In the early days of cloud computing, managing access was both complex and risky. Hard-coded credentials and simple authentication systems couldn’t keep up with the growing demands of cloud environments. These outdated practices left organizations vulnerable to security breaches.
This highlighted key challenges:
- Manual Credential Management: Embedding access keys directly in code increased the risk of exposure.
- Basic Access Models: Simple username-password systems couldn’t handle complex roles or permissions.
- Limited Control: Enforcing least-privilege access was difficult, leading to overly permissive user rights and security gaps.
Recognizing the need for a more secure and manageable approach, the cloud industry moved toward developing a more sophisticated, centralized solution. This led to the creation of AWS Identity and Access Management (IAM) in 2011.
Why did AWS Introduce IAM?
AWS introduced IAM in 2011 to address the growing complexity and security demands of cloud environments. The goal was to provide centralized, fine-grained control over access to cloud resources, improving security while simplifying access management. IAM was designed not only for managing access within the AWS ecosystem but also to play a crucial role in overall cloud security posture management (CSPM).
IAM is critical for ensuring secure and compliant access in multi-cloud environments, where organizations often use a mix of AWS, Azure, Google Cloud, and on-premises systems. In these scenarios, IAM not only secures access to AWS resources but also contributes to the broader cloud security framework by enforcing identity-based access control across different platforms, minimizing security gaps, and enhancing visibility into access and permissions.
Understanding AWS IAM
AWS IAM is a powerful tool that allows administrators to manage who has access to AWS services and resources, and what actions they can perform. It is built to simplify access management while enhancing security by enabling organizations to:
- Control user access: Specify who can access which resources and the actions they can take.
- Enable secure collaboration: Ensure that users or services in different departments or regions have the appropriate permissions, without exposing unnecessary resources.
- Enforce security practices: IAM helps organizations implement security best practices, such as least-privilege access and strong authentication, reducing the risk of breaches.
Identity vs. Access Management: It's essential to distinguish between identity and access within IAM:
- Identity refers to the authentication aspect of IAM, i.e., verifying who a user or service is. This involves using methods such as username/password, Multi-Factor Authentication (MFA), and external identity federation (e.g., Active Directory, Google, etc.).
- Access refers to authorization, which controls what actions the authenticated identity can perform. IAM defines access policies that grant or deny actions on AWS resources based on the identity’s permissions.
IAM Authentication and Authorization
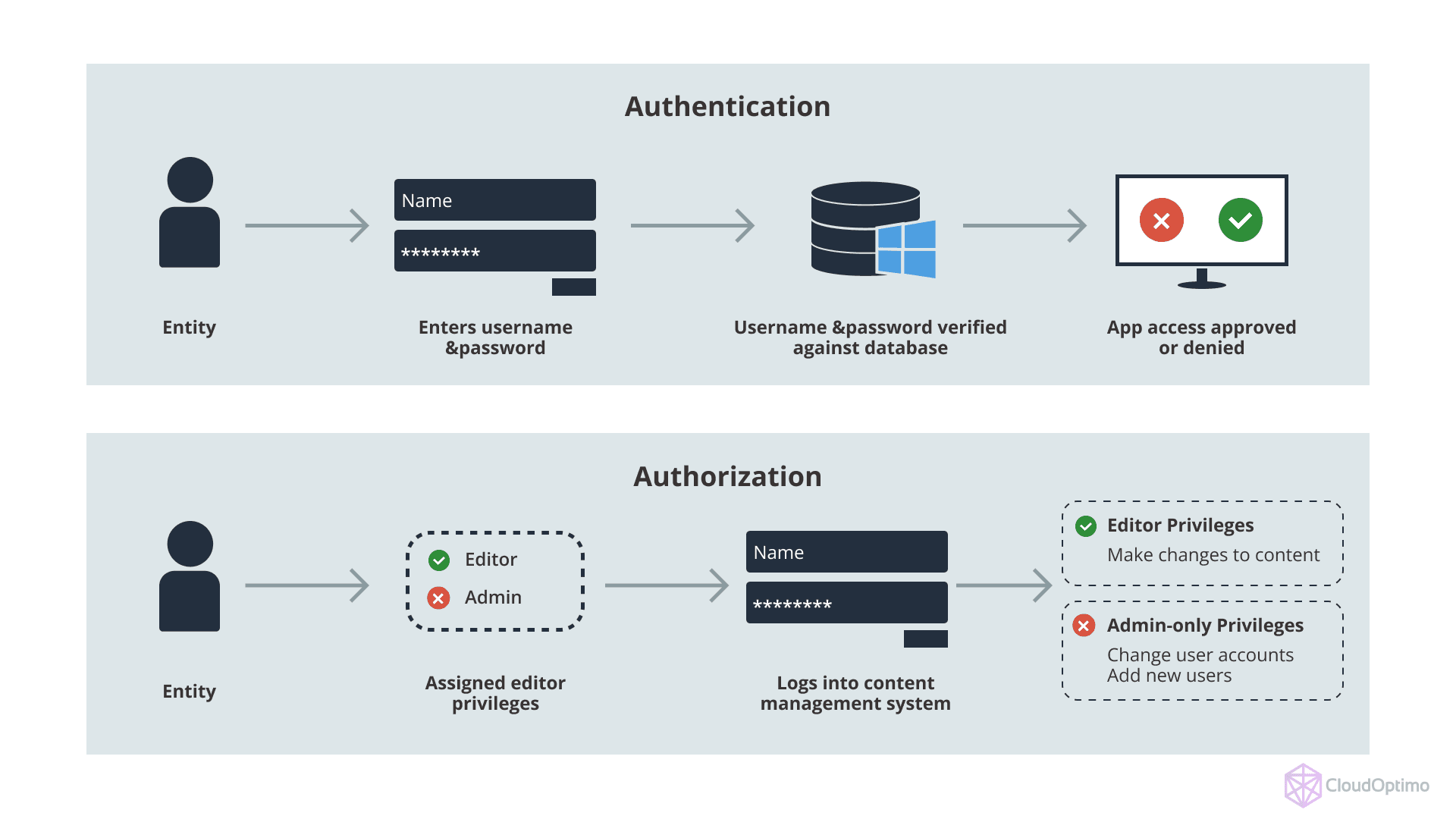
IAM is centered around two essential aspects: authentication and authorization.
