1. Introduction to Amazon Systems Manager (SSM)
What is Amazon Systems Manager (SSM)?
Amazon Systems Manager (SSM) is an integrated management service offered by AWS to automate and manage infrastructure tasks on AWS environments. It helps you centrally control your resources and enables automated management of virtual machines (VMs), applications, and other systems across AWS and hybrid environments. Systems Manager is designed to simplify day-to-day operations, such as configuration management, patching, monitoring, and troubleshooting, reducing manual efforts and improving operational efficiency.
SSM integrates with a wide variety of AWS services to offer end-to-end infrastructure management. It can be used to perform tasks like managing software inventory, executing remote commands, ensuring compliance, and automating operational tasks such as patching.
Key Benefits of Using SSM
- Simplified Management: SSM allows you to manage all your AWS resources from a single, unified interface. You can automate configuration changes and monitor system health, making infrastructure management simpler.
- Operational Efficiency: By automating routine tasks like software patching, instance management, and inventory collection, SSM saves time and reduces human error.
- Secure Remote Access: With tools like Session Manager, you can access your instances securely without needing to open SSH ports or rely on traditional remote access methods.
- Improved Compliance: SSM helps maintain system configurations according to your organization’s security policies by automatically applying and enforcing them. It also provides reporting features to track compliance status.
- Cost Reduction: By automating tasks and reducing manual intervention, SSM helps optimize operations, which can reduce costs related to IT management and operational overhead.
How SSM Helps in Managing AWS Infrastructure
SSM simplifies the complexity of managing AWS infrastructure by allowing you to:
- Automate common administrative tasks like patching, instance configuration, and software installation.
- Gain insights into your resources by viewing detailed configuration data and performing automated health checks.
- Ensure consistency across your infrastructure with tools like State Manager, which allows you to define desired system configurations and ensure they are maintained.
- Remotely troubleshoot and access instances securely using Session Manager, avoiding the need for open ports or VPNs.
2. Core Components of Amazon Systems Manager
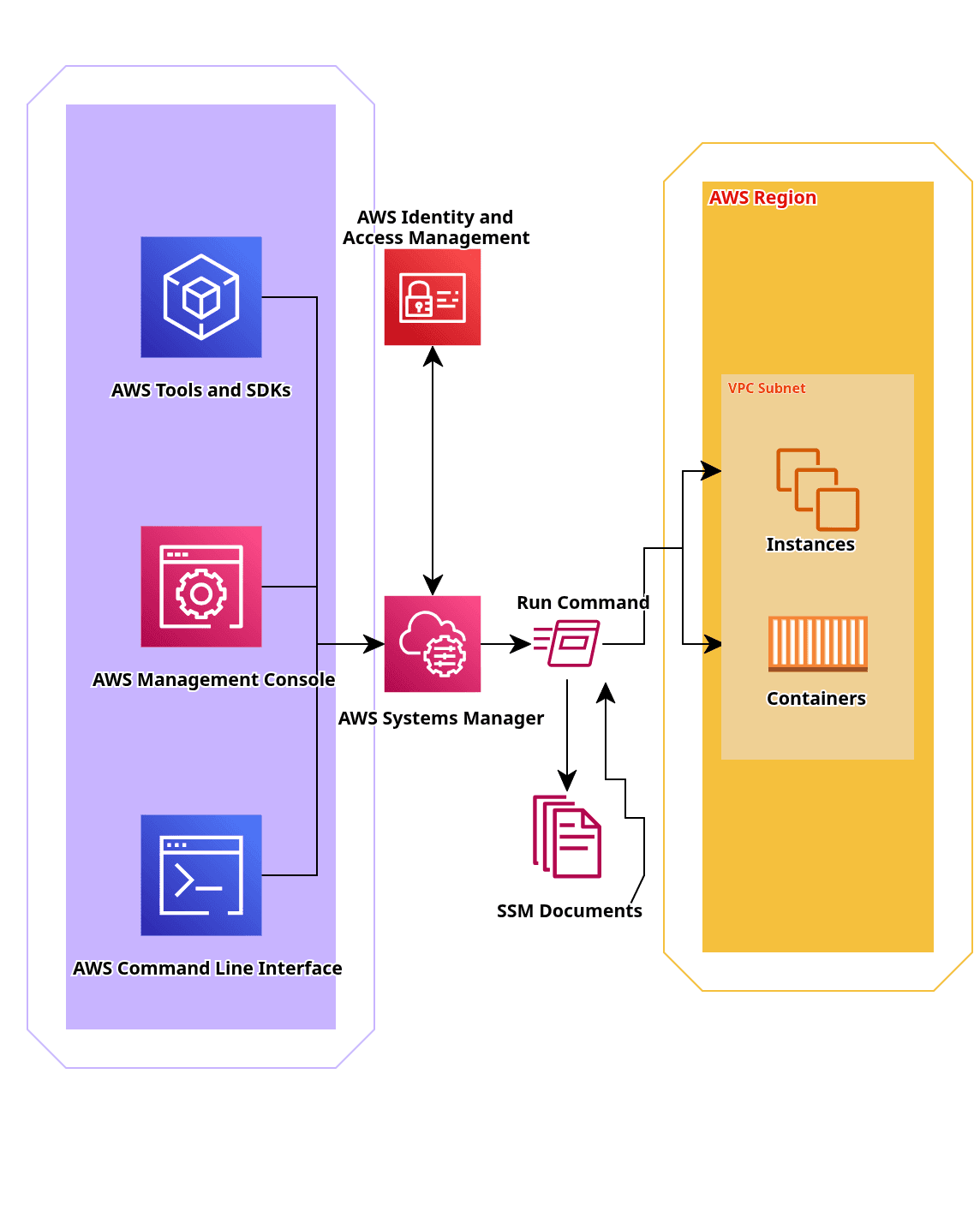
To understand how SSM works, it's essential to first get familiar with its key components. These components help streamline management, automation, and control over your AWS infrastructure.
Systems Manager Agent (SSM Agent)
