What is Azure Arc?
Source - Azure
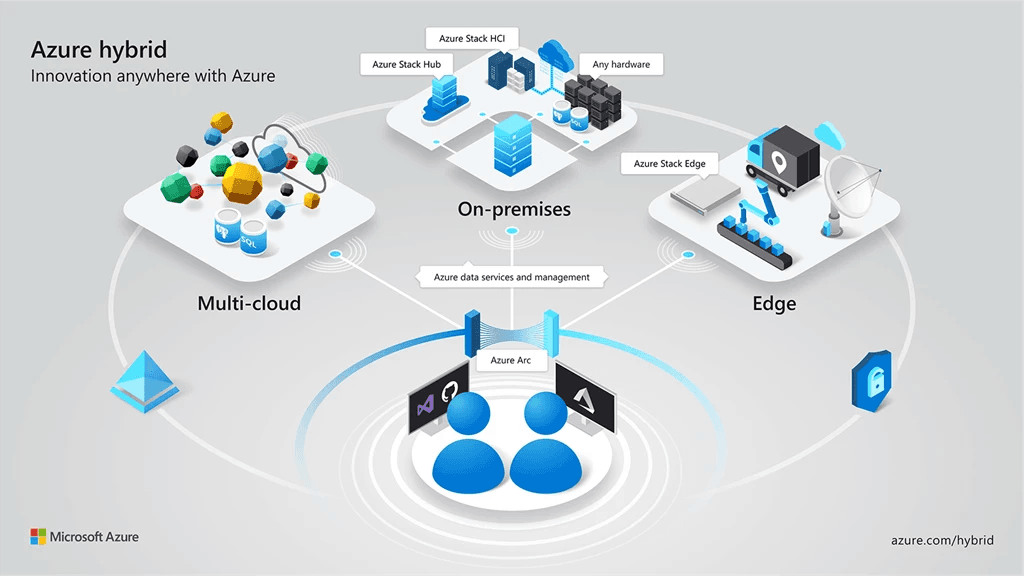
Azure Arc is a Microsoft platform that extends Azure’s management and governance capabilities to any infrastructure—on-premises, across other clouds, or at the edge. It enables organizations to project their existing non-Azure resources into Azure and manage them as if they were native to the cloud.
The Hybrid and Multi-Cloud Challenge
Modern enterprises rarely operate in a single environment. Distributed infrastructure, siloed tools, and inconsistent policies create significant challenges in maintaining visibility, compliance, and control across systems. Traditional tools often fall short in providing a unified governance model for such diverse ecosystems.
The Problems It Solves and What Makes It Unique
Azure Arc addresses the fragmented nature of hybrid and multi-cloud environments by offering:
- Unified Resource Management – A centralized control plane across on-premises servers, multi-cloud workloads, and Kubernetes clusters.
- Consistent Policy Enforcement – Apply security, compliance, and operational policies regardless of where the resource lives.
- Access to Azure Services Anywhere – Deploy services like Azure SQL Managed Instance or App Services outside Azure data centers.
- Scalable DevOps Integration – Use tools like GitOps, ARM, and Bicep to automate across environments.
- Non-disruptive Adoption – Arc integrates with existing systems and processes, enabling modernization without large migrations.By bridging the gap between diverse IT environments, Azure Arc introduces a cohesive visibility, compliance, and scalability model tailored for today’s distributed enterprises.
Common Misconceptions About Azure Arc
When exploring Azure Arc, it’s easy to confuse it with other cloud tools or misunderstand its purpose. Let’s clear up some of the most common misconceptions.
Is Azure Arc a cloud migration tool?
Many assume that Azure Arc is designed for cloud migration, but that’s not the case. Instead of moving workloads to Azure, Azure Arc helps businesses manage and govern their existing infrastructure—whether it’s on-premises, in other clouds, or at the edge. This means organizations can modernize their IT operations without undergoing complex migration processes.
Is Azure Arc a replacement for Azure Stack?
While both Azure Arc and Azure Stack extend Azure’s capabilities beyond the cloud, they serve different purposes. Azure Stack provides on-premises infrastructure that runs Azure services locally, whereas Azure Arc brings Azure’s management capabilities to any environment, regardless of where the infrastructure is hosted. Think of Azure Arc as a way to bring Azure’s control plane to your existing setup, rather than replacing it with Azure-like infrastructure.
Can Azure Arc work without Azure services?
Since Azure Arc is an extension of Azure’s management ecosystem, it requires integration with Azure services to unlock its full potential. While some basic functionalities, like server inventory, can work with minimal connectivity, key features—such as security enforcement, policy management, and data services—depend on Azure’s cloud-based capabilities. It’s not about replacing your existing systems but enhancing them with Azure’s robust governance and automation.
