As businesses expand their operations across multiple locations and adopt remote work, the need for secure and reliable network connections has never been greater. Every day, companies transfer vast amounts of sensitive data—customer information, financial records, and proprietary research—across distributed teams and cloud environments.
Without a secure communication framework, data can be exposed to cyber threats, unauthorized access, and compliance risks. Traditional networking solutions struggle to keep up with the demands of modern business, where seamless, always-on connectivity is essential. To address these challenges, businesses turn to Virtual Private Networks (VPNs). A VPN ensures that data remains secure while traveling across untrusted networks, providing the safe and constant connectivity needed in today’s digital landscape.
What is a VPN?
VPN is a private, encrypted tunnel that connects different networks or devices over the internet. It allows users to send and receive data as if they were on the same private network, even when working remotely or across multiple office locations.
For businesses, a VPN provides three key benefits:
- Secure Remote Access – Employees working from home or on the go can safely connect to company systems.
- Seamless Network Connectivity – Multiple offices or data centers can function as a unified network.
- Data Protection – Encryption prevents unauthorized access, keeping business communications private.
While VPNs have long been used to protect corporate networks, the rise of cloud computing has introduced new challenges. Companies now rely on cloud-based applications and services, making it essential to extend their networks beyond physical office locations.
Understanding the Basics
Before diving into Azure VPN specifics, let's understand some fundamental concepts:
What happens without a VPN?
Nowadays, remote work and cloud-based operations are more common than ever. However, when employees connect to company resources from home or public networks without a VPN:
- Their data travels across the public internet unprotected
- Sensitive information could potentially be intercepted
- Your network perimeter is expanded to include countless unsecured connection points
These challenges make it crucial to have a secure way to connect remote users and office networks to business resources. This is where Azure VPN comes in.
What is Azure VPN?
Azure VPN is a cloud-based service offered by Microsoft Azure that enables organizations to securely connect their on-premises networks with Azure's cloud infrastructure. Azure VPN offers multiple connection types to suit different business needs, ranging from site-to-site connections, which link entire office networks, to point-to-site connections for individual remote workers.
With Azure VPN, organizations benefit from:
- Scalability: Easily adjust to growing business needs by connecting multiple locations without requiring additional physical infrastructure.
- Security: By using strong encryption, Azure VPN protects sensitive business data as it travels between on-premises networks and the cloud.
- Reliability: Azure VPN is backed by Azure’s robust infrastructure, ensuring consistent performance and availability.
In short, Azure VPN is more than just a VPN service; it’s a key enabler for modern cloud-based businesses, providing both secure connectivity and seamless integration with the broader Azure ecosystem.
How does Azure VPN Enhances On-Premises and Cloud Network Connectivity?
Azure VPN enables businesses to seamlessly link their on-premises infrastructure to Microsoft Azure, creating a secure communication pathway between their internal networks and cloud services. This is especially important for businesses looking to transition to the cloud while maintaining their existing systems, or for those managing a hybrid infrastructure.
With Azure VPN, companies can safely transmit data between their on-premises networks and Azure, ensuring secure remote access for employees and consistent, high-performance networking across locations. Whether it’s connecting multiple office locations or providing remote teams with secure access to cloud resources, Azure VPN helps businesses maintain a unified, protected network environment.
This is especially valuable for businesses that:
- Are transitioning from on-premises data centers to cloud-based workloads.
- Need a secure and scalable solution to connect multiple locations.
- Want to enable remote employees and third-party vendors to access corporate systems securely.
Unlike traditional VPNs, which primarily focus on securing connections between individual users and corporate networks, Azure VPN supports site-to-site connections, remote access, and even dedicated private links through Microsoft’s ExpressRoute.
Key Components and Their Roles
To establish a secure and efficient network connection, Azure VPN relies on several essential components:
Virtual Network Gateway
The Virtual Network Gateway acts as the entry point for VPN connections within Azure. It functions as a bridge between on-premises networks and Azure Virtual Networks (VNets), directing traffic securely between the two. This gateway ensures that data moves safely across different environments, while allowing businesses to scale their infrastructure. In addition, businesses can deploy multiple gateways to increase network resilience and optimize performance by ensuring continuous connectivity, even if one gateway goes down.
VPN Gateway
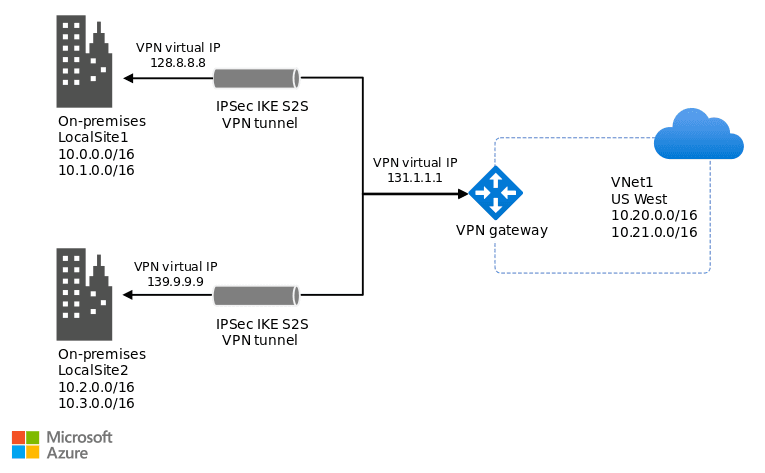
Source - Azure
The VPN Gateway is responsible for managing encrypted VPN tunnels between Azure and external networks (such as on-premises locations or remote user devices). It supports several connection types:
- Site-to-Site (S2S): This type of connection links entire corporate networks, facilitating secure communication between an on-premises network and Azure.