- Authentication: The process of verifying the identity of a user, service, or application. AWS IAM supports a variety of authentication methods, such as username/password combinations, multi-factor authentication (MFA), and programmatic access via Access Keys or AWS Single Sign-On (SSO).
- Authorization: Once authenticated, authorization controls what actions the authenticated user or service can perform. IAM policies govern authorization by specifying which resources a user or service can access and what actions they can perform on those resources.
Components of AWS IAM
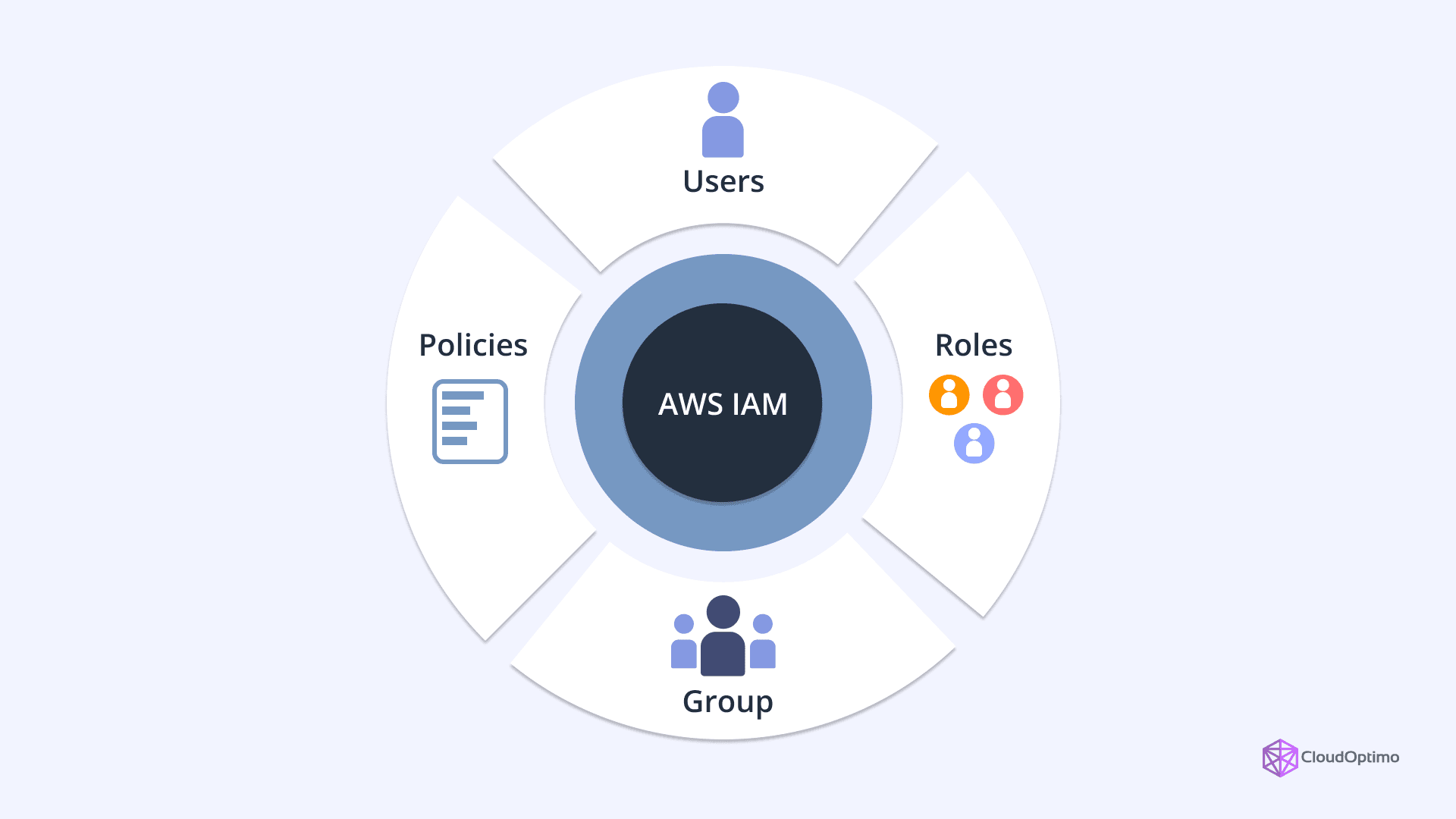
At its core, IAM consists of several key components that work together to provide comprehensive access control:
- Users: In IAM, a user represents an individual identity within an AWS account. It can be a person or an application that requires access to AWS resources. Users are typically associated with a set of credentials, such as a username and password, and may also be granted programmatic access via Access Keys.