Bringing Hybrid Cloud Management Under One Roof
Azure Arc is not just a governance tool—it’s a foundational platform for managing hybrid and multi-cloud environments with consistency and agility. By extending Azure’s capabilities across distributed infrastructure, it enables IT teams to operate in complex environments without losing control or visibility.
Here’s how Azure Arc brings unified management to life across different layers of infrastructure:
Managing Servers Across Diverse Environments
Organizations often operate virtual machines and physical servers that span cloud providers, colocation facilities, and on-premises data centers. Azure Arc enables these non-Azure servers—both Windows and Linux—to be onboarded into Azure as first-class citizens.
Once connected, these machines become manageable through Azure Resource Manager, allowing teams to apply tags, enforce security policies, monitor health, and automate tasks as if they were running inside Azure. This brings long-missing parity between cloud-native and legacy workloads, without requiring a lift-and-shift migration.
Simplifying Kubernetes Operations at Scale
Kubernetes has become the standard for container orchestration—but managing clusters across multiple environments can introduce inconsistencies in configuration, governance, and security. Azure Arc addresses this by allowing organizations to connect any CNCF-compliant Kubernetes cluster, including those hosted on AWS, Google Cloud, or on-premises infrastructure.
Once connected, these clusters can be governed using Azure Policy, secured with Defender for Containers, and configured through GitOps-based automation. Azure Arc doesn’t replace native cloud tooling—it unifies it under a single policy and control framework, reducing the risk of misconfiguration while improving operational velocity.
Extending Azure Data Services Anywhere
Azure Arc goes beyond infrastructure governance by enabling the deployment of data services—such as Azure SQL Managed Instance and PostgreSQL Hyperscale—on any infrastructure. This is especially powerful for scenarios where data sovereignty, latency, or regulatory requirements prevent workloads from running in public cloud regions.
These Arc-enabled data services offer cloud-like benefits such as automatic scaling, high availability, patching, and unified billing, even when deployed outside Azure. Organizations gain the flexibility of running critical databases where they need them, without compromising manageability.
Bringing Azure Application Services Beyond the Cloud
Application modernization isn’t limited to moving workloads to the cloud. With Azure Arc, organizations can bring Azure App Services, Functions, Logic Apps, and other platform services to environments outside of Azure.
This allows teams to build and deploy cloud-native applications using Azure’s development model while hosting them in on-premises data centers or other clouds. Whether it’s for latency-sensitive workloads at the edge or applications bound by regulatory constraints, Azure Arc ensures consistency in development, deployment, and governance across environments.
Why It Matters?
By providing a unified control plane for servers, containers, data, and applications—regardless of where they run—Azure Arc enables organizations to adopt a truly hybrid cloud model. This consistency simplifies operations while enhancing visibility, governance, and security across environments.
But how does Azure Arc make this possible?
To truly understand its power, we need to look under the hood—at the architectural foundations and components that enable Azure Arc to operate seamlessly across such a diverse landscape.
Let’s explore the design principles and building blocks behind Azure Arc.
Inside Azure Arc: Architecture and Components
Now that we’ve seen what Azure Arc can do across hybrid environments—governing servers, managing Kubernetes, deploying data services, and extending applications—it’s worth exploring how it’s all made possible under the hood.
Azure Arc acts as a bridge between Azure and non-Azure environments. It allows resources outside of Azure—like on-premises servers, virtual machines, Kubernetes clusters, and even databases—to be projected into Azure as if they were native Azure resources.