The SSM Agent is a lightweight software installed on your EC2 instances and on-premises servers. It communicates with the SSM service to execute tasks such as patching, running commands, and gathering system information. The agent sends and receives requests from AWS Systems Manager, and it plays a vital role in enabling remote management.
Managed Instances
A managed instance is any resource (EC2 instance, on-premises server, or hybrid server) that has the SSM Agent installed and is actively managed by SSM. These instances can be configured, patched, and monitored using Systems Manager. You can view and manage managed instances directly from the Systems Manager console.
SSM Documents (Runbooks, Command Documents)
SSM Documents define the actions that can be performed on managed instances. They serve as templates for automation and task execution.
- Command Documents: These are used to execute specific commands or scripts on managed instances.
- Runbooks: These are a series of steps designed to automate complex workflows. Runbooks are key for automating operations like patch management, backups, and deployments.
Maintenance Windows
Maintenance Windows allow you to define time periods when certain tasks (e.g., patching or updates) should be applied to your managed instances. You can schedule these windows during off-hours to minimize the impact on system performance or business operations.
State Manager
State Manager is a feature of SSM that allows you to define and enforce a desired state configuration for your managed instances. For instance, you can specify that certain software versions or settings must be present on all instances and automatically apply those configurations to maintain consistency across your infrastructure.
Automation
Automation is the heart of operational workflows in Systems Manager. With Automation, you can create runbooks to automate complex tasks like instance patching, server configuration, and even scaling infrastructure. Automation eliminates the need for manual intervention, allowing you to build efficient and repeatable processes.
3. Setting Up Amazon Systems Manager
To begin using Amazon Systems Manager, there are several prerequisites and setup steps that need to be followed.
Prerequisites for Using SSM
Before you can use Systems Manager effectively, ensure that:
- You have an AWS account with appropriate permissions.
- The EC2 instances or on-premises servers you wish to manage have network connectivity to AWS (via the internet or through a VPC endpoint).
- The SSM Agent is installed on your instances (either EC2 or on-premises).
- You have configured your IAM roles and policies correctly to ensure SSM can interact with your resources.
Enabling Systems Manager in AWS Console
To enable SSM in your AWS environment, navigate to the AWS Management Console and access the Systems Manager service. From here, you can configure various tools and settings such as Patch Manager, Session Manager, and Automation. Enabling these features in your account is as simple as selecting the respective tools and configuring them according to your needs.