- Groups: Groups are collections of IAM users. By assigning users to groups, organizations can apply permissions to all users within the group, simplifying the management of large sets of users. This is especially useful for organizing users based on their roles, departments, or access levels.
- Roles: IAM roles are AWS identities that can be assumed by entities such as IAM users, AWS services, or external accounts. Roles provide temporary security credentials to authorized entities, allowing them to perform specific actions on resources without requiring permanent credentials.
- Policies: Policies are documents that define permissions in IAM. They specify what actions are allowed or denied on which resources and are usually written in JSON format. Policies can be attached to users, groups, or roles to grant access.
- Permissions: Permissions determine what actions a user or role can perform on AWS resources. These permissions are specified in IAM policies and are fundamental to the concept of least privilege – granting only the minimum permissions necessary for a task.
Each component works together to create a secure and organized access control mechanism within your AWS environment.
IAM Roles and Their Use Cases
IAM roles are essential for managing temporary access and cross-account access in AWS. Roles enable applications and AWS services like EC2 or Lambda to assume permissions without embedding long-term credentials in the application code.
Key Use Cases for IAM Roles:
- Cross-Account Access: A role can be used to allow a user or service from one AWS account to access resources in another account.
- Service-to-Service Access: Roles allow AWS services like EC2, Lambda, or ECS to interact with other AWS services or resources securely, without requiring user credentials.
For example, an EC2 instance can assume a role that grants it the permissions to read from an S3 bucket, without needing to store access keys in the instance itself. Similarly, a Lambda function can assume the role to read from DynamoDB tables.
Example IAM Role Policy:
This example policy grants the EC2 instance permission to list and get objects from a specific S3 bucket:
| { "Version": "xxxx-xx-xx", "Statement": [ { "Effect": "Allow", "Action": [ "s3:ListBucket", "s3:GetObject" ], "Resource": [ "arn:aws:s3:::example-bucket", "arn:aws:s3:::example-bucket/*" ] } ] } |
This policy allows an EC2 instance, assuming a role, to interact with the example-bucket S3 resources securely.
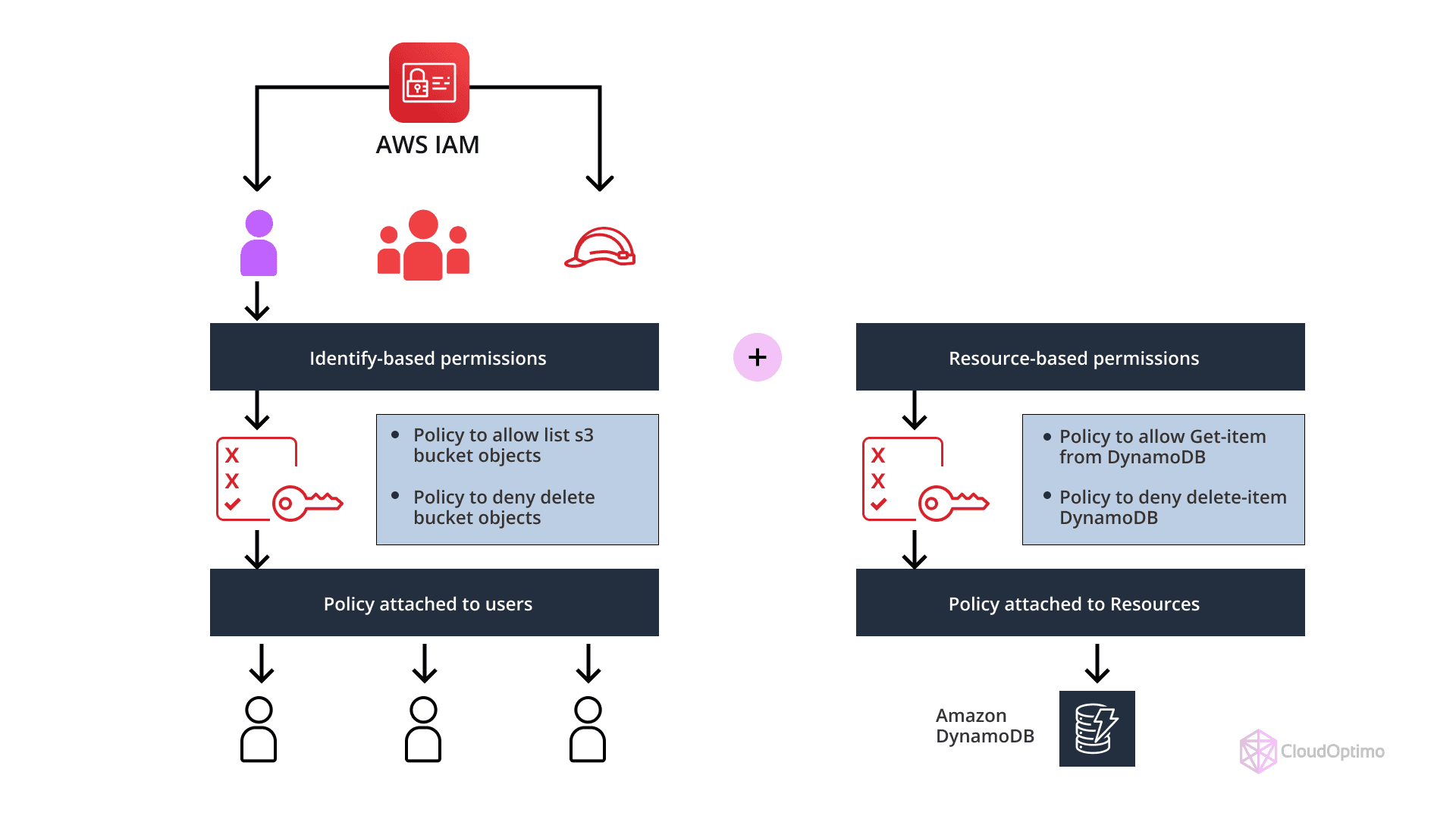
IAM Policies and Permission Management
Source - Cloudiofy
IAM policies are at the core of AWS access management. Policies define which actions are allowed or denied on specific AWS resources, and they can be attached to IAM users, groups, or roles. There are two types of IAM policies:
- Managed Policies: These are predefined policies created and maintained by AWS. They offer a convenient way to assign permissions for common use cases and are regularly updated by AWS to reflect new services and features. Examples include AdministratorAccess, ReadOnlyAccess, and PowerUserAccess.
