In modern cloud architectures, Network Address Translation (NAT) Gateways play an essential role by enabling instances in a private subnet to access the internet or other AWS services while preventing external systems from initiating a connection to those instances. As companies move to the cloud and adopt services like AWS, Azure, and Google Cloud Platform (GCP), they encounter the challenge of maintaining security while enabling seamless outbound connectivity for certain private subnets.
The concept of NAT isn't new, but the flexibility and scalability offered by NAT Gateways in the cloud are noteworthy. This blog explores NAT Gateways in detail, from their role in networking to practical use cases, performance tips, and cost considerations.
Understanding the Basics of NAT
Source: AWS Community
Before delving into how NAT Gateways work, it's important to grasp the basics of Network Address Translation (NAT). NAT is a technique that modifies the IP address information in IP packet headers while they are in transit, usually to hide private network addresses from public view.
- Types of NAT
- Source NAT (SNAT): Rewrites the source address of the outgoing traffic. This is what a NAT Gateway performs—when instances send outbound requests, the source address is replaced with the NAT Gateway's address.
- Destination NAT (DNAT): Rewrites the destination IP address in incoming traffic. This is typically used in load balancing or routing traffic to different internal servers.
- Key Concepts
- Private Subnet: Instances in a private subnet cannot initiate outbound communication to the internet without a NAT Gateway.
- Public Subnet: Instances in a public subnet can send and receive traffic directly from the internet.
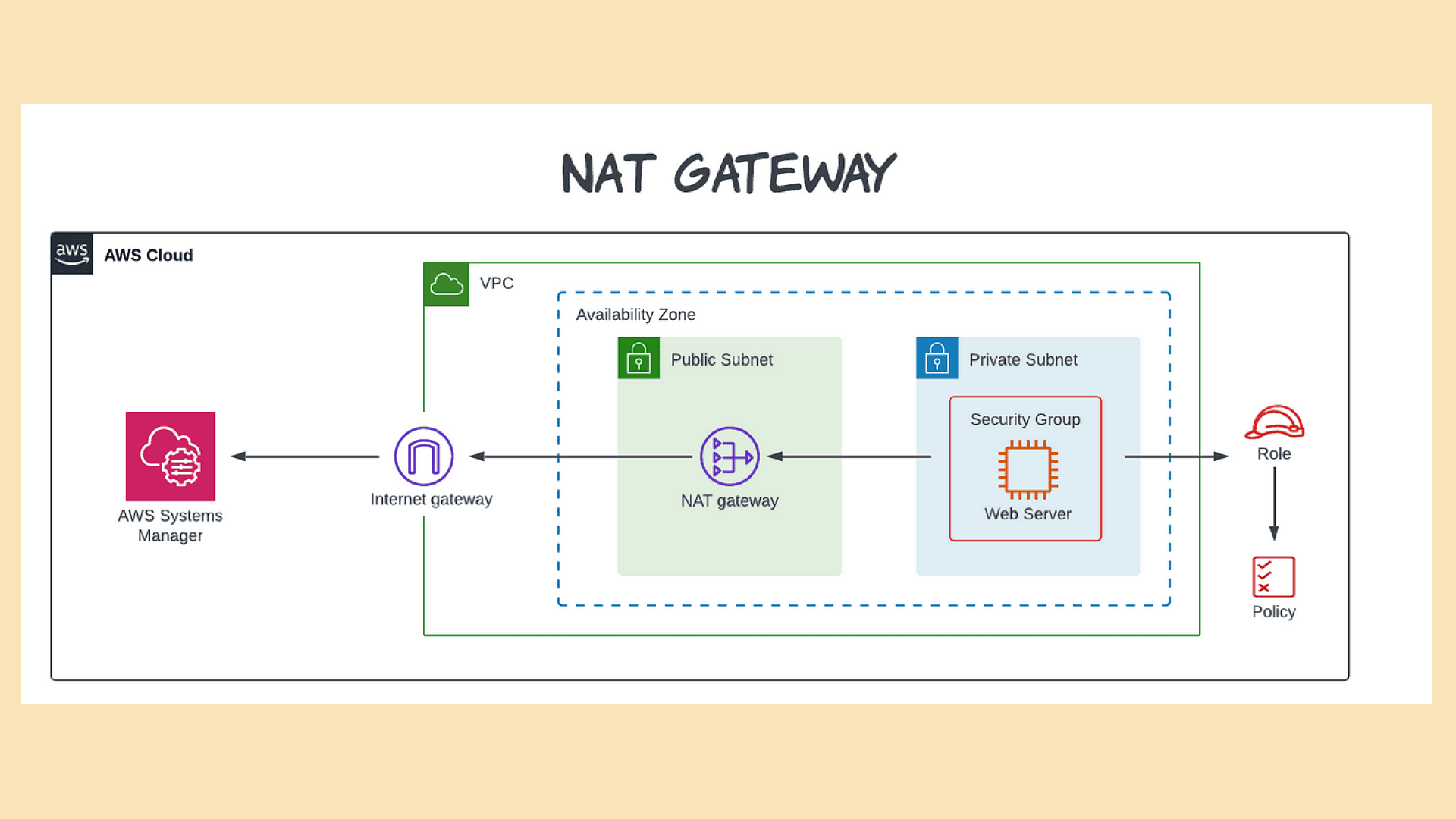
How NAT Gateway Enables Internet Access for Private Subnet Resources
Source: AWS Documentation
A NAT Gateway allows resources in a private subnet, which lack public IP addresses, to interact with the internet for outbound traffic. When an instance in the private subnet needs to access the internet (for updates or external APIs), it sends its request to the NAT Gateway. The NAT Gateway then rewrites the source IP address to its own public IP, forwards the request to the internet, and, upon receiving the response, translates it back to the private IP before sending it to the instance. This process enables secure communication without exposing the private resources’ identities.
NAT Gateway vs. NAT Instance
A common question is whether to use a NAT Gateway or a NAT Instance. While both serve the same fundamental purpose, they differ in terms of scalability, management overhead, and performance.
| Feature | NAT Gateway | NAT Instance |
| Scalability | Automatically scales with network traffic | Requires manual scaling |
| Availability | Highly available by default | Depends on the instance type |
| Management | Fully managed service | Requires patching and management |
