared VPCs to centralize networking.
- Set up organizational trust models through Cloud Identity federation or Google Workspace.
Cross-project access demands careful governance to prevent unintended privilege escalation across administrative domains.
9. Auditing and Monitoring IAM Roles
9.1 Using Cloud Audit Logs
Cloud Audit Logs automatically capture activity across Google Cloud resources, recording who accessed what and when.
Audit log types:
- Admin Activity: Tracks administrative operations, such as IAM policy changes.
- Data Access: Captures read/write operations on user data (must be enabled).
Audit logs are essential for:
- Security incident investigations.
- Compliance reporting.
- Ongoing operational monitoring.
Exporting logs to external systems for aggregation and long-term analysis is a recommended best practice.
9.2 Analyzing Policy Changes with Policy Analyzer
Policy Analyzer provides tools for reviewing effective permissions across cloud resources, making it easier to understand who has access.
Key uses:
- Identify excessive or unintended permissions.
- Audit access levels across projects.
- Verify policy changes during infrastructure updates.
Policy Analyzer supports security audits by offering visibility into complex IAM environments.
9.3 Monitoring Role Misconfigurations
IAM role misconfigurations can expose resources to risk or disrupt operations. Common misconfigurations include granting overly broad permissions or creating custom roles without careful scoping.
Best practices to prevent misconfigurations:
- Regularly audit roles and permissions.
- Prefer predefined roles when possible.
- Document the purpose and scope of custom roles.
Proactive monitoring can catch permission drift early and help maintain a secure, stable environment.
10. Common Pitfalls in Role Hierarchies and How to Avoid Them
10.1 Overprovisioning Permissions
Granting more permissions than necessary can lead to security vulnerabilities. Overprovisioned accounts can perform unintended actions, creating risks for data loss, service disruption, or compliance violations.
Recommendation: Apply the principle of least privilege, regularly review access, and minimize role grants.
10.2 Ignoring Folder-Level Inheritance
IAM policies applied at the folder level cascade down to all contained projects and resources. Ignoring this inheritance can lead to unexpected access rights.
Recommendation: Always review inherited policies when assigning roles at the folder or organization level to avoid unintentional permissions.
10.3 Misusing Basic Roles in Production Environments
Basic roles (Owner, Editor, Viewer) are broad and grant more permissions than usually required. Using them in production increases the risk of privilege escalation and misconfigurations.
Recommendation: Replace basic roles with predefined or custom roles aligned to specific operational needs whenever possible.
11. Future Trends and Evolving Practices in IAM
11.1 Evolution of IAM in Multi-Cloud Environments
As more organizations adopt multi-cloud strategies, IAM systems are evolving to support access control across platforms like AWS, Azure, and Google Cloud.
Emerging solutions include:
- Federated identity providers that support Single Sign-On (SSO) across clouds.
- Centralized IAM platforms that abstract identity management across providers.
- Cloud-native IAM tools expanding support for external identities and APIs.
Future IAM strategies will prioritize interoperability, centralized governance, and cross-cloud visibility.
11.2 The Rise of Attribute-Based Access Control (ABAC)
ABAC introduces access policies based on attributes (e.g., user role, resource tag, environment) rather than static role bindings.
Benefits of ABAC:
- Supports dynamic, context-aware permissions.
- Scales better in large, complex environments.
- Enables policy definitions using business logic.
Although IAM in Google Cloud is primarily role-based today, ABAC features are increasingly being integrated to enable more adaptable access models.
11.3 Security Automation for IAM Role Management
Automated tools for IAM management are becoming essential as environments grow in size and complexity.
Common automation practices include:
- Scheduled audits of IAM bindings and role usage.
- Automated deprovisioning of unused permissions.
- Integration with CI/CD pipelines to enforce IAM policy standards during deployments.
Security automation reduces human error and ensures that IAM policies remain aligned with compliance and operational goals.
12. Conclusion
12.1 Summary of Key Takeaways
Google Cloud IAM provides a flexible and secure way to manage access across your cloud infrastructure. Understanding the structure of roles, permissions, and policies—along with the resource hierarchy—enables more effective and secure access control.
Key principles to remember:
- Use predefined roles and avoid basic roles in production.
- Apply the principle of least privilege consistently.
- Manage access at the appropriate level (organization, folder, project, resource).
- Monitor and audit IAM regularly using Cloud Audit Logs and Policy Analyzer.
- Stay updated with evolving IAM features such as conditional bindings and deny policies.
12.2 Final Thoughts on Designing Secure Role Hierarchies
IAM is not a one-time setup, it is a continuous process that evolves with your infrastructure. A well-designed role hierarchy:
- Minimizes risk,
- Improves maintainability,
- Aligns with business and security objectives.
As your organization scales, investing in proper IAM design, automation, and policy governance will pay long-term dividends in security, compliance, and operational efficiency.