- Inline Policies: Inline policies are custom policies that are embedded directly into a user, group, or role. While they offer more fine-grained control over permissions, they are not reusable across multiple identities. Inline policies are ideal when unique, tailored permissions are required for specific users or roles.
Policies use JSON syntax and include key components such as:
- Version: Specifies the version of the policy language.
- Statement: The main element of a policy, consists of one or more individual statements.
- Effect: The effect of the statement – either "Allow" or "Deny".
- Action: The actions that the statement applies to (e.g., s3:ListBucket or ec2:StartInstances).
- Resource: The resources the statement applies to (e.g., an S3 bucket or EC2 instance).
- Condition: Optional conditions under which the statement is applied (e.g., requiring MFA for sensitive actions).
Here’s an example of a simple IAM policy:
| { "Version": "xxxx-xx-xx", "Statement": [ { "Effect": "Allow", "Action": "s3:ListBucket", "Resource": "arn:aws:s3:::my-bucket" } ] } |
This policy grants permission to list the contents of a specific S3 bucket.
Real-World Example
Imagine a company that starts small but quickly grows into a large enterprise. Initially, they used IAM to manage access to a few AWS services like EC2 and S3. At first, they create basic IAM roles for their two main teams—Developers and Admins—with broad permissions like full access to EC2, S3, and Lambda. Policies are simple, and everything is easy to manage.
However, as the company scales, it begins to hire more specialized employees—Data Analysts, Support Staff, and Contractors. Each new role requires different levels of access to various AWS services. The company creates new IAM roles and attaches specific policies to meet the diverse needs of these teams.
With growth comes complexity. Now, they have a mix of custom policies, multiple roles, and varying access requirements across their organization. Managing all these moving parts becomes challenging, especially when new users are added and more services are introduced. Permissions become harder to track, and maintaining a clear view of who has access to what becomes a challenging task.
IAM Policy Evaluation Logic
IAM policy evaluation is a critical concept in ensuring that users have the appropriate access. Here's how IAM processes permission requests:
- Explicit Deny: If a policy explicitly denies an action, that will override any allow statement.
- Explicit Allow: IAM evaluates allow statements next and grants access if no deny statements are present.
- Implicit Deny: If no explicit allow or deny is found, IAM denies access by default.
Example IAM Policy Evaluation
- Step 1: An IAM user requests access to an S3 bucket.
- Step 2: IAM evaluates the policies attached to the user, their group, and any roles they may assume.
- Step 3: The policies are checked in the order of deny -> allow -> implicit deny.