| Performance | High throughput (up to 45 Gbps) | Limited by instance type |
| Cost | Higher hourly charge + data processing fees | Cheaper but more labor-intensive |
Choosing the Right Option
- NAT Gateway is generally preferred for high availability, scalability, and performance. It’s a fully managed service that automatically handles failover and can support large amounts of traffic without the need for manual intervention.
- NAT Instance is more flexible and can be configured to perform additional functions like traffic filtering or logging, but requires more maintenance and manual scaling.
How NAT Gateways Work in AWS, Azure, and GCP
Each cloud provider—AWS, Azure, and Google Cloud Platform (GCP)—offers NAT services, though their implementations and features may vary slightly.
AWS NAT Gateway
In AWS, a NAT Gateway is a managed service within a Virtual Private Cloud (VPC). It allows instances in private subnets to connect to the internet while keeping them shielded from unsolicited inbound traffic.
- Setup: Create a NAT Gateway in a public subnet and configure the route table of the private subnet to send internet-bound traffic to the NAT Gateway.
- Availability: It is automatically replicated within an availability zone for failover, but cross-AZ redundancy requires multiple NAT Gateways.
Azure NAT Gateway
Azure provides its NAT Gateway as a fully managed service, enabling outbound internet access for virtual machines in a Virtual Network (VNet).
- Setup: You create a NAT Gateway resource and associate it with a subnet. All outbound traffic from that subnet is routed through the NAT Gateway.
- Pricing: Azure NAT Gateways charge for both data processing and resource hours, though they are typically more cost-effective than traditional load balancer setups.
GCP Cloud NAT
Google’s Cloud NAT is unique in that it is serverless and distributed, meaning that traffic can be routed through multiple regions or zones without requiring multiple gateways.
- Setup: GCP Cloud NAT is configured at the regional level and works seamlessly with Google Compute Engine instances within VPCs.
- Scalability: GCP’s Cloud NAT automatically scales with network traffic, ensuring minimal management overhead.
Configuring a NAT Gateway in AWS
Let’s walk through the configuration of a NAT Gateway in AWS.
Step-by-Step Guide to Setup
- Create a VPC: Go to the AWS Management Console, and create a new VPC with at least two subnets: one public and one private.
- Create a NAT Gateway: In the VPC dashboard, select “Create NAT Gateway.” You’ll need to choose an elastic IP and assign it to the NAT Gateway.
- Modify Route Table: Edit the route table for your private subnet. Set the default route (0.0.0.0/0) to point to the newly created NAT Gateway.
- Test Connectivity: Launch an instance in the private subnet and attempt to connect to the internet. It should now route traffic through the NAT Gateway.
