Managing identities and access securely has become essential for businesses of all sizes. Microsoft Intra ID, part of the broader Identity and Access Management (IAM) ecosystem, plays a crucial role in ensuring that your enterprise’s digital infrastructure is both secure and efficient.
In this blog, we will explore everything you need to know about Microsoft Intra ID, from its key features and integration capabilities to its security features and advanced use cases.
By the end of this post, you'll be equipped with the knowledge to maximize the potential of Microsoft Entra ID for your organization.
The Role of Identity and Access Management (IAM) in Modern Businesses
Modern businesses rely on Identity and Access Management to answer three fundamental questions:
- Who are you? (Authentication)
- What are you allowed to access? (Authorization)
- How can we verify you're who you claim to be? (Verification)
Effective IAM connects users to the resources they need while protecting sensitive data from unauthorized access. In today's environment, where data breaches can cost millions and damage reputations permanently, IAM isn't just an IT function—it's a business necessity.
What is Microsoft Entra ID?
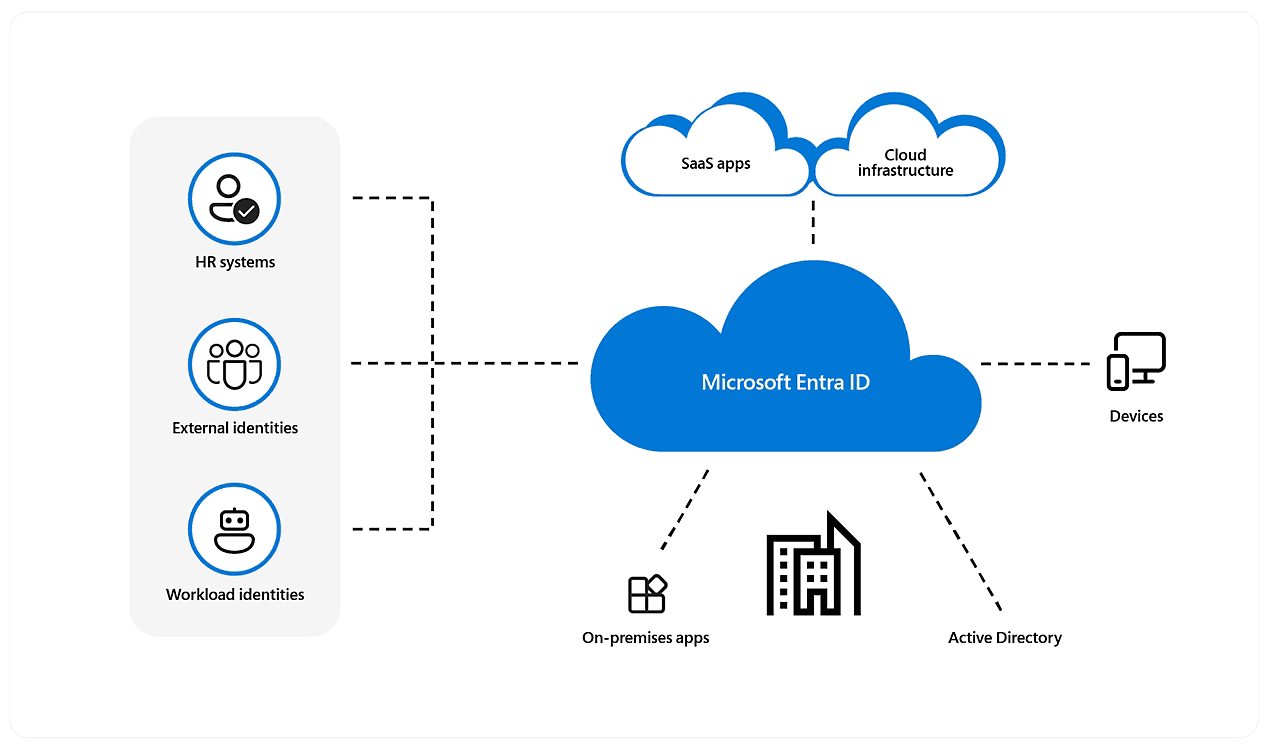
Source - Azure
Microsoft Entra ID, formerly known as Azure Active Directory (Azure AD), is Microsoft's cloud-based identity and access management service. It serves as the control center for who can access what within your digital environment. Think of Entra ID as the modern evolution of traditional Active Directory, rebuilt for today's cloud-centric environment
At its core, Entra ID provides a single trusted system that manages user identities and controls access to applications, data, and resources—whether they're hosted in Microsoft's cloud, other cloud providers, or on-premises. It's the identity foundation that powers Microsoft 365, Azure, and thousands of third-party applications.
Why Enterprises Are Adopting It?
Organizations are rapidly embracing Entra ID for several compelling reasons:
- Security enhancement: As identity becomes the new perimeter, Entra ID provides robust protection against the most common attack vectors.
- Productivity gains: Employees can access all their applications through a single set of credentials, eliminating password fatigue and reducing IT support costs.
- Modern work enablement: Entra ID supports secure remote work, bringing together employees, partners, and customers in a protected digital environment.