Advanced IAM Policy Evaluation Logic
IAM policy evaluation follows a specific decision-making process:
- Explicit Deny Precedence
| { "Priority": [ "Explicit Deny", "Explicit Allow", "Implicit Deny" ] } |
- Policy Evaluation Flow
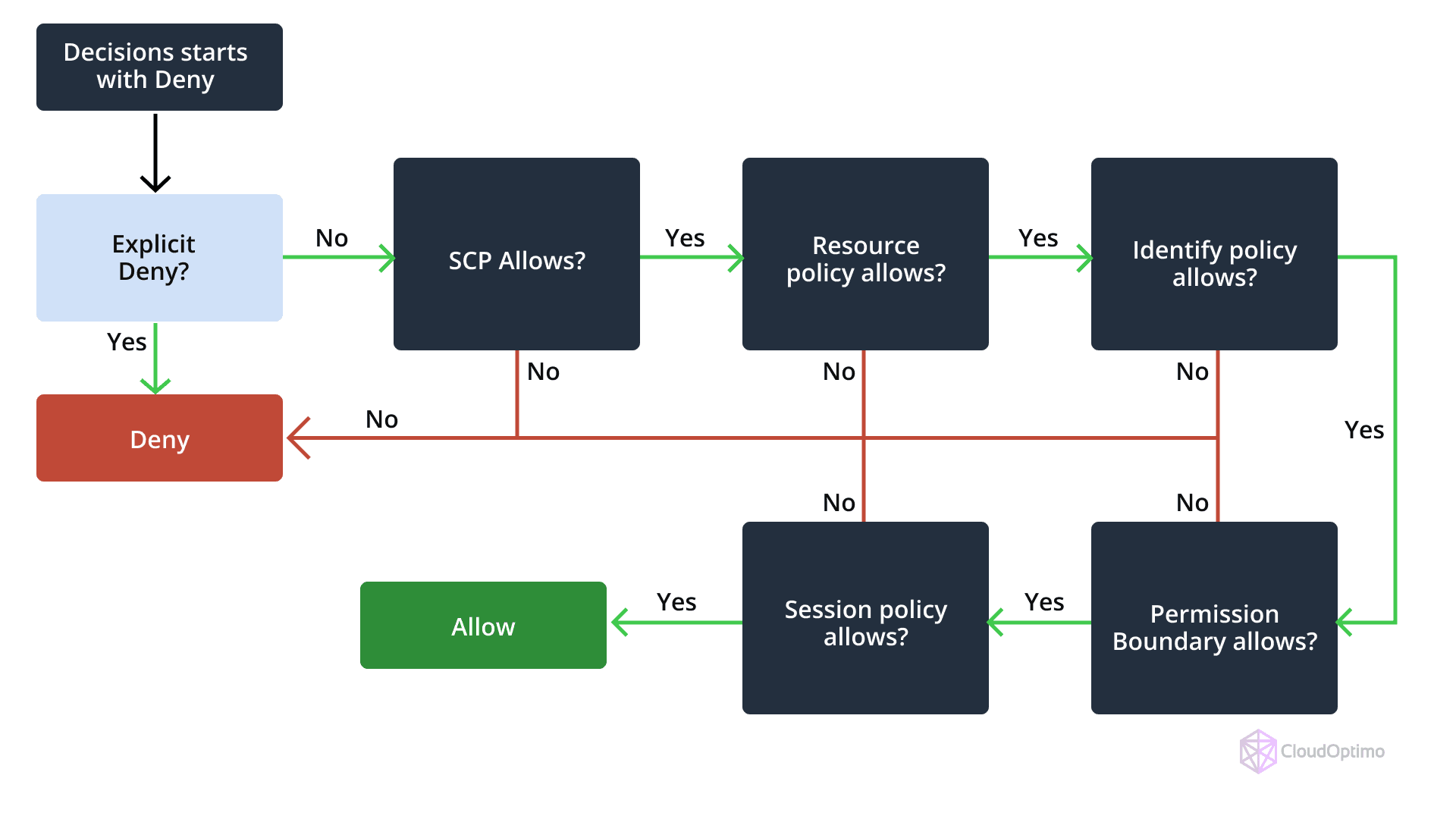
Source - Tutorials Dojo
- Start with all permissions denied
- Evaluate identity-based policies
- Apply resource-based policies
- Check for explicit denies
- Apply explicit allows
- Resolve the final permission set
Detailed Examples of Complex Policy Construction
Here’s an advanced example that allows read access to objects within a specific prefix in an S3 bucket:
| { "Version": "xxxx-xx-xx", "Statement": [ { "Effect": "Allow", "Action": ["s3:ListBucket", "s3:GetObject"], "Resource": [ "arn:aws:s3:::example-bucket", "arn:aws:s3:::example-bucket/*" ], "Condition": { "StringEquals": { "s3:prefix": "important-data/" } } } ] } |
This policy allows users to list and retrieve objects from the example-bucket, but only those under the important-data/ prefix, which is an effective way to limit access to sensitive data.
While AWS introduced IAM in 2011, breaches like the 2014 incident remind us that proper implementation and continuous improvement of access controls are vital to protect cloud environments. Misconfigured or overly complex policies pose security risks and can impact system performance.