Setting IAM Roles and Permissions
Amazon SSM relies on AWS Identity and Access Management (IAM) to define what actions a user or service can perform. To use SSM effectively:
- Ensure that the necessary IAM roles are assigned to users, services, and managed instances.
- For instance, an EC2 instance needs to have an IAM role with appropriate policies (like AmazonSSMManagedInstanceCore) to allow SSM to interact with it.
- Similarly, for human users, specific permissions need to be granted to interact with Systems Manager through the AWS Console or API.
Installing and Configuring SSM Agent on EC2 Instances
For EC2 instances to be managed by SSM, you need to install the SSM Agent. In many AWS AMIs, the agent comes pre-installed, but for custom AMIs or on-premises systems, you must manually install it. You can install the agent using the AWS Systems Manager documentation, which provides detailed steps for different operating systems like Linux and Windows.
Once installed, ensure that the agent is running and properly communicating with the SSM service. You can verify this from the Systems Manager console by checking the "Managed Instances" section.
4. Key Features of Amazon SSM
Amazon Systems Manager offers a rich set of features designed to simplify AWS infrastructure management, improve security, and automate operational tasks.
Automation and Runbooks
Automation in SSM allows you to create and manage runbooks, which are predefined workflows designed to perform complex tasks with minimal human intervention. These tasks could range from patching EC2 instances to rotating secrets in Parameter Store.
Runbook Example:
| Action | Description |
| Step 1: Check Instance Health | Verify the health of the EC2 instance before proceeding with updates. |
| Step 2: Apply Patches | Automatically apply the latest patches based on defined baselines. |
| Step 3: Reboot Instance | Reboot the instance if necessary after patching. |
By automating these tasks, you can ensure that your systems remain compliant and up-to-date without manual oversight.
Patch Management and Compliance
Patch Manager allows you to automate the patching process for your managed instances. You can define patch baselines to specify which patches should be applied and when. Systems Manager then applies these patches automatically during predefined maintenance windows.
Patch Compliance Table:
| Instance ID | Patch Status | Last Patch Applied | Compliance Status |
| i-123abc456 | Success | 2025-02-01 | Compliant |
| i-789def012 | Failed | 2025-01-25 | Non-Compliant |
Using Patch Manager ensures that your EC2 instances remain compliant with security standards, reducing the risk of vulnerabilities.
Session Manager for Secure Remote Access
Session Manager allows you to securely access EC2 instances without the need for SSH or RDP. This improves security by eliminating the need for open inbound ports. Sessions are logged, providing a detailed audit trail for access.
Key Features of Session Manager:
- Secure access without opening ports or configuring VPNs.
- Encrypted session connections.
- Detailed session logging for auditing purposes.
Parameter Store for Configuration Management and Secrets Storage
Parameter Store is a service within SSM that allows you to securely store and manage configuration data, secrets, and parameters such as API keys and database credentials. You can store parameters in plaintext or encrypt them with AWS KMS for extra security.
Example:
- Parameter Name: /app/db-password
- Value: (Encrypted string)
By using Parameter Store, you can centralize the management of sensitive data and integrate it directly into your applications.
Inventory Management and Software Inventory
SSM can automatically collect software inventory from your managed instances, including information about installed applications, patches, and configurations. This feature is particularly useful for auditing, compliance, and reporting.
Inventory Table:
| Instance ID | Installed Software | Version | Last Updated |
| i-abc123456 | Apache HTTP Server | 2.4.46 | 2025-02-12 |
| i-xyz987654 | MySQL Database | 8.0.23 | 2025-01-15 |
This helps you maintain a comprehensive inventory of your infrastructure’s software and system configurations.
5. Working with EC2 Instances Using SSM
Running Commands on EC2 Instances
Amazon Systems Manager provides several methods for executing commands on EC2 instances without needing SSH access or exposing ports. This is particularly useful for administrators who need to perform routine maintenance tasks or troubleshoot issues remotely.
You can run commands using the Run Command feature in Systems Manager. This allows you to execute predefined scripts or custom commands across multiple EC2 instances at once.
How to Run Commands:
- Navigate to the Run Command section in the AWS Systems Manager console.