- Regulatory compliance: Built-in tools help organizations meet increasingly strict privacy and security regulations.
Key Capabilities of Microsoft Entra ID
Microsoft Entra ID delivers a comprehensive set of capabilities:
Cloud-First Authentication: Secure Access, Anytime, Anywhere
With Microsoft Entra ID, authentication is built for the cloud, in the cloud. Unlike traditional identity systems tied to on-premises infrastructure, Entra ID ensures that users—whether in an office, working remotely, or using mobile devices—can securely access their resources from any location, without the need for VPNs or legacy authentication methods.
- Single Sign-On (SSO): One login grants access to Microsoft 365, Azure, and thousands of cloud apps. No more juggling multiple passwords.
- Passwordless Authentication: Support for biometrics, security keys, and authenticator apps to eliminate the weakest link—passwords.
Adaptive Security with Conditional Access
Cloud environments demand context-aware security. Microsoft Entra ID’s Conditional Access continuously evaluates login requests, ensuring access decisions are based on who the user is, where they are, what device they’re using, and the risk associated with the sign-in attempt.
- Grant or block access dynamically based on real-time risk signals.
- Enforce step-up authentication (MFA) only when needed—reducing friction for legitimate users.
- Protect SaaS and on-prem apps equally, applying consistent security across hybrid environments.
Identity Protection: AI-Powered Threat Defense
Cyber threats evolve faster than manual security policies can keep up. Microsoft Entra ID leverages AI-driven Identity Protection to detect suspicious login attempts, compromised credentials, and unusual user behavior—all without human intervention.
- Automated risk detection based on Microsoft’s vast threat intelligence network.
- Real-time remediation, from blocking high-risk sign-ins to enforcing password resets.
- Integration with Microsoft Defender to correlate identity risks with broader security threats.
Cloud-Based Lifecycle Management: Automation at Scale
Managing users, roles, and access manually in the cloud is inefficient. Microsoft Entra ID automates identity lifecycle management, ensuring that the right people have the right access—and that access is revoked when it’s no longer needed.
- Seamless onboarding and offboarding of employees, partners, and contractors.
- Dynamic user groups that adjust permissions based on department, role, or project.
- Self-Service Password Reset (SSPR) reduces IT workload and improves user experience.
Hybrid Identity: Bridging Cloud and On-Premises Environments
For organizations running hybrid IT, Microsoft Entra ID extends identity capabilities beyond the cloud, allowing seamless integration with on-premises Active Directory (AD) and legacy applications.
- Azure AD Connect syncs on-prem users and credentials with the cloud.
- Hybrid Conditional Access ensures both cloud and on-prem resources follow the same security rules.
- SSO to on-prem applications, even if they weren’t originally designed for the cloud.
Secure Access Beyond Employees: External Identities & B2B Collaboration
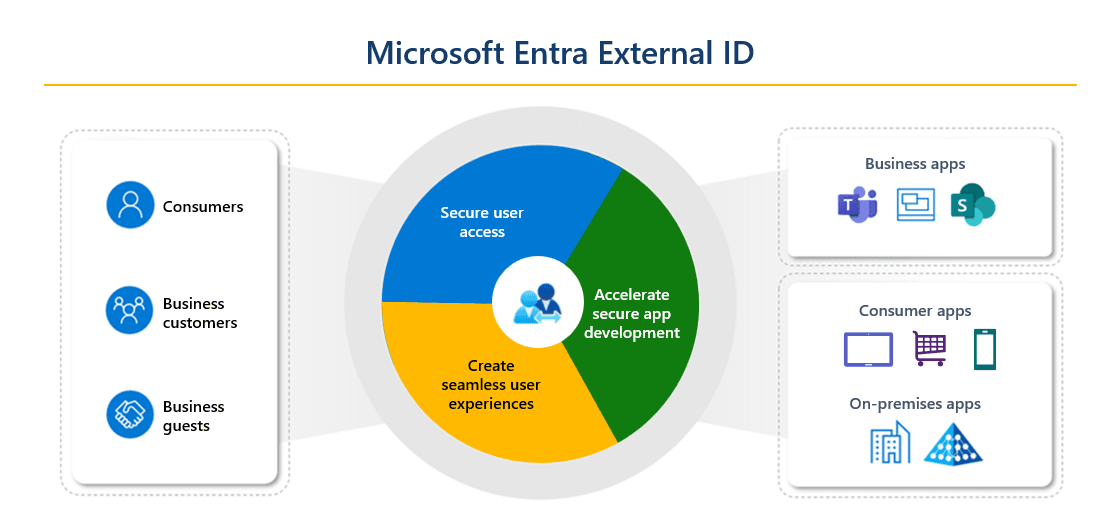
Source - Azure
Cloud ecosystems aren’t just for employees—they include vendors, partners, and customers who also need access. Microsoft Entra ID enables organizations to manage external identities without the complexity of separate accounts securely.
- B2B guest access allows partners to sign in with their own credentials (Google, Facebook, or other Entra ID tenants).
- B2C identity management supports authentication for consumer-facing applications, integrating with social logins and custom policies.