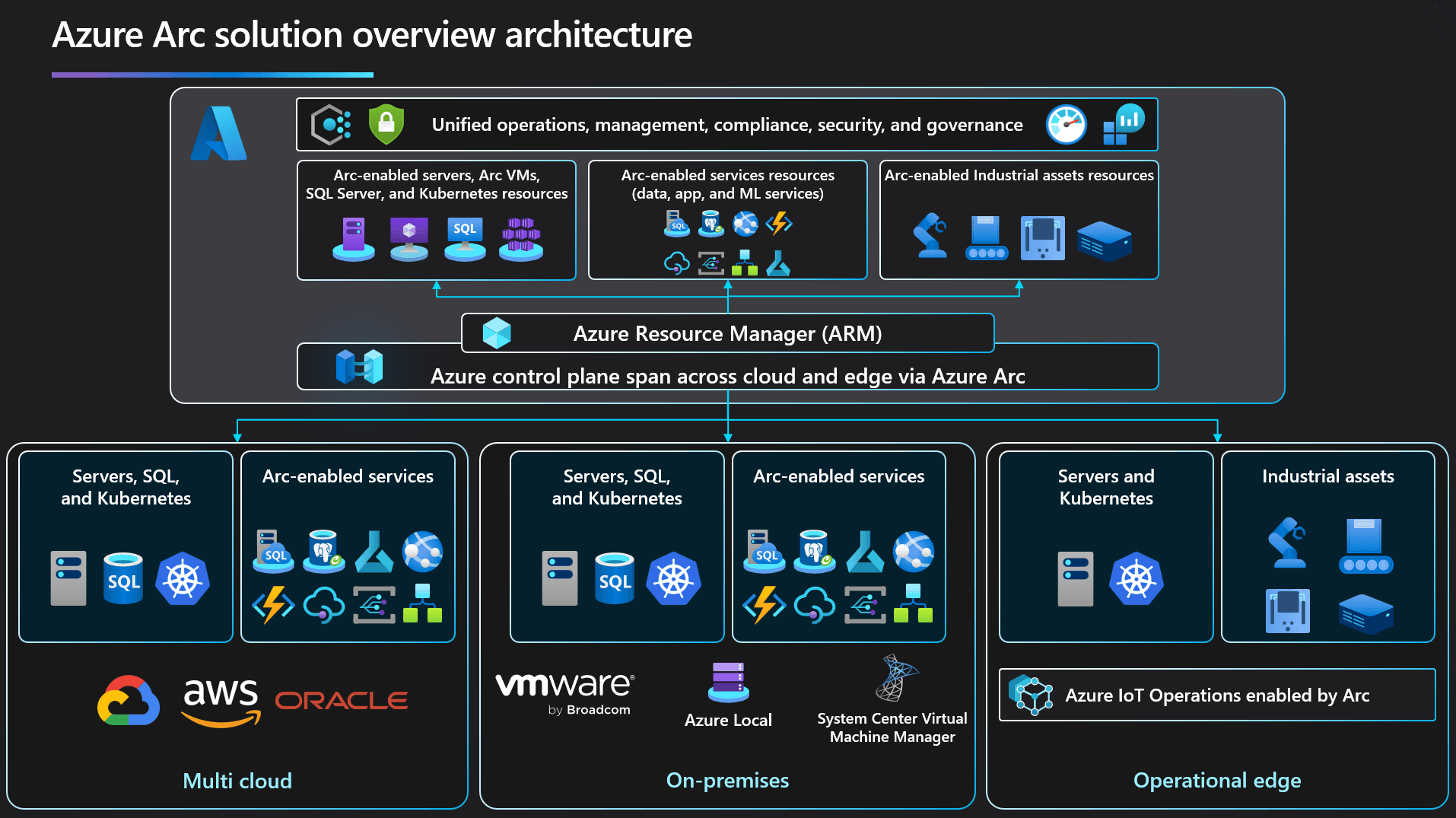
Key Components of Azure Arc Architecture
Source - Azure
To make all of this possible, Azure Arc relies on a few essential components. Here’s how they work together:
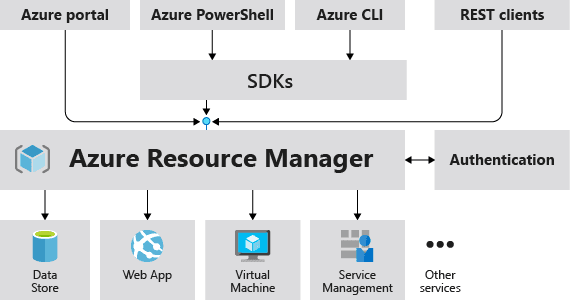
Azure Resource Manager
Source - Azure
This is the foundation of Azure’s governance model, and it plays the same role in Azure Arc. When a non-Azure resource is connected via Arc, it's represented in Resource Manager just like a native Azure resource. That means you can apply tags, assign permissions, enforce policies, and monitor performance—all through the Azure portal.
