What is AWS STS?
AWS Security Token Service (STS) is a service provided by AWS to grant temporary, limited-privilege credentials for accessing AWS resources. Unlike permanent IAM credentials, which can last indefinitely, STS issues credentials that automatically expire after a set time, reducing the risk of unauthorized access.
Core Purpose and Functionality
The core purpose of AWS STS is to help secure access to your AWS resources by offering temporary credentials. These credentials can be used for a wide range of activities, such as cross-account access, federated login, or for granting limited-time access to applications or services that require AWS resources.
Where STS Fits in the AWS Ecosystem
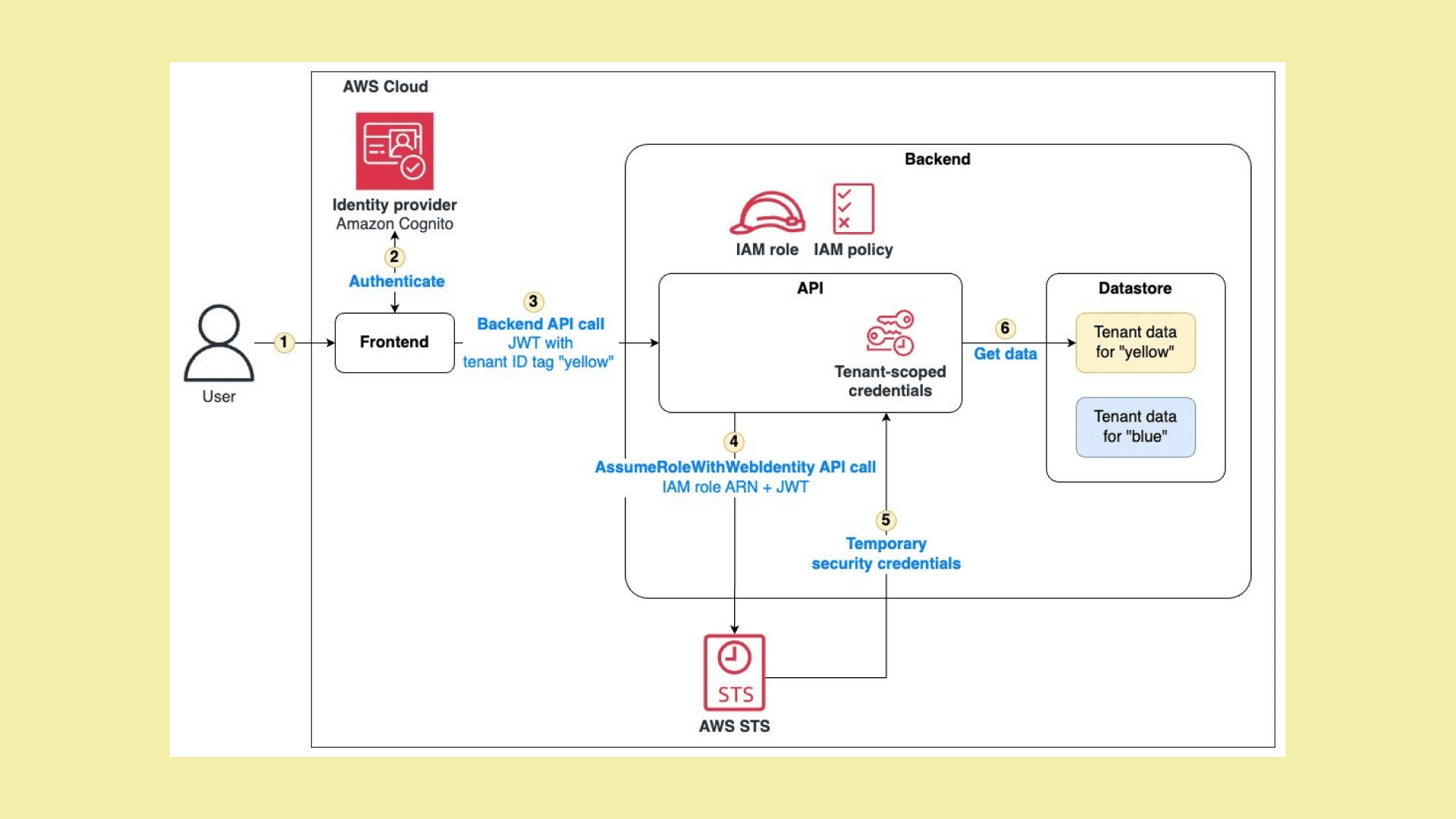
Source: AWS Security Blog
AWS STS integrates with several key AWS services, such as AWS IAM, Amazon Cognito, and AWS Organizations, playing a crucial role in securely managing access. It allows you to delegate permissions securely across accounts, provide temporary access to users, and facilitate federated identity management.