Compliance-Driven Identity Governance
Identity security is as much about compliance as it is about access. Microsoft Entra ID offers Identity Governance, ensuring that access to cloud resources is continuously monitored, reviewed, and adjusted to align with compliance requirements.
- Access reviews ensure that inactive users and unnecessary permissions are removed.
- Privileged Identity Management (PIM) reduces risk by granting elevated access only when needed.
- Built-in audit logs and reports simplify compliance with ISO, GDPR, NIST, and other regulatory standards.
These features work together to create a security posture that's both strong and flexible—protecting resources while enabling productivity.
Migration Strategies: Transitioning from Traditional Active Directory to Microsoft Entra ID
For organizations currently using on-premises Active Directory, transitioning to Microsoft Entra ID represents a significant evolution in identity management. Here's how to approach this migration strategically:
Assessment and Planning
Before making any changes, take stock of your current environment:
- Inventory your existing AD infrastructure, including domain controllers, forests, and trusts
- Identify applications that rely on Active Directory authentication
- Evaluate your current group policies and how they'll translate to the cloud
- Document your current identity lifecycle processes
Migration Approaches
Microsoft offers several paths to migrate from traditional AD to Entra ID:
Staged Migration: The most common approach follows these phases:
- Deploy Azure AD Connect to synchronize identities while maintaining on-premises AD
- Implement pass-through authentication or password hash synchronization
- Gradually move applications to use Entra ID authentication
- Transition users to cloud-based identity management features
Hybrid Environment: Many organizations have maintained a hybrid identity model for years:
- On-premises AD remains the primary identity source
- Entra ID provides cloud authentication and access management
- Conditional Access policies secure both environments consistently
- Users experience a unified identity experience across platforms
Cloud Transformation: For organizations ready to fully embrace the cloud:
- Recreate your organizational structure in Entra ID
- Migrate user accounts and groups in batches
- Decommission on-premises AD after thorough testing
- Implement cloud-native identity governance
Common Challenges and Solutions
Organizations often face these challenges during migration:
Legacy Application Compatibility:
- Solution: Implement Application Proxy to provide secure access to on-premises applications without VPN
- Alternative: Maintain a slimmed-down AD infrastructure for legacy apps while using Entra ID for modern applications
Directory Complexity:
- Solution: Use Azure AD Connect filtering to manage which objects synchronize to the cloud
- Best practice: Clean up your on-premises directory before synchronization
User Experience Concerns:
- Solution: Implement a phased rollout with clear communication and training
- Tip: Start with IT staff as early adopters to identify and resolve issues
With careful planning and a phased approach, organizations can successfully transition from traditional Active Directory to Microsoft Entra ID while minimizing disruption and maximizing security benefits.
Where It Fits Within the Microsoft Ecosystem?
With a strong foundation of core identity capabilities, Microsoft Entra ID is not just an IAM tool—it is the identity framework that connects users, devices, and applications across the cloud. It extends beyond simple authentication, embedding itself into every layer of an organization's security, compliance, and hybrid IT strategy.
Powering Identity Across Microsoft 365 and Cloud Applications
Entra ID ensures that employees can move between Microsoft 365 services like Teams, SharePoint, and Exchange without repeated sign-ins, creating a frictionless user experience. Beyond Microsoft apps, its deep integration with thousands of SaaS applications allows organizations to maintain a unified identity strategy across a diverse cloud environment.
Strengthening Cloud Security with Zero Trust
As enterprises shift to the cloud, identity has become the new perimeter—and Entra ID is central to Microsoft's Zero Trust security model. Instead of assuming implicit trust within a network, every access request is continuously evaluated based on factors like user identity, device health, and risk level. This adaptive security approach ensures that:
- High-risk sign-ins are automatically blocked or require additional verification.
- Sensitive data and applications remain protected, even when accessed from personal devices or remote locations.
- Cloud security policies remain consistent across Microsoft and third-party platforms.
Extending Protection to Multi-Cloud and Hybrid Environments
Organizations rarely operate in a single-cloud ecosystem. Many use AWS, Google Cloud, or hybrid setups that still rely on on-prem Active Directory (AD). Microsoft Entra ID serves as the unifying identity provider that bridges these environments, ensuring security policies, authentication mechanisms, and access governance remain consistent, regardless of where applications and data reside.
For hybrid enterprises, Entra ID integrates with on-premises AD, allowing for a gradual transition to the cloud without disrupting existing workflows. Whether an organization is fully cloud-based or balancing legacy infrastructure with modern SaaS solutions, Entra ID provides a single source of truth for identity management.
A Central Pillar of Compliance and Governance
Beyond security, identity plays a crucial role in regulatory compliance. Entra ID simplifies the enforcement of policies required by GDPR, ISO 27001, NIST, and other global standards. Built-in identity governance capabilities ensure:
- Access reviews help remove unnecessary permissions and prevent privilege creep.
- Role-based access controls (RBAC) enforce least-privilege access across cloud workloads.
- Comprehensive audit logs provide visibility into authentication and authorization events.
With cyber threats and compliance requirements constantly evolving, Entra ID ensures that organizations stay ahead—proactively securing access while reducing the complexity of identity management.