- Point-to-Site (P2S): For individual remote workers who need to securely access Azure resources, this connection allows them to create a VPN tunnel from their devices to Azure.
Additionally, the VPN Gateway supports ExpressRoute, which creates a dedicated private connection between on-premises networks and Azure, bypassing the public internet to improve security and performance.
Local Network Gateway
The Local Network Gateway represents the on-premises network in Azure’s configurations. This component contains crucial information such as IP address ranges, VPN device settings, and routing configurations. It essentially provides Azure with the details needed to know how to connect securely to the on-premises network, facilitating smooth communication between on-premises environments and cloud-based resources.
With businesses increasingly relying on cloud-based applications, Azure VPN offers a secure, scalable, and cost-effective way to integrate networks. By encrypting data transmissions, it minimizes the risk of cyber threats, ensuring sensitive information remains protected.
Additionally, Azure VPN is built for flexibility. Companies can start small, connecting a single office to Azure, and later expand to multiple sites or even a fully cloud-based model. It also integrates seamlessly with other Azure security and networking tools, making it a powerful component of a larger cloud strategy.
Azure VPN Architecture
The architecture of Azure VPN is designed to establish secure, scalable, and resilient connectivity between on-premises networks, remote users, and Azure resources. By leveraging multiple VPN connection types, enterprises can create hybrid network infrastructures that ensure reliable and encrypted data flow.
Network Design and Topology
Azure VPN can be deployed in several architectural models, depending on an organization's network requirements. The most common architectures include:
Hub-and-Spoke Architecture
In this model, a central Virtual Network (VNet) acts as a hub, connecting multiple on-premises networks and branch offices via Site-to-Site (S2S) VPNs. Spoke VNets can then connect to the hub for communication between different departments, workloads, or cloud services. This design:
- Provides a centralized security and routing control.
- Reduces the number of required VPN tunnels.
- Optimizes performance by minimizing unnecessary network hops.
Full Mesh Architecture
A full mesh VPN topology enables direct communication between multiple sites without routing traffic through a central hub. This approach is best for organizations needing:
- Low-latency connections between geographically distributed offices.
- High availability without reliance on a central hub.
- Faster communication for real-time applications, such as VoIP or video conferencing.
Hybrid Cloud Architecture
This model integrates on-premises networks with Azure VNets using Azure VPN alongside ExpressRoute. Organizations can:
- Establish a primary VPN-based connection with a backup ExpressRoute for redundancy.
- Securely extend their data center resources to the cloud.
- Optimize workloads between cloud and on-premises environments.
Traffic Routing and Security Considerations
The Azure VPN architecture is designed with multiple layers of security and traffic control to ensure secure communication. Key elements include:
- BGP (Border Gateway Protocol):
- Used for dynamic routing to avoid manual route configuration.
- Supports automatic failover for high availability in multi-site VPN setups.
- Ensures optimal routing paths for cloud and on-premises traffic.
- Encryption Standards:
- Uses IPsec/IKE (Internet Key Exchange) for encrypted VPN tunnels.
- Supports AES-256 encryption for maximum security.
- Ensures secure transmission of sensitive data across public networks.
- Redundancy & Failover:
- Azure VPN supports Active-Active mode for dual VPN tunnels, ensuring zero downtime in case of a single gateway failure.
- ExpressRoute fallback to VPN provides an automatic switchover if a dedicated ExpressRoute connection experiences issues.
Integration with Enterprise Security and Networking
Azure VPN works alongside Azure Firewall, Network Security Groups (NSGs), and Azure DDoS Protection to enhance security and compliance. Key integration aspects include:
- Traffic Filtering and Firewall Rules:
- Enforce security policies for incoming and outgoing traffic.
- Define network rules based on IP addresses, protocols, and ports.
- Identity and Access Management (IAM):
- Enforce conditional access for remote users using Azure Active Directory (Azure AD).
- Apply multi-factor authentication (MFA) to VPN logins.
- Monitoring and Diagnostics:
Azure Network Watcher provides VPN health monitoring, performance insights, and troubleshooting tools.- Log Analytics enables real-time monitoring of VPN connections, traffic logs, and potential security risks.
Types of VPN Connections
Azure VPN offers multiple connection types to accommodate different business requirements, whether for individual remote access, corporate network extensions, or high-performance private connections. Each type serves a distinct purpose in ensuring secure and scalable connectivity between on-premises environments and Azure.