Performance Implications of Complex IAM Configurations
With an increasing number of policies, roles, and permissions, the time it takes IAM to evaluate requests increases, which can degrade performance, particularly when large numbers of users are accessing the environment simultaneously.
Optimization Strategies
As IAM configurations become more complex, optimization becomes key to maintaining performance. Here are some strategies:
- Limit Policies per Identity: Minimize the total number of policies attached to any given identity.
Optimize Policy Evaluation: Use the AWS CLI to analyze policy complexity. For example, the simulate-principal-policy command can simulate policy evaluations and help identify performance issues.
Example CLI Command:
| # AWS CLI to analyze policy complexity aws iam simulate-principal-policy \ --policy-source-arn arn:aws:iam::ACCOUNT_ID:policy/POLICY_NAME \ --action-names s3:GetObject |
- Use Managed Policies: Where possible, use AWS-managed policies, which are maintained by AWS and optimized for common use cases, instead of creating custom policies from scratch.
Challenges and Limitations of Large-Scale IAM Implementations
As organizations grow, the complexities of IAM become more noticeable. Managing IAM at scale introduces several challenges:
Policy Sprawl
Initially, the company may have a few simple IAM policies to manage access. But as the team expands, the number of custom policies grows significantly. This policy sprawl can quickly become overwhelming. Organizations struggle to:
- Track which policies are in use.
- Identify redundant policies.
- Ensure policies align with security best practices.
These challenges increase the risk of misconfigurations and complicate administrative tasks.
IAM Resource Limits
AWS imposes limits on the number of IAM entities (users, roles, policies) per account. As organizations expand, they may hit these limits, requiring careful planning. Failing to manage these limits can disrupt operations and create bottlenecks.
IAM Limits to Keep in Mind:
- Users per account: AWS allows up to 5000 IAM users per AWS account by default.
- Groups per account: A maximum of 300 groups per account.
- Roles per account: 1000 roles per AWS account.
- Managed Policies: 150 managed policies per account.
These limits highlight the need for scalable IAM practices, especially when managing large teams or complex environments.
Performance Bottlenecks
With the increasing number of roles, policies, and permissions, IAM evaluation time may increase. When a user requests access to a resource, IAM must evaluate all policies and conditions before granting access. As the number of policies grows, this evaluation process becomes more complex and can result in performance bottlenecks, impacting user experience and overall operations.
Why This Matters?
These challenges highlight the importance of proactive IAM management and planning, especially in rapidly growing environments. Addressing policy sprawl, monitoring resource limits, and optimizing performance are crucial steps in maintaining a scalable and secure IAM implementation.
Benefits of AWS IAM
AWS IAM offers several benefits for organizations leveraging cloud services:
- Centralized Access Control: IAM enables organizations to manage all user permissions centrally, providing a clear overview of who has access to which resources and ensuring that appropriate policies are in place.
- Scalability: IAM scales with the organization. Whether there are ten or ten thousand users, IAM can manage identities and permissions with the same level of security and ease.
- Granular Access Control: With IAM, permissions can be defined at a fine-grained level. This allows administrators to restrict access to specific actions, resources, or even specific data sets, ensuring that users only have access to what is necessary for their role.
- Security and Compliance: IAM plays a crucial role in enforcing security policies and compliance standards. By managing access and auditing activities, IAM helps organizations meet regulatory requirements and safeguard sensitive information.
Best Practices for Implementing AWS IAM
Effectively managing AWS IAM ensures that your cloud environment remains secure, scalable, and compliant. Here are key best practices to consider:
- Adopt the Principle of Least Privilege
- What it means: Grant users and services only the permissions they need to perform their tasks.
- Implementation: Start with minimal permissions and step by step, add access as required. Use IAM policies to define allowed actions and resources precisely.
- Use IAM Roles for Applications and Services
- Avoid Hard-Coded Credentials: Replace access keys embedded in code with IAM roles for AWS services. This reduces the risk of credential exposure.
- Service-Specific Roles: Create distinct roles for different AWS services (e.g., Lambda, EC2) to ensure they have only the necessary permissions.
- Implement Multi-Factor Authentication (MFA)
- For All Users: Require MFA for IAM users, especially those with administrative privileges.
- Virtual MFA Devices: Encourage using virtual MFA devices or hardware tokens to enhance security.
- Regularly Review and Audit IAM Policies
- Policy Evaluation Tools: Use AWS IAM Access Analyzer and Security Hub to identify overly permissive policies and unused access rights.
- Audit Logs: Monitor user activity via AWS CloudTrail and set up alerts for suspicious behavior.
- Manage IAM Policies Centrally
- Consolidate Policies: Minimize the number of policies and avoid creating policy duplicates.
- Tag Resources and Identities: Use tags to organize and track IAM users, roles, and policies across the organization.
- Leverage Managed Policies When Appropriate
- AWS-Managed Policies: Use these for standard access patterns, such as ReadOnlyAccess or AdministratorAccess.
- Custom Policies: Create specific policies for unique business requirements while adhering to best security practices.
- Secure Root Account Access
- Restrict Usage: Use the root account only for initial setup and emergency purposes.