How to Set Up a NAT Gateway
Setting Up NAT Gateway in AWS
For AWS, you can create a NAT Gateway using the AWS CLI. Here's how to do it step-by-step:
AWS CLI Command to Create a NAT Gateway
# Create a NAT Gateway aws ec2 create-nat-gateway \ --subnet-id subnet-01xxx789abxxxf \ --allocation-id eipalloc-01xxx6789axxxef \ --tag-specifications 'ResourceType=natgateway,Tags=[{Key=Name,Value=MyNATGateway}]'
|
In this command:
- subnet-id: ID of the subnet where the NAT Gateway is created.
- allocation-id: ID of the Elastic IP to associate with the NAT Gateway.
Update Route Table to Use NAT Gateway
# Add a route to the route table to use the NAT Gateway for outbound internet traffic aws ec2 create-route \ --route-table-id rtb-01xxx789axxxef \ --destination-cidr-block 0.0.0.0/0 \ --nat-gateway-id nat-012xxx789axxdef
|
This command routes all outbound internet traffic (0.0.0.0/0) from the private subnet to the NAT Gateway.
Setting Up NAT Gateway in Azure
Azure allows you to create a NAT Gateway using the Azure CLI:
Azure CLI Command to Create a NAT Gateway
| bash # Create a public IP address for the NAT Gateway az network public-ip create \ --resource-group myResourceGroup \ --name myNATGatewayIP \ --sku Standard # Create a NAT Gateway az network nat gateway create \ --resource-group myResourceGroup \ --name myNATGateway \ --public-ip-addresses myNATGatewayIP \ --idle-timeout 10 # Associate the NAT Gateway with a subnet az network vnet subnet update \ --resource-group myResourceGroup \ --vnet-name myVnet \ --name mySubnet \ --nat-gateway myNATGateway |
This Azure CLI command:
- Creates a NAT Gateway with a public IP.
- Associates the NAT Gateway with a subnet in a virtual network.
Setting Up NAT Gateway in GCP (Cloud NAT)
For Google Cloud Platform, you can create a Cloud NAT using the gcloud CLI tool:
GCP CLI Command to Create a Cloud NAT
| bash # Create a Cloud NAT router gcloud compute routers create my-nat-router \ --network my-vpc \ --region us-central1 # Create a Cloud NAT configuration gcloud compute routers nats create my-cloud-nat \ --router=my-nat-router \ --region=us-central1 \ --nat-external-ip-pool=nat-external-ip \ --nat-primary-subnet-ranges=ALL_SUBNETS_ALL_IP_RANGES \ --enable-logging |
This command creates a Cloud NAT associated with a router in the specified VPC and region, enabling outbound traffic for all private subnets.
Performance Optimization and Best Practices
Performance tuning is crucial for ensuring that your NAT Gateway can handle traffic efficiently without becoming a bottleneck.
Scaling and Load Balancing
- Auto-Scaling: AWS NAT Gateways automatically scale with traffic, but for large environments, ensure you have multiple NAT Gateways across different availability zones to handle failover.
- Route Table Configuration: Use separate NAT Gateways for critical workloads to avoid single points of failure.
Managing Throughput
AWS NAT Gateways support up to 45 Gbps of traffic. For high-throughput workloads, monitor traffic patterns and ensure your network architecture is designed to distribute load effectively.