Point-to-Site (P2S) VPN – For Individual Remote
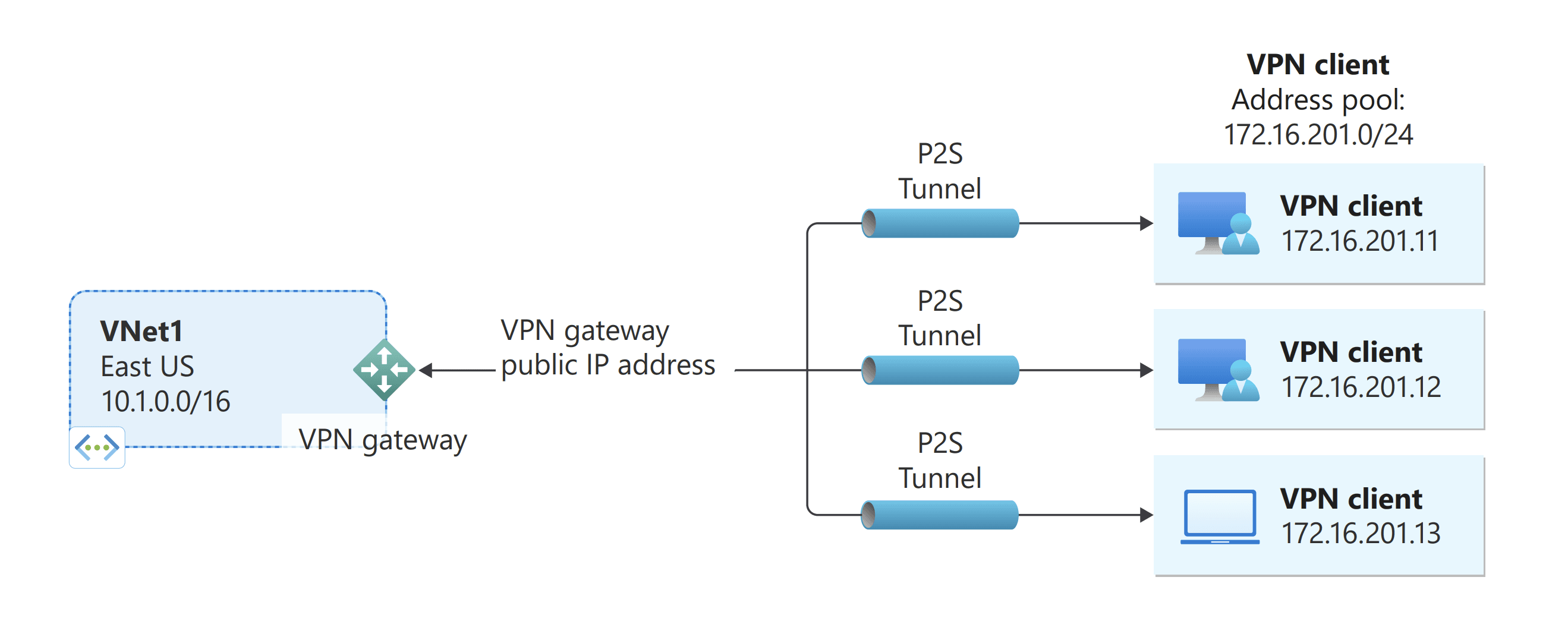
Source - Azure
A Point-to-Site (P2S) VPN is designed for individual employees who need secure access to Azure resources from remote locations. This is particularly useful for remote workers, contractors, or traveling staff who must securely connect to the corporate network without needing a full-scale network extension.
- How It Works: Employees install a VPN client on their devices, which establishes an encrypted tunnel directly to the Azure Virtual Network.
- Security Features: Uses certificate-based authentication, Azure Active Directory (Azure AD), or RADIUS authentication for secure access control.
- Best For: Organizations with remote work policies, temporary workforce needs, or freelancers accessing internal systems.
Site-to-Site (S2S) VPN – For Corporate Network Integration
A Site-to-Site (S2S) VPN extends entire on-premises networks into Azure, ensuring seamless connectivity between data centers, office locations, and cloud-based workloads.
- How It Works: A VPN device at the on-premises location establishes an IPsec/IKE-encrypted tunnel with an Azure VPN Gateway, allowing continuous network communication.
- Security & Performance: Provides a dedicated, persistent connection suitable for hybrid cloud architectures where workloads span across on-premises and Azure.
- Best For: Businesses implementing hybrid cloud models that require secure, consistent communication between cloud and on-premises resources.
ExpressRoute – For High-Performance, Private Connections
For businesses requiring high bandwidth, low latency, and enhanced security, ExpressRoute provides a dedicated private connection between on-premises data centers and Azure—bypassing the public internet entirely.
- How It Works: ExpressRoute connects on-premises infrastructure to Azure via a private link through a service provider, offering greater reliability and performance.
- Advantages Over VPN: Since traffic never traverses the public internet, ExpressRoute offers higher security, lower latency, and faster speeds than traditional VPN solutions.
- Best For: Enterprises running latency-sensitive applications, financial services, healthcare, and industries requiring compliance-driven private connectivity.
How do Azure VPN Components Work Together?
To ensure secure, reliable, and efficient connectivity, Azure VPN components work in coordination, forming an integrated system that supports multiple VPN connection types.
- Virtual Network Gateway – The Core Network Entry Point
- Acts as the central hub that enables traffic routing between Azure and external networks.
- Supports both P2S and S2S VPNs, ensuring remote users and entire corporate networks can connect securely.
- VPN Gateway – Manages Secure Encrypted Tunnels
- Establishes and maintains encrypted tunnels for data transmission across the internet.
- Supports IPsec/IKE encryption protocols to protect sensitive information from cyber threats.
- Local Network Gateway – Represents On-Premises Infrastructure
- Stores configuration details such as IP address ranges, VPN device settings, and routing information.
- Ensures correct traffic flow between on-premises networks and Azure resources.
Workflow of Azure VPN Connectivity
- For Individual Users (P2S):
- The user authenticates via a VPN client.
- The connection is encrypted and routed through the VPN Gateway to Azure resources.