Navigating the Admin Console: Key Features
The Entra ID Admin Console serves as the central hub for managing your organization’s identity environment. From user management to security configurations, everything is just a few clicks away.
Here’s a breakdown of the key features that make it easy for administrators to stay on top of their identity infrastructure:
Dashboard: A Glimpse at Your Tenant’s Health
The Dashboard provides an at-a-glance overview of your Entra ID tenant. From here, you can quickly assess the health of your system, monitor key metrics like risky sign-ins, and track the status of security policies. This is where you’ll see any critical issues or alerts that need your immediate attention.
Users: Managing Accounts and Access
In the Users section, you can easily add new users, reset passwords, and manage roles or licenses. It’s also where you’ll handle user lifecycle management—from onboarding new employees to offboarding when they leave.
Groups: Organizing Users for Better Access Control
Create and manage user groups in the Groups section, which helps streamline permissions management. Whether you’re organizing users by department, role, or location, groups allow you to assign specific access rights or policies to multiple users at once.
Enterprise Applications: Managing App Access and SSO
The Enterprise Applications tab is where you can configure single sign-on (SSO) for cloud-based applications. Manage who has access to apps like Salesforce, Dropbox, or Zoom, and control security settings to ensure secure access to third-party tools.
Identity Governance: Ensuring Compliance and Access Control
With the Identity Governance feature, you can set up access reviews to ensure that users have the right level of access. It’s also where you manage entitlement management, helping to reduce the risk of excessive or unnecessary access rights across your organization.
Security: Configuring Authentication and Risk Policies
In the Security section, you’ll configure authentication methods, set up multi-factor authentication (MFA), and establish risk-based conditional access rules. These policies ensure that only authorized users can access sensitive applications and data, regardless of their device or location.
Each section offers detailed configuration options while maintaining an intuitive navigation structure—a balance that administrators appreciate as they learn the system.
User and Access Management
Effective user and access management is at the heart of any strong identity strategy. By organizing, assigning, and automating user access intelligently, organizations can improve both security and administrative efficiency.
Let’s take a look at how you can manage users and their permissions in Entra ID:
Creating, Managing, and Organizing Users
A well-organized user base is essential for streamlined operations and security. Microsoft Entra ID offers several features to ensure efficient user management:
- User Creation Workflows: Whether through bulk imports, synchronization with HR systems, or self-service registration, you can onboard new employees quickly and accurately.
- Profile Management: Entra ID allows you to maintain up-to-date and accurate user profiles, including essential information like contact details, job titles, department, and location.
- License Assignment: Control access to premium services by assigning licenses based on job roles and departments, ensuring that only those who need specific tools have access.
- Group Structures: Organize users into groups, whether by department, location, or job functions, for easier permissions management.
- Administrative Units: Delegate management responsibilities for smaller subsets of users, allowing specific teams to manage their areas without overwhelming central administration.
When user management is well-structured, organizations can reduce administrative overhead and enhance security.
Role-Based Access Control (RBAC) and Permissions
Managing user permissions can be challenging, but RBAC simplifies it. Instead of manually managing each user’s access rights, you assign roles based on job responsibilities:
- Built-In Roles: Microsoft Entra ID offers pre-configured roles, like Global Administrator, User Administrator, and Security Administrator, which you can assign according to your team structure.
- Custom Roles: For specific needs, you can create custom roles with carefully defined permissions that match the unique needs of your organization.
- Privileged Identity Management (PIM): This feature allows for just-in-time access to high-privilege roles, ensuring time-bound access only when necessary.
- Least Privilege Principle: This approach ensures that users are only granted the minimum access required to perform their duties, reducing the risk of unauthorized access.
By implementing RBAC and focusing on the principle of least privilege, you can reduce security risks while ensuring that users have exactly the access they need.
Automating User Provisioning and De-provisioning
The lifecycle of an employee provides many opportunities for automation, ensuring that user access is timely and secure:
- HR-Driven Provisioning: Automatically create user accounts and assign appropriate roles when new employees join, based on their profile information.
- Attribute-Based Access: Dynamically grant application access based on job title, department, or location. This ensures that users only see the applications they need to do their jobs.
- Access Reviews: Regularly assess whether users still need their current permissions, helping you stay compliant and prevent access creep.
- De-Provisioning Triggers: When an employee leaves the organization, their access is automatically revoked, ensuring no lingering access.
- Group-Based Licensing: Assign software licenses automatically based on users' group membership, making license management much easier.
For example, one retail client reduced their access management workload by 70% after automating their user provisioning and de-provisioning workflows, while also improving security by ensuring that departed employees lost access in minutes rather than days.
Security and Compliance: Safeguarding Identities
Microsoft Entra ID provides the tools you need to safeguard your identities while maintaining compliance with industry standards.
Let's take a closer look at how you can leverage these features to protect your organization’s digital environment.
Multi-Factor Authentication (MFA) and Conditional Access: Strong, Smart Security
Multi-factor authentication (MFA) is the first defense against unauthorized access. By requiring multiple verification methods, you add a layer of protection that makes it harder for attackers to breach your systems.
- MFA Options: Microsoft Entra ID offers several MFA methods to suit your organization’s needs, including SMS, mobile app notifications, hardware tokens, and biometrics.