Key Features and Capabilities:
- Temporary Security Credentials: STS provides short-lived credentials, which expire after a specific duration (minutes to hours).
- Cross-Account Access: STS allows you to share resources securely across AWS accounts.
- Federated Authentication: Supports external identity providers, enabling users to log in to AWS without creating IAM users.
- Session Management: You can set policies for these temporary credentials and control the scope of permissions.
The Case for AWS STS
Understanding the Security Landscape
In the world of cloud computing, security is paramount. One of the biggest risks in traditional security models is the use of permanent access keys, which can expose your resources to unauthorized users if compromised. AWS STS solves this problem by issuing temporary credentials that expire automatically, reducing the impact of potential security breaches.
1. Risks of Permanent Access Keys
Permanent access keys (IAM access keys) remain valid until manually revoked, leaving your resources open to misuse if they are leaked or compromised. Attackers can misuse these keys indefinitely if they are not detected quickly.
2. Benefits of Temporary Credentials
The key advantage of temporary credentials is their short lifespan. If compromised, they provide a limited window for misuse and automatically expire, meaning no further action is required to revoke them. Additionally, temporary credentials can be restricted to specific roles, permissions, and timeframes, offering much more granular access control.
3. Real-World Security Incidents
A number of high-profile security incidents have occurred due to exposed IAM keys, often found in code repositories like GitHub. In these cases, attackers gained access to sensitive data or services, often with disastrous results. Using temporary credentials would have limited the time for such attacks to be effective, mitigating the damage.
Why Choose STS?
- Security: Temporary credentials significantly reduce the risk of unauthorized access and minimize the window of exposure.
- Flexibility: STS supports both cross-account access and federated access, giving you more control over who accesses your AWS resources.
- Convenience: Ideal for scenarios involving applications, mobile devices, and web services, where users and systems require time-bound access to resources.
Core Concepts and Components
Now that you have a basic understanding of AWS Security Token Service (STS), let’s dive deeper into its core concepts and components. In this section, we’ll explore the critical pieces that make up the temporary security credentials issued by AWS STS, as well as how they function within the AWS ecosystem. Whether you're new to AWS or a seasoned developer, understanding these components is key to securely managing access.
Temporary Security Credentials Deep Dive
When you use AWS STS, it generates temporary security credentials that allow users to access AWS resources for a limited period. These credentials consist of three essential components:
- Access Key ID: This unique identifier is used to access AWS resources.
- Secret Access Key: A secret key used to sign requests to AWS services.
- Session Token: This is used in every request to prove the validity of the session.
What makes these credentials special?
They’re temporary, which means they automatically expire after a set duration, typically between 15 minutes and 12 hours. This helps to mitigate the security risks associated with long-term access keys that might get exposed.
Token Lifecycle and Expiration
AWS STS operates on the principle of temporary access. This means that the credentials it issues have a lifecycle:
- Credential Issuance: When you request access (say, to assume a role), STS generates and returns these temporary credentials.
- Credential Usage: You use these credentials to interact with AWS resources.
- Expiration: Once the credentials expire (as per the duration set), they are no longer valid, and you must request new ones.
This lifecycle ensures that credentials cannot be misused for extended periods, minimizing the risk of unauthorized access.
Now, let’s look at how these temporary credentials come into play. The process begins when you need to assume a role. AWS STS makes this process simple and secure.
Here's a quick rundown of the role assumption process:
- Request to Assume a Role: A user (or service) sends a request to assume a role that has specific permissions tied to it.
- STS Validates the Request: AWS checks if the requester has the correct permissions to assume the role. This is based on the trust relationship defined in the role’s configuration.
- Temporary Credentials Issuance: If the request is valid, STS issues temporary security credentials (Access Key, Secret Key, and Session Token) to the user or service.
- Access to AWS Resources: The user or service can now use these credentials to access resources within the permissions granted by the role.
Key Components of AWS STS
There are several key components that make up the functionality of AWS STS. Here’s a breakdown:
- Roles and Policies: Roles are used to define what actions a user or service can perform, and policies help refine those permissions.
- Trust Relationships: These define who can assume a role. For example, a role might trust users from a specific AWS account or even external identity providers like Google or Facebook.
- Session Duration: The time period for which the temporary credentials are valid. Session duration can range from 15 minutes to 12 hours, depending on your requirements.