- For Corporate Networks (S2S):
- The on-premises VPN device initiates a secure connection to the Azure VPN Gateway.
- Traffic between the on-premises network and Azure VNet is encrypted and dynamically routed.
- For High-Performance Needs (ExpressRoute):
- A private circuit is established between the enterprise data center and Azure, bypassing the internet for higher security and performance.
- Businesses can configure ExpressRoute with VPN failover, ensuring high availability.
Configuration Options
Configuring Azure VPN is essential for enabling secure, encrypted communication between your on-premises infrastructure and Azure cloud. The key to a successful setup lies in the planning phase, where you make decisions about the VPN’s architecture, security methods, and performance optimization.
Setting Up the Virtual Network Gateway
The Virtual Network Gateway is at the core of any Azure VPN setup, enabling secure connectivity between your on-premises network and Azure resources.
Steps to Set Up the Virtual Network Gateway:
- Create a Virtual Network (VNet):
Plan and create a VNet that will serve as the foundation for your Azure VPN. Ensure its IP address range does not overlap with your on-premises network, allowing for smooth routing of traffic. - Select the Correct VPN Gateway SKU:
Depending on your performance needs, choose a VPN Gateway SKU (e.g., Basic, VpnGw1, VpnGw2). These choices determine bandwidth, reliability, and redundancy levels, so it's important to align this with your organizational needs. - Assign a Public IP:
A static public IP is critical for establishing reliable, continuous communication between your Azure environment and the external network. This IP serves as the entry point for VPN traffic.
Why this is important:
Incorrect VNet addressing or using the wrong gateway SKU can hinder performance or prevent proper connectivity, leading to potential network instability.
Defining VPN Connection Types
Once your Virtual Network Gateway is established, the next step is to choose the VPN connection types that best suit your requirements: Point-to-Site (P2S) for individual users or Site-to-Site (S2S) for network-to-network communication.
P2S VPN: Remote Access for Users
P2S connections allow remote employees to access Azure resources securely.
- Enable P2S on the Gateway:
Activate the Point-to-Site feature on your VPN Gateway to enable remote access for users. - Choose Authentication Methods:
Azure supports various authentication options for P2S:- Azure Active Directory (Azure AD) for organizations using cloud-based user management.
- Certificate-Based Authentication for enhanced security with digital certificates.
- RADIUS Authentication for enterprises needing to integrate with existing on-premises identity services.
- Distribute VPN Client Configuration:
After configuration, download the VPN client and distribute it to users with necessary instructions for setup.
S2S VPN: Network-Level Connectivity
S2S VPNs connect entire networks (on-premises to Azure) for continuous secure communication.
- Define the Local Network Gateway:
A Local Network Gateway represents your on-premises network in Azure. Specify the public IP address and address space for routing. - Set Encryption Parameters:
Configure IPsec/IKE settings, ensuring both ends use matching encryption algorithms like AES256 and SHA256. - Routing Policies:
Choose between static routing or dynamic routing (BGP) for more scalable, adaptive routing paths.
Why this is important:
Choosing the wrong authentication method or encryption protocol can expose your network to risks. Ensure secure tunnels by carefully configuring the VPN and encryption methods.
Enhancing Security & Performance
After setting up VPN connections, the next step is to ensure security and optimize performance.
Network Security Configuration:
- Apply Network Security Groups (NSGs):
Use NSGs to restrict traffic within your VNet, ensuring that only authorized resources have access to sensitive data. - Use Conditional Access:
Implement MFA (Multi-Factor Authentication) for P2S VPNs to enforce strict access controls, ensuring that only verified users can connect remotely. - Enable Azure Firewall:
For added security, consider using Azure Firewall for more granular traffic inspection, especially when dealing with large-scale deployments.
Performance Optimization:
- Choose the Correct Gateway SKU:
Ensure the selected SKU supports the required throughput and scalability. For higher traffic needs, select advanced SKUs like VpnGw2 or VpnGw3. - Consider ExpressRoute for High-Performance Needs:
For scenarios where low latency and high throughput are critical, leverage ExpressRoute for a dedicated, private connection to Azure. - Load Balancing for High Availability:
Distribute traffic across multiple VPN Gateways to ensure high availability and prevent bottlenecks in high-demand environments.
Security Considerations for Azure VPN
Ensuring robust security is critical when configuring an Azure VPN. By integrating strong encryption methods, authentication systems, and following best practices, you can safeguard your network communication and prevent unauthorized access.
Encryption Standards and Protocols
Azure VPN provides end-to-end encryption to protect data during transit. The primary encryption standard is AES-256, which is widely recognized for its security. Azure uses IPsec/IKEv2 protocols, ensuring secure tunneling and data integrity across VPN connections.
- AES-256 Encryption: Offers strong encryption to prevent unauthorized access, ensuring that sensitive data remains confidential.
- IPsec/IKEv2 Protocols: Ensure the secure exchange of keys and provide high resilience against network attacks.
Authentication Mechanisms
Azure VPN supports several authentication mechanisms to ensure only authorized users and devices can establish a secure connection.
- Azure Active Directory (Azure AD): Ideal for organizations already using Azure AD for identity management, providing seamless integration and centralized access control.
- RADIUS Authentication: Suitable for businesses that require an on-premises authentication solution, integrating with existing infrastructure.
- Certificate-Based Authentication: Provides a high level of security by utilizing digital certificates for device identification, adding an extra layer of protection.