- Risk-Based MFA: For enhanced user experience, Entra ID offers risk-based MFA, where additional verification is only required when suspicious activity is detected—like a login attempt from an unfamiliar location.
- Conditional Access: This feature enables you to create customized security rules that evaluate multiple factors before granting access. These rules take into account:
- User identity and group membership
- Device health and compliance status
- Location and network information
- Application sensitivity
- Real-time risk detection
By combining these elements, you can intelligently enforce security, challenging users only when necessary, which enhances the user experience while ensuring high levels of protection.
Threat Detection, Risk-Based Authentication, and Compliance Features
Entra ID goes beyond just MFA and access control—it continuously monitors activity to detect suspicious behaviors and help ensure your organization stays compliant.
- Identity Protection: This tool uses machine learning to detect unusual behaviors, such as impossible travel (e.g., logging in from two countries minutes apart) or unfamiliar sign-in properties.
- Risk-Based Policies: Entra ID automatically adjusts security requirements based on the level of risk detected. For example, higher-risk sign-ins may prompt additional verification methods, like MFA or device health checks.
- Secure Score: Entra ID provides a Secure Score, offering actionable recommendations to improve your security posture and help you stay on top of best practices.
- Compliance Tooling: Entra ID helps you meet regulatory requirements with compliance tools that align with standards like GDPR, HIPAA, ISO 27001, and SOC 2.
- Comprehensive Logging: Detailed logs allow for auditing and forensic investigations in case of a security incident, helping your team trace suspicious activities and maintain accountability.
These features work together to create a dynamic, adaptive security framework that helps defend against emerging threats while ensuring compliance with regulatory standards.
Best Practices for Strengthening Identity Security
To enhance your organization’s identity security posture, adopting the following best practices can make a significant difference:
- Eliminate Passwords: Where possible, move away from traditional passwords in favor of more secure methods like FIDO2 security keys or Microsoft Authenticator.
- Implement Zero Trust: Adopt Zero Trust principles, where every access request is verified, regardless of its origin.
- Regularly Review Privileged Accounts: Make sure that only those who truly need privileged access have it—and regularly review these accounts to avoid over-provisioning.
- Monitor and Respond to Alerts: Stay vigilant by monitoring alerts and acting swiftly on any suspicious activities.
- Security Awareness Training: Empower your users by training them to recognize phishing attacks and other identity-related threats.
- Test Recovery Procedures: Ensure you have a well-tested recovery plan in place before a real emergency occurs.
Integrations and Extensibility
Microsoft Entra ID is designed to seamlessly integrate with your existing tools and workflows, creating a cohesive experience across multiple platforms.
Connecting Entra ID with Microsoft 365, Teams, and Azure
Entra ID powers authentication and authorization for a wide range of Microsoft services, ensuring that users have seamless access to critical applications:
- Microsoft 365 Integration: Entra ID enables single sign-on (SSO) across productivity tools like Outlook, Teams, SharePoint, and OneDrive. Once signed in, users can easily access all their tools without needing to authenticate repeatedly.
- Azure Resource Management: With Entra ID, you can control access to various Azure resources—from virtual machines to databases—ensuring that only authorized users have access to critical cloud infrastructure.
- Teams Governance: Manage guest access, external sharing, and meeting policies in Microsoft Teams. This ensures that your team can collaborate with others securely while keeping sensitive information safe.
- Developer Resources: Entra ID also integrates with development tools like Azure DevOps, GitHub Enterprise, and more, helping manage access across your development environments.
These integrations allow for a unified security experience, where users can access all their necessary tools with minimal friction, without sacrificing protection.
Implementing Single Sign-On (SSO) for a Seamless Experience
SSO offers a simpler way to authenticate users, reducing friction without compromising security. With Microsoft Entra ID, you can extend this convenient, secure authentication experience beyond just Microsoft tools:
- Application Gallery: Choose from thousands of pre-integrated SaaS applications to provide users with seamless access across the board.
- Integration Protocols: Entra ID supports industry standards such as SAML, WS-Federation, and OpenID Connect, enabling compatibility with a wide range of external apps.
- My Apps Portal: Users can access a personalized dashboard of all their authorized applications, providing a single location to manage app access.
- Application Proxy: For on-premises web applications, Entra ID extends SSO without exposing internal apps to the internet, maintaining both security and convenience.
- Password Vaulting: Entra ID even supports password vaulting for legacy applications that don’t support modern authentication standards, automatically filling in credentials when needed.
Implementing SSO significantly enhances both security and user satisfaction—one engineering firm reported a 40% reduction in password reset tickets within just three months of implementation.
Managing External Users and B2B Access
Entra ID securely manages these relationships while protecting sensitive data:
- B2B Collaboration: Invite external partners, vendors, and customers to access specific resources securely, using their own identities.
- Self-Service Sign-Up: Enable external users to register through custom flows, reducing the administrative burden on your IT team.
- Access Reviews: Regularly review and confirm whether external users still require access, helping ensure compliance and security.
- Conditional Access for Guests: Apply appropriate security policies to external identities, ensuring that they meet your organization's security standards.