- Choose the EC2 instances (or managed instances) on which you want to execute the command.
- Select a predefined document or create your own custom command.
- Specify the parameters (such as command arguments) and run the command.
This can be used for various tasks such as:
- Installing software updates
- Running diagnostic scripts
- Modifying configuration files
Example:
| Command Name | Description | Instances Affected |
| Install Apache Server | Installs Apache HTTP server on EC2 instances. | i-abc123456, i-xyz987654 |
| Run Diagnostic Script | Executes a diagnostic script for server health check. | i-abc123456 |
Managing EC2 Instance Configuration with SSM
SSM also simplifies managing EC2 instance configurations. Through State Manager, you can define a desired state for your EC2 instances. For example, you can ensure that all instances in a specific environment have a certain version of a software package or a specific configuration file.
State Manager helps maintain this desired configuration by continuously monitoring the state of the instance and applying changes when needed.
Example Configuration Task:
- Ensure that the latest version of nginx is installed on all instances in a production environment.
- Ensure the system's timezone is set to UTC across all instances.
SSM enables you to automate these configuration tasks, reducing manual configuration errors and increasing consistency across your EC2 fleet.
Using EC2 Instance as a Managed Instance
An EC2 instance becomes a Managed Instance in Systems Manager once the SSM Agent is installed and the necessary IAM permissions are in place. This allows SSM to manage and interact with the instance for various tasks like executing commands, patching, and inventory collection.
You can view and manage managed instances directly in the Systems Manager console. Managed instances give you greater control over configuration management, patching, and security, while also enabling easier troubleshooting without the need for direct access to the EC2 instance.
6. SSM Automation: Streamlining Operations
Introduction to Automation in SSM
Automation is one of the key features of Amazon Systems Manager. It helps automate repetitive tasks, thereby saving time and reducing human errors. Automation in SSM is typically implemented using Automation Runbooks—predefined workflows that describe how to perform a task or series of tasks.
These runbooks can automate tasks such as:
- Patching systems
- Configuring software
- Restarting services
- Managing backups
Automation simplifies operations by making processes repeatable and removing the need for manual intervention, leading to more consistent and reliable system operations.
Creating and Executing Automation Runbooks
Creating automation runbooks involves defining the actions you want to automate using SSM’s Automation Documents. These documents are made up of a series of steps or actions, each of which is designed to perform specific tasks on EC2 instances or other resources.
Steps to Create a Runbook:
- Define the task you want to automate (e.g., apply security patches).
- Create an Automation Document (runbook) and outline the steps.
- Define the conditions under which the automation should run (e.g., only during off-hours).
- Test the runbook to ensure it performs the desired actions.
- Execute the runbook on the desired resources.
Runbooks can be triggered manually or automatically based on events, like instance health or a scheduled maintenance window.
Example Runbook:
| Step | Action | Resource Affected |
| 1 | Apply security patches | i-abc123456 |
| 2 | Restart EC2 instance to apply patches | i-abc123456 |
| 3 | Notify system administrator of completed task | [email protected] |
Automation Best Practices
While automation is highly efficient, there are a few best practices to follow:
- Test Runbooks: Always test automation runbooks in a staging environment to ensure that they perform as expected.
- Error Handling: Include error-handling steps in runbooks to ensure that failure points are properly managed and logged.
- Logging and Notifications: Enable logging and notifications for automation tasks to track their success and troubleshoot any issues.
- Version Control: Maintain versions of your runbooks, especially for complex workflows, so that you can track changes and rollback when necessary.
Advanced Use Cases for Automation (e.g., Auto-scaling, Backup Operations)
Automation in SSM can be extended to advanced use cases:
- Auto-scaling: Create runbooks that automatically adjust the number of EC2 instances based on load. For example, a runbook could monitor CPU usage and scale up or down when thresholds are met.
- Backup Operations: Automate regular backup of critical data using SSM runbooks, ensuring that backups happen consistently without manual intervention.
Troubleshooting Automation Workflows
If an automated workflow fails, troubleshooting is key to ensuring operations continue smoothly. Common troubleshooting steps include:
- Reviewing logs in Amazon CloudWatch to identify what went wrong.