Azure Arc Agent (Connected Machine Agent)
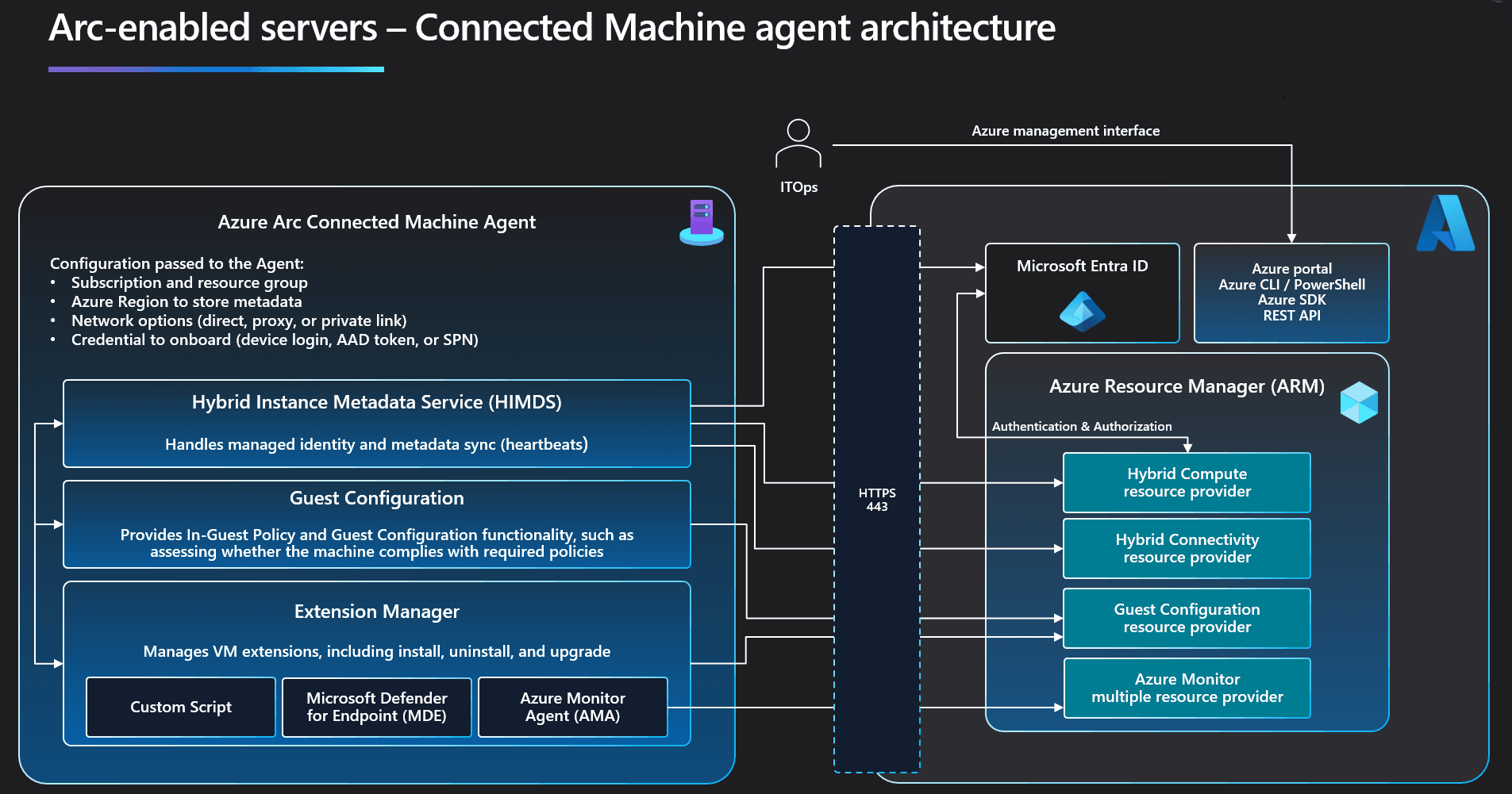
Source - Azure
For servers and VMs, this lightweight agent is what creates the connection to Azure. Once installed, it initiates secure outbound communication with Azure, allowing the machine to be onboarded and managed centrally. There's no need to open inbound ports—everything is outbound and encrypted.
Azure Arc-enabled Kubernetes Connectors:
For Kubernetes clusters—whether running on-prem or in another cloud—Azure Arc provides a way to register them with Azure. A set of agents and extensions are deployed in the cluster, enabling GitOps, policy enforcement, monitoring, and integration with Azure services like Defender for Cloud and Azure Monitor.
Azure Arc-enabled Data Services Layer:
When using Azure Arc to run Azure SQL Managed Instance or PostgreSQL Hyperscale outside Azure, the data controller comes into play. Deployed within a Kubernetes cluster, it orchestrates deployment, monitoring, scaling, and backups—giving you the feel of a managed service, without leaving your data center or preferred cloud.
Control Plane Integration:
Whether it’s servers, Kubernetes clusters, or data services, all Arc-enabled resources communicate with Azure over HTTPS, leveraging Azure’s control plane for visibility, governance, and operational insights.
Security by Design
All communication initiated by Arc is encrypted and outbound-only, reducing risk and simplifying network configurations. You maintain control over what gets connected, and how it's managed—no forced dependency, no intrusive takeover.
Servers need only the Connected Machine Agent. Kubernetes environments require agent-based extensions. For data services, the Kubernetes-based controller orchestrates everything locally. Azure remains the orchestrator—not the executor—allowing Arc to scale without being invasive.