- Cross-Tenant Access: Easily control how your organization interacts with other Entra ID tenants, managing permissions and collaboration across different environments.
These features allow for secure collaboration without compromising security, enabling you to work closely with external teams while maintaining the necessary boundaries and controls.
Advanced Applications of Microsoft Entra ID
Hybrid and Multi-Cloud Identity Management
Entra ID simplifies identity management across various infrastructures, whether on-premises or in the cloud. Here's how it works:
- Hybrid Identity: For businesses with both on-premises and cloud-based resources, Entra ID integrates seamlessly with on-premises Active Directory, providing a unified identity management experience across your entire infrastructure.
- Multi-Cloud Strategies: Entra ID extends its protection to other major cloud platforms, including AWS and Google Cloud, ensuring consistent access controls regardless of where your resources are hosted.
- Cloud-to-Cloud Scenarios: Manage access to applications and services spread across different cloud platforms, ensuring secure and streamlined workflows.
- Hybrid Security Models: Entra ID applies consistent security policies across all environments—whether cloud, on-prem, or hybrid—allowing you to maintain a strong security posture as your organization’s technology landscape evolves.
With Entra ID, organizations can create flexible, yet secure environments that scale across various platforms without compromising security.
Secure Access for Contractors, Vendors, and Partners
In today’s business world, collaboration extends beyond company walls. Entra ID ensures that external users, like contractors or partners, have the access they need without compromising security. Key features include:
- Just-In-Time Access: Grant access only when needed, reducing the risk of over-privileged accounts.
- Workflow Approvals: Require managerial sign-off before granting sensitive access, ensuring control over who gets access to what.
- Time-Bound Permissions: Automatically revoke access after a specific period, ensuring external users can’t access your resources beyond the necessary timeframe.
- Activity Monitoring: Track and analyze unusual behaviors from external accounts to detect potential security threats in real-time.
- Segregated Access Paths: Limit contractors or partners to specific resources, preventing unauthorized access to other areas of the network.
These measures allow organizations to maintain secure collaboration with external partners while mitigating risks associated with non-employee access.
Customization and Automation with PowerShell
For advanced administrators, PowerShell offers a powerful way to customize and automate Microsoft Entra ID tasks, streamlining management at scale. Here’s how it can be used:
- Bulk Operations: Manage large numbers of users, groups, or applications efficiently through automated scripts, reducing manual effort.
- Custom Reporting: Generate customized reports to meet specific needs that go beyond the default reports provided in the Entra ID admin center.
- Scheduled Tasks: Automate routine tasks like user provisioning or security checks, reducing the administrative burden and improving consistency.
- Integration with Other Systems: Connect Entra ID to custom applications or workflows, ensuring your identity management system integrates with the rest of your IT environment.
- Tenant Management: Administer multiple Entra ID tenants across different environments with consistent processes, ensuring streamlined management at scale.
By using PowerShell, organizations can fully customize their Entra ID experience to meet specific needs, creating a tailored solution that fits their infrastructure and business goals.
Real-World Implementation
Organizations across industries are leveraging Entra ID to enhance their security posture while optimizing operational efficiency.
Here are some real-world examples:
- Financial Services: A global bank implemented risk-based authentication using Entra ID, analyzing over 100 risk signals before granting access to sensitive systems. This proactive approach not only blocked thousands of credential-based attacks but also reduced friction for legitimate users, improving the overall user experience and minimizing the impact on productivity.
- Healthcare: A hospital network used Entra ID’s governance features to automate access reviews, ensuring compliance with HIPAA regulations. By streamlining this process, they reduced audit preparation time by 60%, freeing up resources for critical patient care and minimizing the chance of non-compliance due to manual errors.
- Retail: A multinational retailer deployed conditional access policies across 2,000 point-of-sale (POS) locations to secure customer transactions. This solution prevented unauthorized access even when credentials were compromised, ensuring data integrity and preserving customer trust, a key asset in the highly competitive retail space.
- Education: A university system introduced self-service password resets and multi-factor authentication (MFA) for 50,000 students and faculty. As a result, they saw a 35% reduction in help desk calls during peak enrollment periods, enabling their IT staff to focus on more critical tasks while enhancing the overall user experience for students and faculty.
Overcoming Challenges in Large-Scale Identity Management
While the benefits of modern identity management are clear, organizations often face challenges during large-scale deployments. Here’s how they overcome common obstacles:
- Legacy Application Integration: Many organizations have successfully modernized legacy applications by leveraging custom connectors or integrating hybrid cloud solutions, bringing older apps into the Entra ID ecosystem without compromising on security or functionality.
- Cultural Resistance to Change: Resistance to new security measures is often a major barrier. To address this, organizations have implemented change management strategies that clearly communicate the direct benefits to users, such as easier access, faster logins, and enhanced personal security, which fosters quicker adoption.
- Complex Organizational Structures: For enterprises with complex hierarchical structures, Entra ID offers custom roles and administrative units, allowing for secure delegation of responsibilities while respecting the organization’s boundaries. This ensures that each department or unit has the right level of control without jeopardizing overall security.