Best Practices for VPN Security
To further strengthen the security of your Azure VPN setup, the following best practices are recommended:
- Implement Multi-Factor Authentication (MFA): Enforce MFA for remote access through Point-to-Site (P2S) connections to ensure that even if credentials are compromised, unauthorized access is blocked.
- Role-Based Access Control (RBAC): Restrict access based on user roles to minimize exposure of critical resources. Users should only have access to what they need.
- Regularly Monitor VPN Logs: Implement a system to continuously monitor VPN logs for unusual activities or security anomalies. This allows proactive identification of potential threats before they escalate.
Performance Factors for Optimizing Azure VPN
Optimizing the performance of your Azure VPN involves understanding throughput limitations, adjusting configurations, and ensuring network redundancy. Here are key factors to consider for maintaining optimal performance while ensuring high availability.
Understanding Bandwidth Limitations
Each VPN gateway SKU has a specified maximum throughput limit. It’s essential to choose the right VPN Gateway SKU based on your traffic and connection requirements. Selecting an inadequate SKU can result in network congestion or degraded performance. The common gateway SKUs include:
- Basic SKU: Suitable for small-scale environments with low bandwidth requirements.
- VpnGw1, VpnGw2, VpnGw3: Provide varying levels of bandwidth and performance, with higher SKUs offering more bandwidth and redundancy.
By selecting the correct SKU, you ensure that your network traffic is handled efficiently without bottlenecks.
Optimizing VPN Performance
To further improve the performance of your Azure VPN, consider the following optimizations:
- Traffic Shaping and Quality of Service (QoS): Implement traffic shaping techniques to prioritize critical application traffic. Use QoS policies to ensure that the most important traffic is delivered with minimal delay.
- Optimize Routing Configurations: Ensure routing tables are optimized to direct traffic along the most efficient paths. For larger networks, consider using dynamic routing protocols like BGP to automatically adapt to network changes.
Network Redundancy and Failover
To ensure high availability and resilience, it’s vital to implement redundant network configurations that can handle failovers in case of a failure.
- Active-Passive Gateway Configuration: Deploy active-passive VPN gateway configurations to ensure that if one gateway fails, another can take over without interruption.
- Azure Traffic Manager: Use Azure Traffic Manager to manage traffic distribution across multiple VPN gateways, providing automatic failover and improving overall reliability.
Implementation Guide
Once your Azure VPN configuration is in place, the next phase is implementation, where you execute the setup and test the system for connectivity, security, and performance.
Deploying Point-to-Site (P2S) VPN for Remote Users
To allow individual users secure access to your Azure resources, you will need to implement Point-to-Site (P2S) VPNs. Here's how you can do it:
Step 1: Set Up the Virtual Network and Gateway
- Create the Virtual Network (VNet):
Ensure the VNet has the right address space and is properly connected to other Azure resources. - Deploy the VPN Gateway:
Based on your performance needs, choose the correct SKU for the gateway.
Step 2: Authentication Setup for P2S
- Choose the Right Authentication Type:
Select between Azure AD, Certificate-Based, or RADIUS authentication based on your organization’s identity management.
Step 3: Distribute VPN Client Configuration
- Provide the configuration file to remote users, ensuring they install the client on their devices and set up the connection properly.
Step 4: Validate Remote Access
- Verify Connectivity:
Use tools like ping or traceroute to ensure users can access Azure VMs or services securely.
Deploying Site-to-Site (S2S) VPN for Network Connectivity
For connecting your on-premises network to Azure, you'll use Site-to-Site (S2S) VPN. This type of connection ensures that entire on-premises networks can securely communicate with Azure resources.
Step 1: Configure the On-Premises VPN Device
- Ensure compatibility with Azure’s VPN requirements. This could include configuring firewalls or routers to handle VPN traffic securely.
- Assign a static public IP to your on-premises VPN device.
Step 2: Set Up the Azure VPN Gateway
- Create the Gateway in Azure and configure the necessary IPsec/IKE parameters.
Step 3: Set Up Routing
- Define routing policies, choosing between static or dynamic (BGP) routing based on your network setup and traffic patterns.
Step 4: Validate Connectivity
- Once everything is configured, ping and traceroute to ensure seamless communication between on-premises and Azure networks.
Troubleshooting and Monitoring
Once the VPN is deployed, continuous monitoring is necessary to ensure reliable performance and secure operations.
Monitoring Tools:
- Azure Network Watcher: Use this tool to diagnose and monitor VPN connection health.
- Log Analytics: Collect and analyze log data to troubleshoot issues in real-time.
Troubleshooting Tips:
- Check VPN Status in Azure and ensure that there are no configuration mismatches between the client and the gateway.
- Use ping, traceroute, and Azure diagnostics to track down and resolve issues related to connectivity.
Troubleshooting Azure VPN
When working with Azure VPN, it’s important to troubleshoot effectively to address common connection and configuration issues. Below is a comprehensive guide with specific error codes, resolution steps, and automated solutions using Azure CLI, PowerShell, and ARM templates.
Connection Failures
Error Code 809 - The VPN Server is Unreachable
This error typically occurs when the client cannot reach the Azure VPN Gateway due to network configuration issues or a firewall blocking the connection.
Resolution Steps:
- Check Gateway Public IP: Ensure the VPN Gateway has a public IP assigned and that it’s accessible from the client network.
- Verify Port Accessibility: Ensure that necessary VPN ports (UDP 500, UDP 4500) are open on both the client firewall and any intermediate devices.