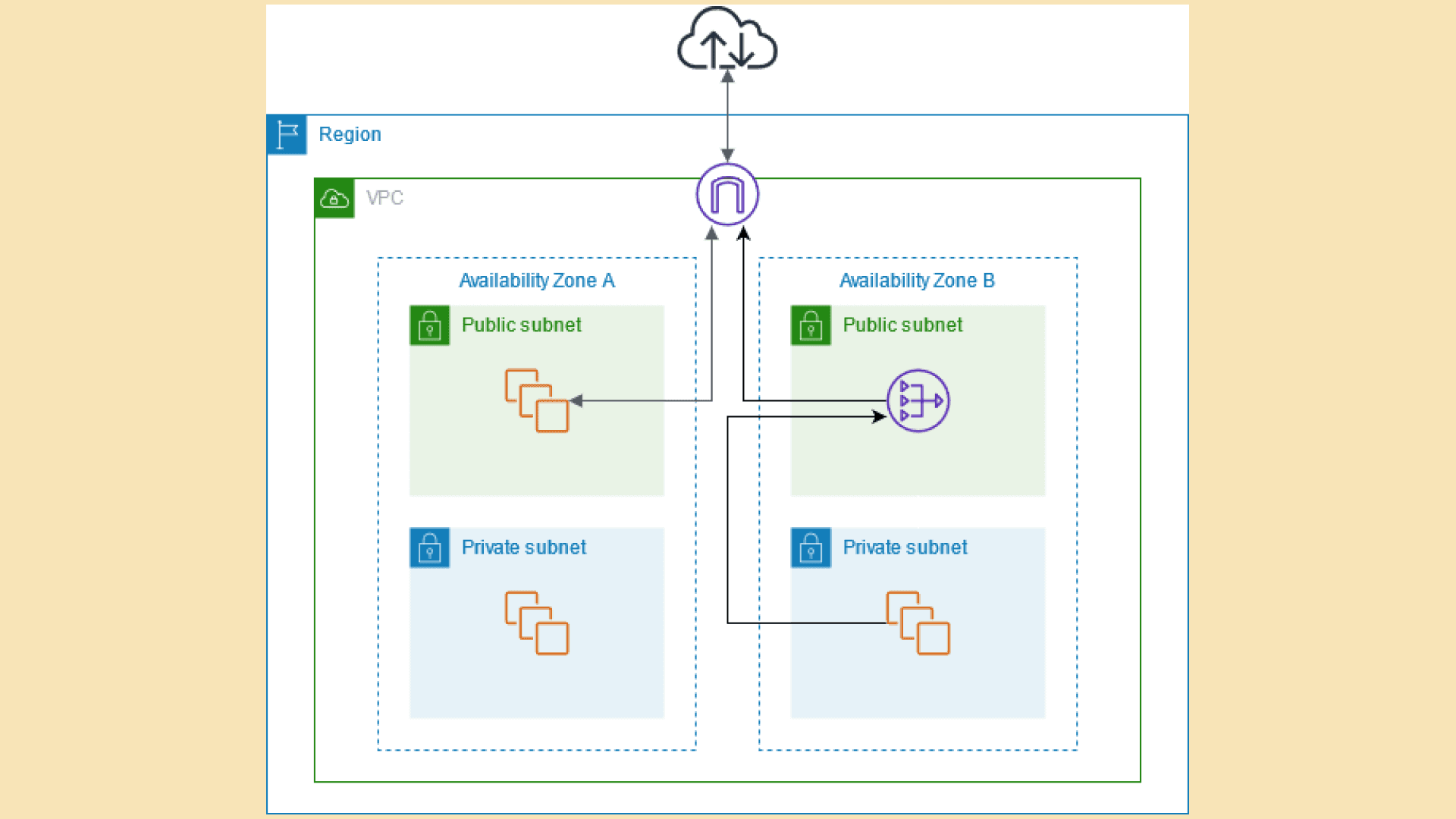
High Availability
To ensure high availability, deploy NAT Gateways in multiple availability zones (AZs). AWS does not automatically handle cross-AZ failover, so this step is crucial for resilience.
Cost Considerations and Optimization
While NAT Gateways provide critical network services for private subnets, they can introduce significant costs if not optimized properly. Understanding the pricing models and implementing cost-saving strategies is essential for managing expenses in cloud deployments.
Understanding NAT Gateway Pricing Across Providers
Different cloud providers offer distinct pricing models for their NAT services, and knowing these differences helps with budgeting and optimizing costs.
AWS NAT Gateway Pricing
In AWS, NAT Gateway costs consist of two primary components:
- Hourly Charges: This is a flat fee that you pay for every hour the NAT Gateway is provisioned.
- Data Processing Charges: This charge applies to every gigabyte of data processed through the NAT Gateway.
| Region | Hourly Charge(USD) | Data Processing(per GB) |
| US East (N. Virginia) | $0.05 | $0.05 |
| Asia Pacific (Singapore) | $0.06 | $0.05 |
Azure NAT Gateway Pricing
Azure charges for NAT Gateways similarly, but the exact pricing varies slightly based on region and the amount of data processed.
| Region | Hourly Charge (USD) | Data Processing (per GB |
| Central US | $0.05 | $0.05 |
| West Europe | $0.05 | $0.05 |
| Australia East | $0.06 | $0.05 |
GCP Cloud NAT Pricing
Google Cloud Platform’s Cloud NAT charges are typically based on regional usage. GCP does not charge for the service itself, but only for data processed by Cloud NAT.
| Region | Data Processing(per GB) |
| US Central | $0.05 |
| Europe West | $0.05 |
| Asia East | $0.05 |
Cost Optimization Techniques
Managing NAT Gateway costs involves strategic decisions about architecture and usage. Here are some effective strategies:
Minimize Unnecessary Data Transfer
Data processing fees are one of the most significant cost factors in NAT Gateways. Ensure that only necessary traffic is routed through the NAT Gateway by evaluating whether certain services or instances truly need outbound internet access.