- Mergers & Acquisitions: When consolidating identity systems following a merger or acquisition, enterprises have adopted methodical approaches to tenant consolidation that ensure a smooth transition without compromising security. Proper planning for user migration, role redefinition, and system integration is crucial to maintain operational continuity.
By addressing these challenges with clear planning, executive buy-in, and tailored solutions, organizations ensure their identity management systems remain resilient, scalable, and secure.
Lessons Learned from Real-World Deployments
Experienced practitioners share these insights:
- Start with fundamentals: Ensure basic security measures like MFA are fully implemented before moving to advanced scenarios.
- Measure success: Track metrics like reduced password resets, faster onboarding times, and prevented security incidents.
- Invest in training: Both IT staff and end users need appropriate education to maximize benefits.
- Plan for scale: Architecture decisions should anticipate future growth in users, applications, and complexity.
- Build cross-department partnerships: Successful identity programs involve collaboration between IT, security, HR, and business units.
These lessons represent the collective wisdom of organizations that have successfully navigated the journey to modern identity management.
Troubleshooting and Continuous Optimization
Common Issues and How to Resolve Them?
Even the best-designed systems can encounter challenges. Understanding and efficiently addressing common issues is key to minimizing disruptions and maintaining a secure environment. Here’s how to resolve some frequent problems:
- Sign-in Problems:
Ensure accounts are not blocked, confirm that Multi-Factor Authentication (MFA) devices are properly configured, and review Conditional Access policies for potential restrictions. These steps can help identify why users might be having trouble signing in and streamline the resolution process. - Synchronization Errors:
Common causes of synchronization issues include connectivity problems, incorrect permissions, or data inconsistencies. Diagnosing the root cause involves checking service health, reviewing sync logs, and verifying permissions and data mappings to ensure consistency across systems. - Application Access Failures:
Verify that the service principal configurations are accurate, consent grants are in place, and certificates haven’t expired. Any misconfiguration in these areas can prevent access to critical applications, so a thorough check is essential. - Policy Conflicts:
Conflicting Conditional Access rules or permissions can block legitimate user access. To resolve this, carefully audit and adjust policies to ensure they align and don’t inadvertently prevent authorized users from accessing necessary resources. - License Assignment Issues:
Confirm that the appropriate licenses are available and correctly assigned to users or applications. Insufficient or incorrect license assignments can lead to functionality gaps or access issues that hinder user productivity.
Having structured, methodical approaches to diagnosing and resolving these common issues ensures that your identity management system stays reliable and users experience minimal disruption.
Monitoring, Reporting, and Performance Optimization
Ongoing monitoring and proactive performance optimization are critical for maintaining a healthy identity environment. Here are some best practices to ensure everything runs smoothly:
- Operational Monitoring:
Regularly track metrics like authentication success rates, latency, and service availability to spot any signs of system strain or disruptions. This enables you to detect and address issues before they affect end users. - Security Monitoring:
Actively watch for anomalous activity such as repeated failed authentication attempts, suspicious login locations, or unexpected privileged access requests. Early detection of these patterns can help mitigate security risks before they escalate. - Compliance Reporting:
Create regular reports to demonstrate compliance with regulatory standards. Ensuring timely and accurate documentation for audits is crucial for staying aligned with data protection laws, such as GDPR or HIPAA. - Capacity Planning:
Anticipate future growth by continuously analyzing resource usage. This allows you to scale your infrastructure and identity management resources as needed, preventing bottlenecks and ensuring scalability. - Performance Optimization:
Regularly fine-tune configurations to maximize performance. Optimizing the speed, reliability, and responsiveness of your identity management processes helps maintain a smooth user experience even as usage scales.
By proactively monitoring key metrics, reviewing performance data, and planning for future growth, you ensure that your identity management system remains secure, efficient, and scalable.
Leveraging Microsoft Support and Community Resources
No organization needs to solve identity challenges alone:
- Microsoft Support: Access professional assistance through support plans.
- Technical documentation: Reference detailed guides in the Microsoft Learn library.
- Community forums: Connect with peers facing similar challenges.
- User groups: Participate in local and virtual meetings to share experiences.
- Partner ecosystem: Engage specialized consultants for complex implementations.
These resources provide valuable guidance for both everyday questions and unusual scenarios.
Setting Up Microsoft Entra ID: A Step-by-Step Guide
Getting started with Microsoft Entra ID is a straightforward process, especially if your organization is already using Microsoft 365 or Azure. Whether you’re migrating from an existing identity provider or setting up a new cloud-based directory, the key is to plan your identity model and security policies from the beginning.
Step 1: Access Your Entra ID Tenant
If your organization uses Microsoft 365 or Azure, you already have an Entra ID tenant. You can find it in the Azure portal under Microsoft Entra ID. If you’re starting from scratch, you can create a new tenant in just a few clicks.
Step 2: Define Your Identity Model
Before adding users, decide how Entra ID will manage identities:
- Cloud-Only: Users and identities exist only in Microsoft Entra ID, ideal for cloud-native organizations.
- Synchronized (Hybrid): Identities are synced from an on-premises Active Directory (AD), allowing organizations to maintain their existing directory while leveraging cloud capabilities.
- Federated: Authentication happens on-premises (e.g., using Active Directory Federation Services), while authorization and access management occur in the cloud.