- Checking error handling steps in your runbook to see if a failure condition was properly defined.
- Manually running parts of the automation to isolate and resolve issues.
7. Managing Patches and Maintenance
Introduction to Patch Manager
Patch Manager in SSM automates the process of applying patches to your EC2 instances, ensuring that your instances are up-to-date and secure. Patches can be related to both the OS (e.g., security updates) and software applications running on the instances.
Patch Manager integrates with SSM to automatically apply patches according to pre-configured patch baselines. It also allows you to schedule patching tasks during specific maintenance windows, minimizing disruption.
Creating and Managing Patch Baselines
A patch baseline defines which patches should be applied to your managed instances and under what conditions. You can create custom patch baselines based on your organization’s requirements (e.g., apply only critical security patches).
Steps to Create a Patch Baseline:
- Navigate to the Patch Manager section in the Systems Manager console.
- Define a patch baseline, specifying criteria such as patch type (security, critical, etc.) and severity.
- Assign the baseline to specific EC2 instances or groups of instances.
Example Patch Baseline:
| Patch Type | Description |
| Security | Apply only security-related patches |
| Critical | Apply critical updates for OS and software |
| Non-Essential | Only apply non-essential updates if resources allow |
Using Maintenance Windows for Scheduled Patching
Maintenance windows allow you to define specific periods during which patching and other maintenance tasks should be executed. This ensures that patches are applied at times when they won't impact system performance or availability.
You can schedule patching during low-traffic hours to ensure minimal disruption. Systems Manager will automatically apply patches to instances during these windows.
Monitoring Patch Compliance and Health
Once patches are applied, it's important to monitor patch compliance to ensure all instances are up-to-date and compliant with your patching policies. Systems Manager provides a comprehensive Patch Compliance dashboard that shows the status of all your instances, including which patches have been applied and which are pending.
8. Parameter Store and Secrets Manager
Overview of Parameter Store
Parameter Store is an AWS service that helps you manage configuration data, such as API keys, database credentials, and other sensitive information. It offers a centralized storage location for configuration parameters, making it easy to manage, retrieve, and secure application settings.
Managing Configuration Data with Parameter Store
With Parameter Store, you can:
- Store values as plain text or encrypted using AWS Key Management Service (KMS).
- Organize parameters in a hierarchy for better organization.
- Retrieve parameters programmatically in your applications to configure environments.
Example Parameter:
| Parameter Name | Value | Encryption | Description |
| /app/db-password | mySecretPassword123 | Encrypted | Database password |
Using Parameter Store to Securely Store Secrets
Sensitive data, such as API keys or database credentials, should never be hard-coded or stored in plain text. Parameter Store allows you to securely store these secrets and retrieve them on demand, using AWS KMS to encrypt the data.
Integrating Parameter Store with Applications
By integrating Parameter Store into your application, you can automate the retrieval of configuration data, ensuring that your application always has the most up-to-date values. Parameter Store can be accessed via the AWS SDK or AWS CLI, allowing seamless integration with your systems.
Secrets Manager: Advanced Secret Management
While Parameter Store provides secure storage for basic configuration data, Secrets Manager is designed specifically for managing sensitive secrets. It allows you to rotate secrets automatically (e.g., database passwords) and integrate them into applications securely.
With Secrets Manager, you can:
- Automatically rotate secrets without downtime.
- Audit access to secrets using AWS CloudTrail.
- Integrate with applications to retrieve secrets programmatically.
9. Remote Access with Session Manager
Introduction to Session Manager
AWS Session Manager is a powerful tool that allows secure, auditable remote access to your Amazon EC2 instances and on-premises servers. One of the best features is that you can access your instances without opening traditional remote access ports like SSH (port 22) or RDP (port 3389). This makes it more secure and reduces the potential attack surface for your infrastructure.
Key Highlights of Session Manager:
- Secure access without open inbound ports.
- Full logging and auditing with CloudTrail.
- No need for external tools like SSH or RDP.
Secure Remote Access to Instances Without Open Ports
Unlike traditional SSH and RDP access, which require open ports on your EC2 instances, Session Manager allows you to securely connect to instances without any open ports. This minimizes your security risk by preventing unauthorized access to your instances.
Why is this important?