- Enable MFA: Ensure that MFA is enabled for the root account and regularly monitor for unexpected logins.
- Automate Access Management with IAM Access Analyzer
- Automated Analysis: Regularly analyze resource policies to identify unintended public or cross-account access.
- Integrate with CI/CD Pipelines: Incorporate access checks into deployment pipelines to prevent introducing security risks.
- Establish a Clear IAM Governance Framework
- Role-Based Access Control (RBAC): Define clear roles for different departments or teams.
- Review Processes: Implement periodic access reviews and approval workflows to maintain compliance.
- Prepare for Scalability
- Plan for Limits: Monitor IAM entity limits and consider using multiple AWS accounts or AWS Organizations for better scalability.
- Cross-Account Access: Use IAM roles for cross-account access instead of duplicating user accounts across environments.
Industry-Specific IAM Best Practices
- Financial Services
- Implement strict segregation of duties
- Enable comprehensive audit logging
- Use time-bound access for sensitive roles
- Healthcare
- HIPAA compliance configurations
- Granular access to patient data systems
- Implement role-based access with least privilege
- Technology Startups
- Flexible, scalable permission models
- Quick onboarding and offboarding processes
- Integration with development workflows
Advanced IAM Features
As organizations scale and integrate with other systems, AWS IAM offers advanced features like cross-account access and identity federation.
Cross-Account Access
Cross-account access allows secure resource sharing between AWS accounts through temporary, encrypted credentials. Key components:
- Trust Relationship Configuration
- Role Assumption Mechanism
- Secure Credential Exchange
Detailed Cross-Account Role Example
| { "Version": "xxxx-xx-xx", "Statement": { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::123456789012:role/ExampleRole" } } |
Cross-Account Access Example
Let’s go over the process of setting up cross-account access. Suppose Account A wants to allow an IAM user from Account B to access a specific resource, such as an S3 bucket.
Step 1: Create a Role in Account A
In Account A, create an IAM role that grants permissions to access the S3 bucket. The trust policy in the role allows entities from Account B to assume this role.
json
| { "Version": "xxxx-xx-xx", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::AccountB-ID:user/AccountBUser" }, "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::AccountA-ID:role/CrossAccountRole" } ] } |
Step 2: Set Permissions for the Role
Attach the necessary permissions to the role in Account A. For example, allow read access to a specific S3 bucket.
json
| { "Version": "xxxx-xx-xx", "Statement": [ { "Effect": "Allow", "Action": "s3:GetObject", "Resource": "arn:aws:s3:::example-bucket/*" } ] } |
Step 3: Assume the Role from Account B
In Account B, the IAM user will assume the role using the sts:AssumeRole API call. This gives them temporary credentials to access the S3 bucket in Account A.
Federated Access:
IAM also allows users to authenticate through external identity providers (like Active Directory, Google Workspace, etc.) to access AWS resources without needing separate AWS credentials.
Comparative Analysis: IAM Across Cloud Providers
While AWS IAM is one of the most comprehensive solutions available, other cloud providers like Azure and Google Cloud also have robust IAM systems. Here's a comparative look:
| Feature | AWS IAM | Azure AD | Google Cloud IAM |
| Granularity | Fine-grained, resource-level control | Medium-grained, role-based access | Fine-grained, resource-level control |
| Cross-Account Access | Native support for cross-account roles | Requires additional configuration (Azure Lighthouse) | Limited; supports cross-project but limited cross-account |
| Federation Options | Extensive (supports SAML, OpenID Connect, and more) | Comprehensive (supports SAML, OAuth 2.0, OpenID Connect) | Moderate (supports SAML, OIDC, but less flexible) |
| Policy Complexity | Highly flexible and detailed policies | Moderate, with simpler role assignments | Advanced, with detailed policy and condition support |
| Identity Management | Manages identities, roles, and policies across AWS services | Integrated with Microsoft ecosystem (including on-premise AD) | Integrated with GCP services, supports hierarchical structures |
| Role-Based Access Control (RBAC) | Supports both role-based and attribute-based access control | Strong RBAC capabilities | Strong RBAC with role bindings and conditions |
| Auditing and Logging | Comprehensive (AWS CloudTrail) | Comprehensive (Azure Monitor, Azure Sentinel) | Comprehensive (Cloud Audit Logs) |
| Integration with Other Services | Native integration with AWS services | Seamless integration with Microsoft services (e.g., Office 365) | Strong integration with GCP services (e.g., BigQuery, Compute Engine) |
| Ease of Use | Complex, requires understanding IAM policies | User-friendly, especially for Microsoft environments | Moderate; easier if familiar with GCP structure |
IAM and Security Compliance
IAM is a critical component of any organization’s security posture, especially when meeting compliance requirements. AWS provides a variety of compliance programs, including PCI-DSS, HIPAA, and SOC, which require secure access management practices. IAM helps organizations:
- Control Access: By defining clear policies for user roles and permissions, IAM helps control access to sensitive data, ensuring compliance with regulations.