- Firewall Configuration: Ensure your on-premises firewall rules are allowing traffic on the necessary ports (for IPsec, UDP ports 500 and 4500).
- Check Network Security Groups (NSGs): Make sure the NSGs applied to your Azure VPN Gateway are not blocking the VPN traffic.
CLI/PowerShell Commands:
Verify Gateway Public IP (CLI):
| bash az network vpn-gateway show --name <GatewayName> --resource-group <ResourceGroupName> --query "ipConfigurations[0].publicIpAddress" |
Verify Gateway Public IP (PowerShell):
| powershell Get-AzVpnGateway -Name <GatewayName> -ResourceGroupName <ResourceGroupName> | Select-Object -ExpandProperty IpConfigurations |
Error Code 812 - The Connection Was Denied Due to Policy Restrictions
This error happens when the authentication policy applied to the VPN connection is incompatible with the incoming request.
Resolution Steps:
- Check Authentication Method: Ensure that the VPN client’s authentication method (Azure AD, certificate-based, or RADIUS) matches the one configured in Azure.
- Verify RADIUS or Azure AD Configuration: If using RADIUS or Azure AD, ensure the settings are correctly configured in Azure Active Directory or your RADIUS server.
- Review Conditional Access: If using Conditional Access policies, ensure the rules do not block VPN access for the user or group.
CLI/PowerShell Commands:
Verify P2S VPN Client Package (CLI):
| bash az network vpn-client package generate --resource-group <ResourceGroupName> --vpn-gateway <GatewayName> --authentication-method <AuthMethod> |
PowerShell: Use the command below to generate a client package:
| powershell New-AzVpnClientPackage -ResourceGroupName <ResourceGroupName> -VpnGatewayName <GatewayName> -AuthenticationMethod <AuthMethod> |
Latency and Stability Issues
Error: High Latency or Packet Loss
This issue could arise from network congestion or incorrect routing configurations, causing the VPN tunnel to perform poorly.
Resolution Steps:
- Verify Routing Configuration: Check whether static routes or BGP (Border Gateway Protocol) are configured. Misconfigured static routes could lead to inefficient routing paths.
- Use Azure Network Watcher: Use the Connection Troubleshoot tool in Network Watcher to identify routing issues between the client and Azure.
- Check Gateway Performance: Review the VPN Gateway metrics using Azure Monitor. High CPU utilization or throughput limits may cause delays.
CLI/PowerShell Commands:
Check VPN Gateway Metrics (CLI):
| bash az monitor metrics list --resource <VPNGatewayResourceId> --metric "Throughput" --interval 5m |
Check VPN Gateway Metrics (PowerShell):
| powershell Get-AzMetric -ResourceId <VPNGatewayResourceId> -MetricName "Throughput" -TimeGrain 00:05:00 |
Resolution Steps for Latency/High Traffic (BGP Issues)
- Enable BGP: If not already using BGP, consider enabling it for dynamic routing. This ensures routing tables are automatically updated with the best path.
- Verify BGP Peering: Ensure that BGP peering is properly configured between the Azure VPN Gateway and your on-premises device.
- Adjust Network Bandwidth: Increase the bandwidth or upgrade to a higher VPN Gateway SKU if network throughput is low.
CLI/PowerShell Commands:
Enable BGP on VPN Gateway (CLI):
| bash az network vpn-gateway update --name <GatewayName> --resource-group <ResourceGroupName> --bgp-peer <PeerIP> --asn <ASNNumber> |
Enable BGP on VPN Gateway (PowerShell):
| powershell Set-AzVpnGateway -Name <GatewayName> -ResourceGroupName <ResourceGroupName> -BGP -PeerIP <PeerIP> -ASN <ASNNumber> |
VPN Connection Failures During Maintenance or Downtime
Resolution Steps:
- Use Traffic Manager for Failover: To ensure high availability, use Azure Traffic Manager to distribute traffic between multiple VPN gateways. This helps avoid downtime during planned maintenance or unexpected failures.
CLI/PowerShell Commands:
Create Traffic Manager Profile (CLI):
| bash az network traffic-manager profile create --name <ProfileName> --resource-group <ResourceGroupName> --routing-method Priority --unique-dns-name <DNSName> |
Create Traffic Manager Profile (PowerShell):
| powershell New-AzTrafficManagerProfile -ResourceGroupName <ResourceGroupName> -Name <ProfileName> -RoutingMethod Priority -UniqueDnsName <DNSName> |
VPN Gateway Scaling Issues
Error: Low Throughput or High Latency Due to Gateway Sizing
If your network is seeing slow VPN performance or latency issues, it might be due to the VPN Gateway SKU not being powerful enough.
Resolution Steps:
- Upgrade VPN Gateway SKU: If your traffic volume increases or you are experiencing bottlenecks, upgrading to a higher-tier VPN Gateway SKU like VpnGw2 or VpnGw3 may be necessary.
- Use Load Balancers: If you have multiple VPN Gateways, you can distribute traffic using Azure Load Balancer to ensure redundancy and high availability.
CLI/PowerShell Commands:
Upgrade VPN Gateway SKU (CLI):
| bash az network vpn-gateway update --name <GatewayName> --resource-group <ResourceGroupName> --sku VpnGw2 |
Upgrade VPN Gateway SKU (PowerShell):
| powershell Set-AzVpnGateway -Name <GatewayName> -ResourceGroupName <ResourceGroupName> -Sku VpnGw2 |
Automation Using ARM Templates for VPN Deployment
You can automate the deployment of Azure VPN Gateways using ARM templates for consistency and speed.