Use Instance Metadata Locally
If instances in private subnets need to communicate with AWS services, such as S3 or EC2, consider using VPC endpoints or instance metadata for these services, rather than routing traffic through a NAT Gateway.
Cross-Availability Zone Traffic Management
NAT Gateways charge for cross-availability zone traffic. To avoid extra charges, configure your NAT Gateway in the same availability zone as your resources whenever possible.
Security Best Practices for NAT Gateways
Security is one of the most important aspects of network design in any cloud architecture. While NAT Gateways add a layer of protection by preventing unnecessary inbound traffic, further precautions should be taken to ensure a secure environment.
Restricting Outbound Traffic
A key security practice when using a NAT Gateway is to restrict outbound traffic to only what is necessary. This can be accomplished through:
- Network Access Control Lists (NACLs): NACLs can be applied at the subnet level to control both inbound and outbound traffic. This is particularly useful for preventing instances from accessing unnecessary or malicious external services.
| bash # Create a network ACL and associate it with the subnet aws ec2 create-network-acl --vpc-id vpc-01xxxx789abxxxxf # Add inbound rules to restrict traffic aws ec2 create-network-acl-entry \ --network-acl-id acl-01xxxx789abxxxf \ --ingress \ --rule-number 100 \ --protocol tcp \ --port-range From=80,To=80 \ --cidr-block 0.0.0.0/0 \ --rule-action allow |
This example creates a Network Access Control List (NACL) and restricts inbound traffic to allow only HTTP requests.
- Security Groups: While NAT Gateways themselves don't use security groups, instances within private subnets should be associated with security groups that define strict egress (outbound) rules.
| bash Copy code # Create security group and define egress rules aws ec2 create-security-group --group-name MyPrivateSG --description "My security group for NAT instances" # Allow outbound HTTPS traffic (port 443) only aws ec2 authorize-security-group-egress \ --group-id sg-01xxxxx789abxxxf \ --protocol tcp \ --port 443 \ --cidr 0.0.0.0/0 |
Use VPC Flow Logs
VPC Flow Logs allow you to monitor and capture detailed traffic flow information, which can be invaluable for security monitoring. With flow logs enabled, you can detect unusual traffic patterns and potential security threats, such as data exfiltration attempts.
Enforce TLS/SSL for Outbound Connections
When instances communicate with external services over the internet via a NAT Gateway, ensure that all communications are encrypted using TLS/SSL. This prevents sensitive data from being exposed or intercepted during transit.
Monitoring and Troubleshooting NAT Gateway
For any production cloud environment, proactive monitoring and troubleshooting are critical to ensuring smooth operations. NAT Gateways are no exception, and setting up the right tools to monitor their performance is key to avoiding network bottlenecks and minimizing downtime.
Key Metrics to Monitor
Cloud providers offer built-in monitoring tools that provide detailed metrics related to NAT Gateway usage. Some important metrics to monitor include:
- Active Connections: The number of active TCP/UDP connections being routed through the NAT Gateway. A sudden spike in active connections might indicate an unexpected surge in traffic or a potential security issue.
- Data Processed: Monitoring the volume of data processed can help you keep an eye on your costs and ensure that traffic flows align with expected patterns.
- Packet Errors and Latency: High error rates or increased latency can signal network congestion or misconfigurations.
Monitoring Tools by Provider
AWS CloudWatch: AWS provides CloudWatch metrics for NAT Gateway, including throughput, connection attempts, and packet errors. You can set up CloudWatch Alarms to notify you when thresholds are breached.
You can monitor NAT Gateway metrics via CloudWatch using the AWS CLI:
# Create a CloudWatch Alarm for high data processing on NAT Gateway aws cloudwatch put-metric-alarm \ --alarm-name HighNATGatewayDataProcessed \ --metric-name BytesProcessed \ --namespace AWS/NATGateway \ --statistic Sum \ --period 300 \ --threshold 1000000000 \ --comparison-operator GreaterThanThreshold \ --evaluation-periods 1 \ --dimensions Name=NatGatewayId,Value=nat-0123456789abcdef \ --alarm-actions arn:aws:sns:us-east-1:123456789012:MySNSTopic |
This will trigger an alarm if more than 1 GB of data is processed in a 5-minute period by the NAT Gateway.