- Security: No open ports means a reduced attack surface.
- Encryption: Session data is encrypted, ensuring your communications are secure.
- No extra software needed: You don’t need third-party tools for remote access.
How to use Session Manager:
- Go to the AWS Systems Manager Console.
- Navigate to Session Manager.
- Select the EC2 instance you want to connect to.
- Click Start Session.
Monitoring and Auditing Sessions
All actions during a session are logged for auditing and security purposes. With CloudTrail and CloudWatch Logs, you can monitor all session activities.
| Feature | Description |
| CloudTrail Logging | Captures details of each session, including commands run and user activities. |
| CloudWatch Logs | Helps you monitor real-time session activities for deeper insights. |
This makes it easier to:
- Audit user activity.
- Maintain compliance with industry regulations.
- Identify any unauthorized access.
Use Cases for Secure Access (e.g., Disaster Recovery, Maintenance)
Here are some key scenarios where Session Manager can be extremely beneficial:
| Use Case | Description |
| Disaster Recovery | In case of an outage, access your instances without SSH or RDP for quick troubleshooting. |
| Maintenance | Perform tasks like patching or updates securely without needing to open access ports. |
| Compliance | Use Session Manager to adhere to compliance regulations by tracking access in detail. |
10. Inventory Management in SSM
Using SSM to Collect and Organize Instance Inventory
Amazon SSM's Inventory Management feature automatically collects metadata from your EC2 instances and on-premises servers. It gathers useful details about the instance, such as installed software, OS configurations, and more.
This feature enables you to:
- Maintain an organized inventory of your infrastructure.
- Automate inventory collection across thousands of instances.
| Inventory Item | Description |
| Software Installed | List of software packages on an instance. |
| OS Configuration | Information about the operating system (e.g., version, build). |
| Network Settings | Configuration data like IP address, subnet, etc. |
You can view and organize inventory in the Systems Manager Console, simplifying the process of tracking your infrastructure.
Querying and Reporting Inventory Data
Once the inventory is collected, you can query the data to find specific details or generate reports. This is useful for:
- Software compliance: Ensure that the right software is installed.
- Configuration management: Track configuration drift and ensure consistency.
For example, a query could return a list of instances running a specific version of a software package:
| Instance ID | Installed Software | OS Version | Last Configured |
| i-abc123456 | Apache, MySQL | Ubuntu 20.04 | 2025-02-10 |
| i-xyz987654 | Nginx, PostgreSQL | Windows 2019 | 2025-02-11 |
Integrating Inventory Management with Other AWS Services (e.g., Config, CloudWatch)
SSM Inventory integrates seamlessly with other AWS services:
- AWS Config: Track and record configuration changes over time.
- Amazon CloudWatch: Monitor changes and set up alarms when specific conditions are met.
- AWS Lambda: Automatically trigger actions based on inventory changes.
This integration allows you to:
- Maintain historical configuration data.
- Automate responses to inventory changes.
11. Security and Compliance with Amazon Systems Manager
Securing SSM Operations and Protecting Data
Security is a cornerstone of AWS Systems Manager. Here’s how it protects your data and ensures your operations are secure:
- IAM Roles and Policies: Use fine-grained access controls to limit who can access which systems and features within SSM.
- Encryption: All communications and stored data are encrypted using AWS KMS.
- CloudTrail: Logs all actions taken within SSM for auditing purposes.
| Security Feature | Description |
| IAM Roles/Policies | Control access to systems and resources within SSM. |
| Encryption (KMS) | Ensure all data in transit and at rest is encrypted. |
| CloudTrail Logging | Provides audit logs of all actions performed within SSM. |
These measures help maintain a secure, compliant environment.
Best Practices for Configuring IAM Roles and Policies
When configuring IAM roles and policies for Systems Manager, consider the following best practices:
- Principle of Least Privilege: Only grant the minimum permissions needed to perform tasks.
- Use Managed Policies: AWS provides default managed policies for common roles, which can simplify access management.
- Cross-Account Access: If you have multiple AWS accounts, configure cross-account roles to grant specific access.
| Best Practice | Explanation |
| Least Privilege | Only assign permissions necessary for tasks. |
| Managed Policies | Use predefined policies for common roles. |
| Cross-Account Access | Enable secure management of resources across multiple AWS accounts. |
Auditing SSM Activity with CloudTrail
All Systems Manager activities are logged in AWS CloudTrail. These logs can help you track:
- Who accessed which instance.