Example ARM Template for VPN Gateway Deployment
| json { "$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#", "contentVersion": "1.0.0.0", "resources": [ { "type": "Microsoft.Network/virtualNetworkGateways", "apiVersion": "2020-11-01", "location": "[resourceGroup().location]", "properties": { "gatewayType": "Vpn", "vpnType": "RouteBased", "enableBgp": true, "ipConfigurations": [ { "name": "vpngateway-ipconfig", "properties": { "subnet": { "id": "[resourceId('Microsoft.Network/virtualNetworks/subnets', 'myVNet', 'GatewaySubnet')]" }, "publicIpAddress": { "id": "[resourceId('Microsoft.Network/publicIPAddresses', 'myVpnPublicIP')]" } } } ], "sku": { "name": "VpnGw2", "tier": "VpnGw2" } } } ] } |
Common Applications of Azure VPN
Azure VPN is a versatile tool that supports a wide range of business needs, particularly when it comes to maintaining secure, reliable network connections across various environments. Here are some of the most common ways organizations use Azure VPN:
- Secure Remote Access for Employees
With the rise of remote work, ensuring employees can access internal systems securely has become a top priority for many organizations. Azure VPN allows businesses to provide remote workers with secure access to corporate resources, no matter where they are located. This means employees can work safely from home or on the go, without compromising sensitive data.
- Extending On-Premises Networks to the Cloud
As more businesses shift towards cloud-based infrastructures, hybrid cloud environments have become increasingly popular. Azure VPN makes it easy to integrate on-premises networks with Azure Virtual Networks (VNets), enabling businesses to extend their internal networks to the cloud. This integration ensures seamless communication between on-premises and cloud-based systems, without requiring separate networks for each environment.
- Connecting Branch Offices and Hybrid Environments
For organizations with multiple locations, Azure VPN provides a secure way to interconnect branch offices and ensure efficient communication. Whether you're linking regional offices, data centers, or remote workers, Azure VPN simplifies the process of creating a secure and unified network that spans multiple sites. This leads to better collaboration, faster data sharing, and enhanced security across locations.
- Ensuring Secure Data Transfers for Compliance
Certain industries, such as finance, healthcare, and government, operate under strict regulatory frameworks that require businesses to protect sensitive data during transmission. Azure VPN plays a crucial role in helping these industries meet compliance requirements by encrypting data transfers and ensuring that sensitive information remains secure. This helps businesses avoid costly fines and protect their reputation while adhering to industry standards.
- Reducing Dependency on Private Circuits
Traditionally, organizations would invest in expensive private circuits or leased lines to connect remote offices. However, with Azure VPN, businesses can reduce or eliminate their reliance on costly private infrastructure. Azure VPN offers a cost-effective alternative by providing secure and reliable connections over the public internet. This allows businesses to maintain high levels of security without the hefty price tag of private circuits.
Real-World Applications
Organizations across different industries rely on Azure VPN to address networking challenges such as secure remote access, multi-site connectivity, and high-availability networking. Below are three common scenarios illustrating how Azure VPN is implemented in practical business settings.
Enabling Secure Remote Work for a Small Accounting Firm
Business Type: An accounting firm with 15 employees
Objective: Secure remote access to client financial data
The Challenge
With employees frequently working from home and client locations, the firm needed a secure way to access sensitive financial records stored on office servers. The solution needed to ensure compliance with financial data regulations while remaining cost-effective and easy to manage.
The Solution
- Deployed Azure Point-to-Site (P2S) VPN to enable secure remote access for employees.
- Implemented certificate-based authentication to ensure only authorized personnel could connect.
- Used the Basic VPN Gateway SKU, which provided sufficient bandwidth for their needs while keeping costs low.
The Results
- Employees could securely access files from anywhere without compromising sensitive data.
- The VPN setup was affordable, costing less than $100 per month.
- The firm met regulatory requirements without investing in additional infrastructure.
Connecting Multiple Retail Locations to a Central Cloud System
Business Type: A regional retail chain with 12 store locations
Objective: Real-time inventory and sales data synchronization across all branches
The Challenge
The company needed a centralized network solution to connect all store locations to its inventory and point-of-sale (POS) system hosted in Azure. The previous network, relying on traditional private circuits, was costly and difficult to scale.
The Solution
- Implemented Azure Site-to-Site (S2S) VPN to connect each store to the central cloud infrastructure securely.
- Designed a hub-and-spoke network architecture, with Azure VPN acting as the primary hub.
- Selected the Azure VPN Gateway VpnGw1 SKU, providing a balance between performance and cost.
The Results
- Real-time inventory updates allowed stores to track stock levels instantly.
- Centralized network management simplified IT operations and improved scalability.
- 40% cost reduction compared to the previous MPLS-based private network solution.
Ensuring High-Availability Connectivity for a Healthcare Provider
Business Type: A large healthcare facility with multiple departments and remote clinics
Objective: Maintain continuous, secure access to patient data stored in Azure
The Challenge
The healthcare provider required high-availability network connectivity to access patient records and medical imaging files in Azure. Any downtime could delay critical medical decisions, making network reliability a top priority.
The Solution
- Implemented a hybrid networking approach combining Azure VPN and ExpressRoute for redundancy.
- Deployed Azure VPN Gateway VpnGw2 SKU to support large-scale data transfers.