A Modular, Extensible Design
Azure Arc doesn't require an all-or-nothing adoption. Its architecture is modular and composable, letting you adopt capabilities as needed:
- Start with server inventory and policy enforcement
- Expand to Kubernetes governance and GitOps
- Layer in data services where latency or compliance prevents public cloud adoption
This flexibility lets teams move at their own pace while standardizing operations across platforms.
Security and Governance Benefits
Managing modern infrastructure goes beyond just provisioning resources—it requires establishing consistent security, access control, and compliance across distributed systems. Azure Arc brings these capabilities into a single framework.
Policy Enforcement Across Environments
With Azure Arc, organizations can extend Azure Policy to resources outside of Azure, including on-premises servers and Kubernetes clusters. This allows the enforcement of security baselines, tagging standards, and regulatory requirements uniformly across environments.
Centralized Access and Role Management
Through Azure Active Directory (AAD), Azure Arc enables role-based access control (RBAC) for all Arc-enabled resources. This centralization reduces complexity and ensures consistent identity and access governance regardless of where resources are hosted.
Audit, Compliance, and Threat Detection
Azure Arc integrates with tools like Microsoft Defender for Cloud and Azure Monitor, offering unified audit trails, threat protection, and real-time insights. This is especially valuable for regulated industries that need to demonstrate continuous compliance across hybrid or disconnected environments.
By consolidating governance and security into a single operating model, Azure Arc reduces the risk of configuration drift, enhances policy consistency, and strengthens enterprise resilience—without sacrificing operational agility.
Cost Considerations
Azure Arc promises more than just operational flexibility—it also offers a cost model that supports smart hybrid and multi-cloud strategies. But like any enterprise tool, understanding what’s free, what’s paid, and how to optimize costs is key to getting the most out of it.
Let’s break down how Azure Arc influences your cloud and on-prem expenses and where it can either save money or require strategic investment.
How does Azure Arc Impact cost Structure?
At its core, Azure Arc is not a standalone product with a license—it’s a bridge for extending Azure’s management plane. That means:
- Connecting resources (like servers and clusters) is free.
- You only pay when you activate specific Azure services (e.g., Defender for Cloud, SQL Managed Instance).
- You gain savings from not migrating workloads unnecessarily.
- You centralize operations, reducing tool sprawl and administrative overhead.
These efficiencies are especially valuable in large, complex environments where scattered tools and manual workflows drive up operational costs.
Licensing and Pricing Model Overview
Here’s a closer look at the specific costs associated with Azure Arc services:
| Azure Arc Feature | Pricing (as of 2024) | Details |
| Azure Arc-enabled Servers | Free | Inventory, tagging, policy assignment, and visibility. |
| Azure Monitor (Arc-connected servers) | $2.30 per GB ingested + $0.10/GB retained (30+ days) | Based on Log Analytics pricing. |
| Microsoft Defender for Servers (via Arc) | $6 per server/month (Plan 1) | Includes threat detection, EDR, and integration with Sentinel. |
| Azure Arc-enabled Kubernetes | Free to connect | You only pay for enabled services (e.g., Monitor, Defender for Containers). |
| Defender for Containers (Kubernetes) | $7 per vCore/month | Billed per cluster vCore. |
| Azure Arc-enabled SQL Managed Instance | $0.27/hour per vCore (General Purpose) <br> $0.52/hour per vCore (BC) | Azure Hybrid Benefit applies for eligible SQL licenses. |
| Azure Arc-enabled PostgreSQL Hyperscale | $0.395/hour per vCore | Managed experience on your own infrastructure. |
| Azure Policy & Governance Tools | Free | Policy definition and assignment via Azure portal. |
| Azure Automation / Update Management | $0.002/min per job | Based on runtime duration. |
Best Practices for Optimizing Costs
- Use Azure Hybrid Benefit
Bring your existing Windows Server or SQL Server licenses to significantly reduce Azure Arc-enabled data service costs. - Monitor Ingestion & Retention
Be cautious with Azure Monitor logs—control ingestion volume and retention periods to avoid ballooning analytics costs. - Schedule Non-Critical Resources
Automate shutdowns of dev/test resources outside business hours using Azure Automation or Logic Apps. - Consolidate Security and Monitoring
Use bundled services like Defender for Cloud for centralized threat protection and compliance scanning across environments. - Align SKUs to Workload Type
Choose General Purpose vs. Business Critical SKUs for SQL based on IOPS, latency, and availability requirements—don’t overprovision.