Azure Monitor: For Azure NAT Gateways, Azure Monitor gives visibility into the health of your NAT Gateway, including connection success rates and data throughput.
For Azure, you can use Azure Monitor to monitor NAT Gateway metrics. Here’s how to query log data:
| bash # Query NAT Gateway connection metrics from Azure Monitor Logs az monitor metrics list \ --resource myNATGateway \ --resource-type "Microsoft.Network/natGateways" \ --metric-names InboundConnections,OutboundConnections,PacketsDropped \ --interval 5m |
GCP Stackdriver: GCP’s Cloud NAT integrates with Stackdriver, allowing you to collect, visualize, and alert on key metrics such as traffic flows, errors, and data processing.
In GCP, you can retrieve logs for Cloud NAT using Stackdriver:
| bash # Query NAT logs for error troubleshooting gcloud logging read "resource.type=nat_gateway AND logName=projects/my-project/logs/nat-errors |
Troubleshooting Common Issues
- No Internet Access from Private Subnet
- Ensure that the route table of the private subnet has a rule directing traffic to the NAT Gateway.
- Verify that the NAT Gateway is properly associated with an Elastic IP.
- Excessive Latency
- Check for cross-AZ traffic. If resources and the NAT Gateway are in different availability zones, traffic latency can increase. Consider using multiple NAT Gateways across different availability zones to reduce this latency.
- High Data Processing Costs
- Review your data usage patterns and ensure that you aren’t routing unnecessary traffic through the NAT Gateway. For some internal services, VPC endpoints might be a more cost-effective solution.
Best Practices for Using NAT Gateways
Implementing best practices not only helps with cost and performance but also ensures that your NAT Gateway deployments are secure and scalable.
- High Availability and Redundancy
For mission-critical workloads, deploy NAT Gateways across multiple availability zones (AZs). In AWS, this involves provisioning multiple NAT Gateways and configuring the route tables of your subnets to direct traffic to the appropriate NAT Gateway based on the subnet’s availability zone.
- Optimize Route Tables
When designing your VPC, optimize your route tables to minimize the amount of traffic flowing through the NAT Gateway. For example, route traffic to specific services through VPC endpoints rather than the NAT Gateway, which will reduce both cost and potential network congestion.
- Monitor Costs and Performance Regularly
Cloud environments are dynamic, and usage patterns can change frequently. Set up regular reviews of your NAT Gateway’s performance and costs to ensure that your architecture remains optimized.
NAT Gateway Alternatives
While NAT Gateways offer an effective solution for providing outbound internet access to private subnets, there are several alternatives that may be more suitable depending on your specific use case.
- NAT Instance
A NAT Instance is a virtual machine that can be configured to perform the same function as a NAT Gateway. While it offers more control and customization options, it requires manual scaling, maintenance, and patching. This makes it a better choice for smaller environments or highly specialized network setups.
- Transit Gateway
In complex, multi-VPC environments, a Transit Gateway can simplify routing and provide additional functionality, such as inter-VPC communication. While not a direct replacement for a NAT Gateway, it can serve as part of a broader solution for managing network traffic between VPCs and external networks.
- Direct Connect / ExpressRoute
For organizations with stringent performance or security requirements, dedicated network connections like AWS Direct Connect or Azure ExpressRoute can provide private connections to external services without routing traffic over the public internet.
The Future of NAT in Cloud Networking
As cloud adoption grows, the role of NAT Gateways and similar services will continue to evolve. Trends in hybrid cloud and multi-cloud strategies are driving new network architectures that require more flexibility, scalability, and automation.
One key development is the growing use of serverless networking solutions, such as GCP’s Cloud NAT, which eliminate the need for managing dedicated network appliances and allow traffic routing to be handled automatically at scale.
Additionally, advances in AI-driven network management may soon offer automated traffic optimization, reducing the need for manual configuration and allowing for more intelligent, adaptive network topologies.
Conclusion
NAT Gateways are a crucial component of modern cloud architectures, enabling secure and scalable outbound internet access for instances in private subnets. By understanding the different types of NAT, configuring your setup properly, and following best practices for optimization and security, you can ensure that your cloud network remains both performant and cost-efficient.
Whether you're working with AWS, Azure, or GCP, leveraging the right tools for monitoring, troubleshooting, and cost management will keep your NAT Gateway deployments running smoothly, allowing you to focus on delivering value through your applications.