- Configured automatic failover, ensuring uninterrupted connectivity even if the primary connection failed.
The Results
- 99.99% uptime, ensuring uninterrupted access to critical patient data.
- Compliance with healthcare regulations, including HIPAA and GDPR.
- Optimized network performance, enabling fast transfer of large imaging files.
Key Takeaways
- Small businesses can use Azure VPN for secure and cost-effective remote access.
- Retail chains and enterprises can connect multiple locations using Site-to-Site VPN.
- Mission-critical organizations, such as healthcare providers, can enhance reliability with a hybrid VPN and ExpressRoute setup.
Alternative Connection Methods
When to Use ExpressRoute
ExpressRoute offers private, high-throughput, low-latency connections between on-premises networks and Azure. It bypasses the public internet, providing a more secure and reliable alternative for businesses with demanding networking needs.
Use Cases:
- Dedicated Private Connectivity: When an organization needs a direct, private connection between their on-premises infrastructure and Azure, ExpressRoute is the preferred solution.
- Low Latency, High-Speed Connections: Organizations with applications requiring high bandwidth and low-latency performance (e.g., financial institutions, media streaming) can benefit from ExpressRoute.
- Compliance Requirements: For industries with strict regulatory and compliance needs, ExpressRoute provides a secure, isolated communication channel.
Key Considerations:
- Cost: ExpressRoute can be more expensive than VPN, so it’s most suitable for mission-critical workloads.
- Geographical Location: ExpressRoute requires connections to specific edge locations. Ensure availability in your region before deployment.
Exploring Hybrid Networking Options
Hybrid networking setups combine different connectivity methods to optimize performance and availability. A hybrid network provides flexibility, enabling businesses to balance between cost, performance, and security.
Combining VPN and ExpressRoute for Diverse Workloads
- VPN for Remote Users: Utilize Point-to-Site (P2S) VPN for remote workers and smaller scale requirements.
- ExpressRoute for Critical Workloads: Use ExpressRoute to handle high-priority or high-throughput workloads that require dedicated, private connections.
Benefits:
- Cost Efficiency: Leverage VPN for less demanding workloads, reserving ExpressRoute for mission-critical applications.
- Redundancy and Failover: By deploying both solutions, organizations can ensure high availability through failover capabilities, where traffic is automatically rerouted in case of connection failure.
Using Azure Virtual WAN for Large-Scale Networking
For organizations with multiple branch offices, remote users, or global operations, Azure Virtual WAN is an ideal solution. It simplifies large-scale network management by creating a centralized hub-and-spoke model.
Key Features:
- Global Reach: Connect remote locations across the globe via a single hub in Azure.
- Unified Management: Streamlines network and VPN management through the Azure portal.
- Optimized for SD-WAN Integration: Easily integrates with SD-WAN providers to enhance network performance.
Software-Defined WAN (SD-WAN) Solutions
SD-WAN provides a modern approach to managing WAN connections by using software to control and optimize network traffic.
Benefits of SD-WAN Integration:
- Improved Connectivity and Performance: SD-WAN enhances application performance by dynamically routing traffic across multiple types of connections (e.g., MPLS, broadband, LTE).
- Centralized Control: With SD-WAN, organizations can centrally control their entire network’s performance, security, and routing policies.
- Cost-Effective: SD-WAN can help reduce networking costs by making use of lower-cost connections (like broadband) alongside traditional MPLS.
Deployment Considerations:
- Compatibility: Ensure that your SD-WAN solution integrates seamlessly with Azure VPN or ExpressRoute.
- Security: Maintain end-to-end encryption to protect data integrity while using SD-WAN for connectivity.
Considerations for Long-Term Management
As the complexity of the network grows, long-term monitoring, scaling, and automation become critical components in maintaining a seamless and efficient cloud infrastructure.
Monitoring and Maintenance
Use tools like Azure Monitor, Log Analytics, and Network Watcher to gain deep insights into the health, performance, and availability of your VPN connections and hybrid network infrastructure.
Key Activities:
- Track VPN Gateway Metrics: Use Azure Monitor to track throughput, latency, and connection status in real-time.
- Log Analytics: Leverage Log Analytics for detailed diagnostics, security alerts, and troubleshooting.
Automated Alerts:
- Set Up Alerts for Connectivity Issues: Use Azure Monitor alerts to notify you of any issues with VPN or ExpressRoute connections.
Scaling VPN Connections
As traffic and business needs grow, scaling VPN connections is necessary to ensure seamless performance and availability.
Scaling Strategies:
- Upgrade VPN Gateway SKUs: If you’re experiencing performance bottlenecks, consider upgrading your VPN Gateway to a more robust SKU (e.g., VpnGw2 or VpnGw3) to handle increased traffic demands.
- Leverage Multiple Gateways: For load balancing and redundancy, scale your network by deploying multiple VPN Gateways across different regions.
CLI/PowerShell Commands to Scale VPN:
Upgrade VPN Gateway SKU (CLI):
| bash az network vpn-gateway update --name <GatewayName> --resource-group <ResourceGroupName> --sku VpnGw2 |
Upgrade VPN Gateway SKU (PowerShell):
| powershell Set-AzVpnGateway -Name <GatewayName> -ResourceGroupName <ResourceGroupName> -Sku VpnGw2 |
In conclusion, effectively managing and optimizing your Azure VPN deployment is essential for maintaining a secure, scalable, and high-performing cloud network.