Summary Table: Azure Arc Cost Snapshot
| Category | Cost Estimate | Optimization Tip |
| Arc-enabled Server Management | Free | Use for inventory, policy, tagging at zero cost. |
| Azure Monitor (Logs) | $2.30/GB ingested | Filter logs; use retention policies. |
| Defender for Servers | $6/server/month | Bundle with Azure Security Center for broader coverage. |
| Arc-enabled SQL MI (General) | ~$200/month (1 vCore) | Use Hybrid Benefit if eligible. |
| Arc-enabled PostgreSQL | ~$285/month (1 vCore) | Use scaling to match demand. |
| Defender for Containers | $7/vCore/month | Optimize vCore allocation in clusters. |
| Azure Automation Jobs | $0.002/min | Schedule jobs during low-demand periods. |
Note: Prices are based on publicly available Azure rates as of early 2024 and are subject to change. Always verify against the Azure Pricing Calculator and your specific region for accurate estimates.
Getting Started with Azure Arc
Getting started with Azure Arc doesn’t require a full-scale cloud migration or architectural overhaul. In fact, one of its biggest strengths is how easily it integrates into your existing environment—whether that’s a traditional data center, a public cloud provider, or a fleet of edge devices.
This section outlines what you need to begin and how to onboard your infrastructure into Azure using a consistent and guided approach.
Before You Begin: What You’ll Need
To successfully onboard resources to Azure Arc, make sure you have the following in place:
- An active Azure subscription – Azure Arc is an Azure-native service, so this is a prerequisite.
- Supported infrastructure – This includes physical servers (Windows/Linux), virtual machines, Kubernetes clusters, or environments that can host Arc-enabled data services.
- Network connectivity – The connected resources need outbound HTTPS access to Azure. There’s no need to open inbound ports or expose sensitive systems.
Once these requirements are met, onboarding becomes a structured, repeatable process.
Step-by-Step: Onboarding Your First Resource
Azure Arc supports onboarding through the Azure portal, Azure CLI, and automation tools like ARM templates or Bicep. Here's a simple portal-based walkthrough to illustrate the process:
- Sign in to the Azure portal
Access Azure Portal with the appropriate credentials. - Navigate to Azure Arc
Use the search bar to locate “Azure Arc” and select the relevant service type: servers, Kubernetes, or data services. - Register your resource
- For servers: Install the Connected Machine Agent and register it using a script provided in the portal.
- For Kubernetes: Deploy the Arc agents via a Helm chart.
- For data services: Deploy the Azure Arc Data Controller within a supported Kubernetes environment.
- Apply policies and tools
Once onboarded, you can apply Azure Policies, enable monitoring, and integrate the resource with Azure services like Defender for Cloud.
Essential Tools to Support Your Journey
- Azure CLI – For scripted deployments and advanced management via command-line interface.
- Azure Policy – To standardize governance and automate compliance.
- Azure Monitor – For collecting telemetry, setting alerts, and gaining visibility into resource health.
- Azure Resource Graph – For querying and managing large sets of Arc-enabled resources efficiently.
Whether you're onboarding a single server or scaling across hundreds of clusters, Azure Arc’s tooling is consistent, flexible, and designed to integrate into your existing workflows.
Azure Arc in Action: A Hands-On Guide
After understanding the architecture and components behind Azure Arc, the next question is: What does it feel like in action? How does it function when applied to the complexities of a real IT landscape?
This section walks through three core scenarios that demonstrate how Azure Arc brings tangible value—from onboarding a single server to managing complex Kubernetes clusters and running data services in environments far outside the Azure cloud.
Connecting a Traditional Server to Azure: From Legacy to Cloud-Connected
Consider a typical enterprise scenario: an on-premises Windows Server running a critical legacy application. It’s stable but isolated—outside your cloud governance model.
With Azure Arc, that server becomes a first-class citizen in Azure, without needing to migrate it.
Here’s how that transformation unfolds:
- The lightweight Connected Machine Agent is installed on the server.
- A secure script is run to register it with Azure Arc, projecting it into Azure as a manageable resource.
- Instantly, it's visible in the Azure portal—now governed by Azure Policies, secured with role-based access controls, and monitored just like any VM running natively in Azure.
This turns legacy infrastructure into a cloud-aligned asset, ready for central visibility, policy enforcement, and operational monitoring.
Kubernetes Management Across Cloud Boundaries: A Unified Control Plane
Now imagine your team running Kubernetes clusters in AWS, on-premises, and Azure. Each behaves differently, is secured differently, and is monitored separately. This fragmentation creates operational drag and governance risk.
Azure Arc rewires that fragmentation—without touching your workloads.
Once Arc-enabled:
- The cluster is registered with Azure using a Helm-based deployment that installs Arc agents and extensions.
- The moment it’s connected, you can apply GitOps configurations, deploy Azure Policies, and integrate security tools like Defender for Containers.
- Every cluster—regardless of where it runs—is brought under a single governance umbrella.
Instead of managing multiple tools and dashboards, you now have one—backed by Azure.