- What actions were taken (e.g., commands run, automation triggered).
- Any errors or failures encountered.
This helps maintain accountability, detect security incidents, and comply with regulations.
Compliance Automation and Monitoring with Systems Manager
You can automate compliance checks using SSM Automation:
- Patch Manager ensures that instances are up to date with the latest patches.
- State Manager enforces configurations across instances to meet compliance standards.
Integration with AWS Config helps monitor the compliance state of your instances over time, alerting you when non-compliant changes are made.
12. Advanced Use Cases and Integration
Managing Hybrid Environments with SSM (AWS and On-Premises)
Systems Manager is not limited to just cloud environments. You can extend its capabilities to your on-premises servers as well, providing a unified management experience for both cloud and hybrid infrastructure.
With Hybrid Activations, you can register your on-premises systems with Systems Manager and manage them alongside your EC2 instances.
| Hybrid Use Case | Description |
| On-Premises Servers | Manage both on-premises and EC2 instances seamlessly. |
| Patch Management | Apply patches to both cloud and hybrid instances. |
| Configuration Enforcement | Ensure consistent configurations across all instances. |
Cross-Account Management Using Systems Manager
Managing resources across multiple AWS accounts is made easier with Systems Manager. By using AWS Resource Access Manager (RAM), you can manage EC2 instances across different AWS accounts without switching between consoles.
| Cross-Account Management | Benefit |
| Centralized Management | Manage resources from different accounts in one place. |
| Secure Resource Sharing | Control access to resources securely with IAM roles and policies. |
Integrating SSM with Other AWS Services (e.g., Lambda, CloudWatch, EC2)
Systems Manager integrates with services like Lambda, CloudWatch, and EC2 to automate and streamline operations.
| Integration Service | Benefit |
| AWS Lambda | Trigger functions in response to events from SSM. |
| CloudWatch | Monitor and trigger alarms based on SSM activities. |
| EC2 | Use EC2 instances as managed instances in Systems Manager. |
Managing Large-Scale Infrastructure with SSM Automation
If you're managing a large-scale environment, SSM Automation allows you to automate tasks across thousands of instances, such as:
- Auto-scaling instances.
- Deploying applications.
- Running maintenance tasks.
This saves you time and resources, especially when dealing with large infrastructure setups.
13. Cost Management and Optimization
Understanding the Pricing Model of SSM
Amazon Systems Manager (SSM) provides a cost-effective way to manage your AWS infrastructure. However, understanding its pricing model is essential to avoid unexpected charges and optimize costs.
Key Elements of SSM Pricing:
- Free Services: Many features, such as Systems Manager Inventory, State Manager, and Parameter Store (for basic usage), are free for up to a certain number of resources.
- Pay-as-You-Go Services: Some features are billed based on usage. For example, Run Command, Session Manager, and Automation incur costs based on the number of managed instances and the number of actions performed.
| Feature | Pricing Model |
| Session Manager | Free for up to 100,000 session minutes/month. Charges apply beyond this limit. |
| Run Command | Free for up to 100,000 commands/month. Charges apply beyond this limit. |
| Automation | Charges based on the number of automation executions. |
| Parameter Store | Free tier for storing up to 10,000 parameters. Additional charges for higher usage and advanced features like SecureString. |
Make sure to check the AWS pricing page for detailed cost breakdowns and updates on new features.
Best Practices for Cost-Effective Usage
To optimize your costs with Amazon Systems Manager, consider the following best practices:
- Leverage Free Features: Take advantage of the free features like State Manager and Inventory Management as much as possible before scaling up to premium services.
- Schedule Commands and Automations: Use Maintenance Windows to schedule automation tasks, commands, and patching, ensuring they are run during off-peak hours to reduce overhead costs.