Choosing the right model ensures seamless authentication and access control based on your infrastructure.
Step 3: Configure Your Domain
To create a consistent sign-in experience, add and verify your custom domain (e.g., yourcompany.com) in Entra ID. This ensures that employees can log in with familiar email addresses instead of Microsoft-assigned domain names.
Step 4: Structure Your Users, Groups, and Roles
A well-organized group and role structure simplifies access control and security policies. Consider:
- User Groups: Organize employees based on departments, job roles, or locations.
- Administrative Roles: Assign RBAC (Role-Based Access Control) to grant appropriate permissions without over-provisioning.
- Guest Users: Configure external identities if working with partners or vendors.
Step 5: Establish Security Baselines
Before onboarding users, set up foundational security policies:
- Password Policies: Define complexity requirements and expiration rules.
- Multi-Factor Authentication (MFA): Require additional verification for high-risk sign-ins.
- Conditional Access Policies: Control access based on user, location, and device security posture.
With these initial configurations in place, your Microsoft Entra ID setup is ready to scale securely while ensuring a smooth user experience.
Best Practices for a Smooth Deployment
Successful Entra ID deployments follow these proven practices:
- Start with a pilot: Test with a small group before rolling out widely.
- Communicate clearly: Help users understand what's changing and why it matters.
- Take a phased approach: Begin with basic functionality and add more advanced features as your team becomes comfortable.
- Document your decisions: Keep records of configuration choices and the reasoning behind them.
- Plan for support: Prepare your help desk with training and troubleshooting guides.
- Monitor adoption: Track usage metrics to identify areas needing attention.
Microsoft Entra ID vs. Alternatives
| Feature/Criteria | Microsoft Entra ID | Okta | Google Cloud Identity | AWS IAM |
| Best For | Microsoft 365, Azure, hybrid & enterprise environments | Diverse, multi-cloud environments | Google Workspace, Android-based organizations | AWS-centric identity management |
| Native Integration | Microsoft 365, Azure, Teams, Defender | Works well across various third-party apps | Best with Google services (GCP, Workspace) | Deep integration with AWS services |
| Pricing | Included in Microsoft 365 plans + premium tiers | Standalone pricing, can be costly for MS users | Generally affordable for Google-centric businesses | Free for AWS, but lacks broader IAM tools |
| Ease of Implementation | Seamless for Microsoft users, hybrid-ready | Flexible but requires more third-party configurations | Simple for Google ecosystems, but lacks enterprise depth | Designed specifically for AWS users |
| Security Features | Conditional Access, MFA, Risk-based authentication, AI-driven threat detection | Strong MFA, adaptive authentication | Basic MFA, good for Google apps but limited enterprise security | Strong AWS security, but lacks broader IAM controls |
| Hybrid Identity Support | Excellent support for on-prem & cloud (Active Directory) | Cloud-first, limited on-prem integration | Mostly cloud-based, weak hybrid support | Focused on AWS-only environments |
| SSO & Access Management | Comprehensive SSO, role-based & attribute-based access controls | Powerful SSO & adaptive access | Decent SSO, but not as robust as others | Role-based access, but lacks enterprise SSO support |
| Identity Governance & Compliance | Privileged Identity Management (PIM), detailed auditing, regulatory compliance | Strong compliance features, but separate add-ons | Basic compliance tools, lacks enterprise governance | AWS-focused governance, less flexible for external apps |
| Cross-Platform Support | Supports Microsoft, third-party, and hybrid apps | Works across multi-cloud & SaaS platforms | Best for Google & Android apps, limited elsewhere | Limited to AWS, less flexibility for external apps |
| Scalability & Reliability | Enterprise-grade, backed by Microsoft’s global cloud infrastructure | Highly scalable across multiple environments | Good for Google ecosystem, not optimized for large enterprises | Reliable for AWS workloads, but not ideal for general IAM needs |
| AI & Threat Intelligence | AI-driven security insights, integrates with Microsoft Defender & Sentinel | Strong security analytics, but less AI-driven | Limited AI security features | Good security, but lacks real-time AI-driven threat intelligence |
The Future of Identity Management with Microsoft Entra ID
Emerging Trends in Identity Security and Zero Trust Architecture
The identity landscape continues to evolve:
- Passwordless authentication is becoming the default rather than an exception.
- Continuous authentication evaluates trust throughout a session, not just at login.
- Decentralized identity approaches give users more control over their personal data.
- AI-powered security detects increasingly sophisticated attack patterns.
- Zero Trust architecture eliminates implicit trust based on network location.
Organizations that understand these trends can anticipate changes rather than reacting to them after the fact.
Microsoft's Roadmap and Vision for Identity Management
Microsoft has outlined an ambitious path forward:
- Expanded threat intelligence sharing across the Microsoft security ecosystem.
- Enhanced verification technologies beyond traditional authentication factors.
- Deeper integration between identity and endpoint security.
- Simplified governance for complex regulatory environments.
- Streamlined hybrid experiences for organizations maintaining on-premises systems.
These developments reflect Microsoft's commitment to identity-centered security as the foundation of its broader cybersecurity strategy.