Running Azure SQL Outside Azure: Compliance Without Compromise
Consider a bank operating under strict regulatory controls. It can’t move customer data to the cloud—but still wants cloud-grade manageability for its databases.
With Azure Arc-enabled data services, that’s not only possible—it’s seamless.
The process starts by deploying the Azure Arc Data Controller into an existing Kubernetes cluster on-premises. This controller enables the provisioning of Azure SQL Managed Instances or PostgreSQL Hyperscale—with built-in backup, scaling, telemetry, and policy controls.
From the Azure portal, these databases appear just like their cloud-native counterparts. Yet, the data never leaves your data center.
In essence, you gain a managed cloud database experience—without surrendering data sovereignty or infrastructure control.
Real-World Use Cases
With Azure Arc’s flexible architecture and unified control plane in place, organizations can do more than just connect infrastructure—they can transform how they manage, secure, and scale IT operations across complex environments.
Let’s explore how Azure Arc is being put into action across industries, helping organizations overcome unique challenges without reinventing their infrastructure.
Centralized governance for enterprises
For large enterprises with thousands of servers spread across regions and environments, maintaining consistent governance is daunting. Azure Arc makes this manageable by projecting all resources into Azure’s control plane.
- A global insurance company uses Arc to apply standardized security policies across 5,000+ Windows and Linux servers, regardless of whether they run in Azure, on-premises, or another cloud.
- Configuration drift is reduced through Azure Policy, while role-based access ensures accountability at every level.
Managing Kubernetes clusters across clouds
For large enterprises with thousands of servers spread across regions and environments, maintaining consistent governance is daunting. Azure Arc makes this manageable by projecting all resources into Azure’s control plane.
- A global insurance company uses Arc to apply standardized security policies across 5,000+ Windows and Linux servers, regardless of whether they run in Azure, on-premises, or in another cloud.
- Configuration drift is reduced through Azure Policy, while role-based access ensures accountability at every level.
Running databases in offline or regulated environments
In highly regulated industries, moving sensitive data to the cloud is often not an option. Azure Arc offers a way to bring Azure capabilities to the data instead.
- A government agency uses Arc-enabled SQL Managed Instances in its own data center, ensuring compliance with national data residency laws while still benefiting from Azure’s automated scaling, patching, and monitoring.
- Similarly, a financial firm runs databases in a private environment but gains cloud-like insights through Arc’s data services layer.
Managing workloads at the edge
Retail and manufacturing environments often rely on edge devices and remote infrastructure that can’t depend on a persistent cloud connection. Azure Arc empowers these use cases with consistent deployment, monitoring, and policy enforcement.
- A retail chain uses Arc to deploy inventory management applications across hundreds of stores, each with limited IT staffing. Centralized control reduces complexity and downtime.
- A manufacturing company monitors production-line telemetry and machine learning models at edge sites, all managed through Azure Arc without sacrificing latency or uptime.
Limitations and Considerations
While Azure Arc brings impressive flexibility and control to hybrid and multi-cloud environments, it’s important to understand its boundaries. Like any technology, it's not a one-size-fits-all solution. Knowing where it is useful—and where it might not—helps you make informed decisions about when and how to use it.
Performance and Latency Considerations
Azure Arc depends on cloud connectivity for most of its management capabilities. For workloads in latency-sensitive environments or highly disconnected networks, this could introduce delays in monitoring, policy enforcement, or operations.
While Azure Arc is designed to be lightweight and asynchronous, it's still not ideal for real-time use cases that require split-second responsiveness or local-only execution with zero connectivity.
Network and Connectivity Requirements
One of the benefits of Azure Arc is that it doesn't require inbound connections from Azure to your infrastructure. Everything communicates outbound over HTTPS, which simplifies firewall configuration.
However, this means that reliable internet access is a must, particularly for scenarios involving policy assignments, security scans, or GitOps-based configuration updates. For highly regulated or air-gapped environments, Azure Arc may require adjustments—or may not be feasible without workarounds.
When Azure Arc Might Not Be the Best Fit?
Azure Arc is incredibly powerful, but it’s not intended to replace every tool in your stack. For instance:
- If you're already deeply invested in another multi-cloud management platform with specialized features (like advanced FinOps or non-Azure-native integrations), Arc might feel duplicative.
- In completely offline or disconnected environments where cloud connectivity isn’t an option—even intermittently—Azure Stack Hub or other local infrastructure might be better suited.
- For teams looking for full-fledged application platform abstraction (like serverless multi-cloud frameworks), Arc’s infrastructure-centric model might feel limiting.
Understanding these scenarios doesn’t reduce Arc’s value—it just helps place it where it can make the most impact.