- Consolidate and Group Resources: Use Tagging and Resource Groups to manage related instances, enabling efficient cost tracking and reporting across multiple AWS accounts.
| Tip | Benefit |
| Use Free Tier Services | Maximize usage of free features like Parameter Store, State Manager, and more. |
| Schedule Tasks Efficiently | Reduce execution costs by scheduling tasks during off-peak hours. |
| Tag Resources | Track resource usage by tags to optimize cost allocation. |
Monitoring and Reducing Costs with SSM
Monitoring and controlling your SSM-related costs can be done through AWS tools like AWS Cost Explorer and AWS Budgets. These tools help you track usage patterns and set alerts when your costs exceed predefined limits.
Cost Tracking Tools:
- AWS Cost Explorer: Analyze usage patterns and identify areas where you can reduce costs.
- AWS Budgets: Set cost and usage budgets for your SSM resources and receive alerts when thresholds are exceeded.
Example Cost Reduction Strategy:
- Use AWS Lambda with SSM Automation to automate tasks, such as turning off unused EC2 instances, reducing costs during non-peak periods.
| Tool | Purpose |
| Cost Explorer | Identify usage trends and potential cost-saving areas. |
| AWS Budgets | Set budget thresholds and receive alerts when costs exceed limits. |
14. Best Practices for Using Amazon Systems Manager
Optimizing Performance and Efficiency with SSM
To get the most out of Amazon Systems Manager, follow these performance-optimization practices:
- Consolidate Automation Tasks: Create runbooks that include multiple steps to reduce redundant tasks and improve operational efficiency.
- Use Managed Instances: Ensure that your EC2 instances and on-premises servers are properly tagged and configured as managed instances in SSM. This ensures that SSM can monitor and apply changes uniformly across your infrastructure.
- Optimize Parameter Store Usage: Store configuration values and secrets in Parameter Store instead of hard-coding them into application code, reducing errors and simplifying management.
| Best Practice | Benefit |
| Consolidate Automation Tasks | Reduce redundant actions and optimize workflows. |
| Tag and Manage Instances | Simplify the management of large infrastructures. |
| Store Secrets in Parameter Store | Centralize and secure configuration management. |
Common Pitfalls and How to Avoid Them
While Amazon Systems Manager is powerful, there are some common pitfalls you should avoid:
- Improper IAM Permissions: Ensure that the correct IAM roles and policies are in place to prevent unauthorized access to your instances and sensitive data.
- Unmanaged Instances: Don't forget to register on-premises servers or new EC2 instances with SSM as managed instances, as this will limit your ability to automate and manage them properly.
- Ignoring Security Configurations: Always encrypt sensitive data using KMS and ensure SSM Agents are properly installed and updated to avoid security risks.
| Pitfall | Solution |
| Insufficient IAM Permissions | Implement fine-grained IAM policies to control access. |
| Unmanaged Instances | Register all instances, including on-premises servers, as managed instances. |
| Ignoring Security Best Practices | Use KMS for encryption and update SSM Agent regularly. |
SSM Troubleshooting and Debugging Techniques
When using SSM, problems may arise from time to time. Here are some troubleshooting techniques to resolve common issues:
- Check CloudWatch Logs: For issues with automation or commands, use CloudWatch Logs to capture logs and debug errors.
- Verify Instance Connectivity: Ensure that your EC2 instances have the correct IAM roles and permissions to communicate with the Systems Manager API.
- Use Run Command Logs: When troubleshooting Run Command failures, refer to the logs for detailed error messages.
Troubleshooting Steps:
- Examine logs in CloudWatch or SSM to pinpoint errors.
- Check IAM role permissions to ensure your instances are correctly configured for SSM usage.
- Verify SSM Agent status on the affected instance.
15. Conclusion
Amazon Systems Manager is a versatile and powerful tool that can streamline infrastructure management in AWS. From simplifying patch management and automation to providing secure remote access, SSM enhances operational efficiency and security. By following best practices for cost optimization, performance, and security, you can ensure that your AWS environment remains efficient, cost-effective, and well-managed.
Key Takeaways:
- SSM is essential for automating and securing infrastructure.
- Understanding SSM's pricing model helps in controlling costs.
- Best practices for performance and security are critical to effective usage.
- Future developments in SSM will continue to improve management and automation capabilities.
As AWS Systems Manager evolves, keeping up with new features will help you maintain a cutting-edge approach to infrastructure management.