- Enable Auditing and Monitoring: IAM integrates with AWS CloudTrail to log all API calls, providing detailed records of who accessed what and when. This audit trail is essential for compliance and troubleshooting security incidents.
- Enforce Strong Authentication: Implementing multi-factor authentication (MFA) and strong password policies ensures that only authorized personnel can access critical resources.
IAM Evolution: From 2011 to Present
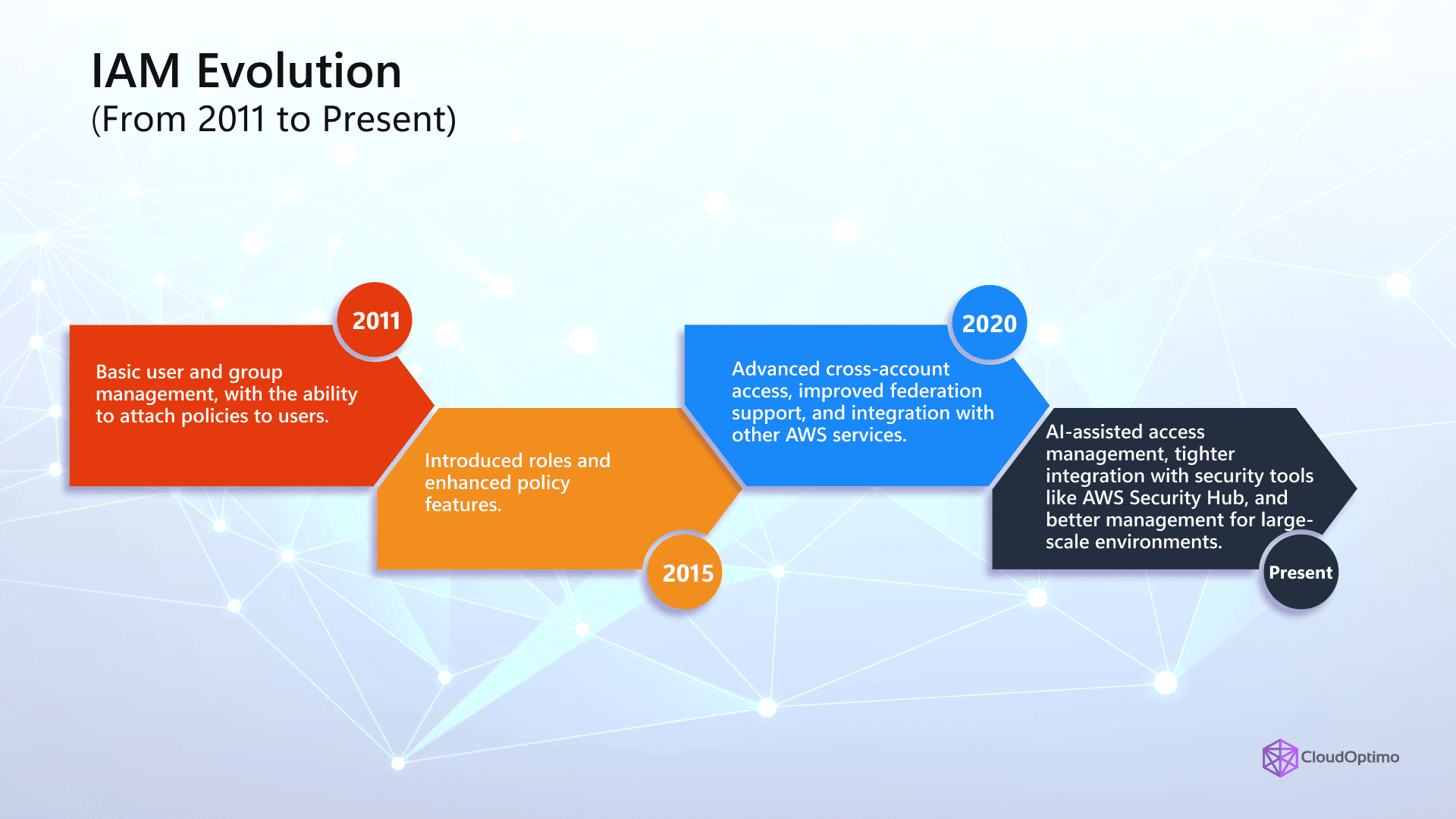
- 2011: Basic user and group management, with the ability to attach policies to users.
- 2015: Introduced roles and enhanced policy features.
- 2020: Advanced cross-account access, improved federation support, and integration with other AWS services.
- Present: AI-assisted access management, tighter integration with security tools like AWS Security Hub, and better management for large-scale environments.
Key Takeaways
- IAM is essential for controlling access to AWS resources securely and efficiently.
- While powerful, Complex IAM configurations come with performance considerations that must be managed carefully.
- Best practices, including role-based access, MFA, and auditing, are crucial to maintaining a secure environment.
- The IAM ecosystem has evolved significantly since 2011, with enhanced features like cross-account access, federation, and integrations with other AWS security tools.
As cloud environments evolve, AWS IAM continues to be a foundational tool for securing resources and enabling seamless, secure scaling of cloud operations.