Troubleshooting and Best Practices
Even well-architected platforms like Azure Arc can encounter friction in real-world environments. Knowing where issues typically arise—and how to resolve or avoid them—can ensure a smooth deployment and long-term stability.
Addressing Common Issues
One of the most frequent challenges is a connected machine not appearing in the Azure portal after onboarding. In most cases, this is linked to connectivity issues—specifically, the inability of the Azure Arc agent to communicate with required Azure endpoints. Since Azure Arc operates using outbound HTTPS traffic, confirming that firewalls or network policies are not blocking these connections is often the first step.
Another common scenario involves policy assignments not being enforced on Arc-enabled resources. This is typically the result of either missing or misconfigured Azure Policy definitions. Ensuring the policies are correctly scoped and compatible with Arc-connected resources often resolves the issue.
Unexpected behavior from extensions—such as monitoring agents or GitOps configurations—can also arise due to version mismatches or unsupported environments. Regular updates and validating compatibility during deployment can mitigate such issues.
Performance and Optimization Best Practices
To maintain performance and reduce management overhead, several best practices can be applied across Arc deployments:
- Target policies and configurations selectively. Avoid broad assignments at the subscription level unless necessary. Instead, use resource groups or management groups for precision.
- Monitor agent health and performance. While lightweight, Arc agents add operational overhead. Monitoring their impact, particularly on resource-constrained environments, helps maintain system stability.
- Automate onboarding at scale. Using tools like ARM templates, Terraform, or Bicep ensures consistency, speeds up deployment, and reduces human error.
- Standardize naming and tagging conventions. Applying consistent labels to all Arc-enabled resources enhances governance, visibility, and cost reporting.
- Keep configurations updated. Ensure the latest supported versions of agents and extensions are used to benefit from security patches, features, and performance improvements.
Deployment Patterns to Follow—and Avoid
Organizations seeing long-term success with Azure Arc tend to approach it with a platform mindset rather than treating it as a temporary bridge. Patterns that typically deliver strong outcomes include:
- Using GitOps for Kubernetes management. This approach brings consistency and version control to cluster configuration across environments.
- Aligning Arc deployments with existing governance structures. Integrating policy, identity, and monitoring from the start avoids fragmentation later.
However, some practices can limit the effectiveness of Arc:
- Over-customizing deployments without documentation. This often leads to fragile configurations that are difficult to scale or support.
- Onboarding resources without planning integration. Connecting servers or clusters to Arc without aligning them to governance or automation workflows can reduce the value Arc provides.
Migration Paths to Azure Arc
Adopting Azure Arc is not an all-or-nothing shift. It’s designed to integrate with existing environments, making it a practical step forward for organizations already operating in hybrid or multi-cloud models. Rather than requiring a disruptive overhaul, Azure Arc supports a phased, deliberate approach—one that aligns with enterprise priorities, governance strategies, and infrastructure realities.
For Organizations with Existing Hybrid Infrastructure
Many enterprises already operate across a mix of on-premises, cloud, and edge environments. In such cases, Azure Arc acts as an overlay—bringing unified visibility, control, and security without forcing migration or platform changes.
For example, existing on-premises Windows or Linux servers can be onboarded to Azure Arc using lightweight agents, allowing IT teams to manage them through Azure Resource Manager. Kubernetes clusters—whether running in a corporate data center or another cloud provider—can be registered with Azure Arc to enable policy enforcement, GitOps workflows, and integration with Azure services like Monitor and Defender.
This approach preserves existing investments while modernizing management and governance.
A Phased Adoption Strategy
Successful Azure Arc adoption typically follows a staged path:
- Assessment and Prioritization
Begin by identifying which resources would benefit most from centralized governance or enhanced security. This could include unmanaged servers, multi-cloud clusters, or systems in regulated environments. - Pilot Deployment
Select a small set of representative workloads—such as a Kubernetes cluster or a handful of VMs—to onboard as a proof of concept. This phase allows teams to validate connectivity, evaluate impact, and fine-tune policy configurations. - Expansion and Integration
Once the initial pilot demonstrates value, extend Arc capabilities across additional systems. Integrate with security, monitoring, automation, and CI/CD pipelines to reinforce governance and operational efficiency. - Operational Maturity
As adoption grows, establish standards for Arc onboarding, tagging, access control, and cost tracking. Formalizing these practices ensures scalability and consistency across business units and regions.
By following this gradual model, organizations can reduce risk, build confidence internally, and extract value from Azure Arc without disrupting current operations.
Azure Arc is a game-changer for businesses managing hybrid and multi-cloud environments. It simplifies governance, enhances security, and extends Azure services beyond the cloud. By adopting Azure Arc, organizations can achieve greater efficiency, scalability, and control over their IT landscape.