AWS STS in Action: Working Mechanism
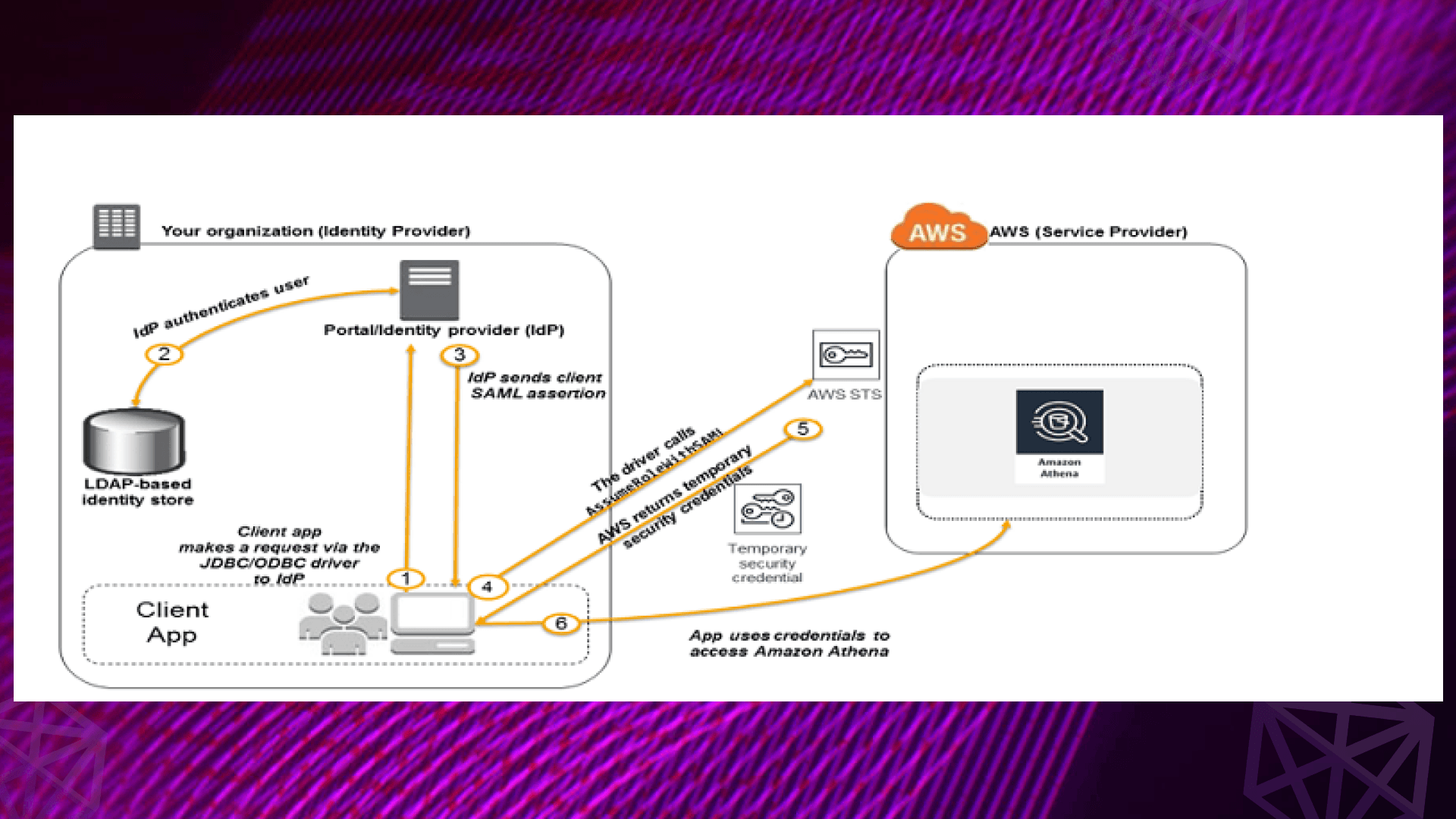
Source: AWS Blog
Now that we’ve covered the key concepts and components, let's take a closer look at how AWS STS actually works in practice. We’ll walk through a typical use case and explore the core API operations that enable this functionality.
Step-by-Step Operation Flow
To better understand how AWS STS operates, let’s break down the workflow:
- Authentication: The user or application authenticates using IAM credentials (or via an external identity provider).
- Role Assumption: The user requests to assume a role, providing their credentials and role-specific information.
- STS Issues Temporary Credentials: If the request is valid, STS returns temporary credentials (Access Key, Secret Key, and Session Token) to the requester.
- Access AWS Resources: The user or service uses the temporary credentials to interact with AWS resources, such as S3 buckets or EC2 instances.
- Expiration & Renewal: Once the temporary credentials expire, the process repeats if additional access is needed.
This seamless process ensures that no long-term keys are exposed and helps minimize security risks.
STS API Operations
AWS STS offers several operations that allow users to manage and configure temporary credentials. Here are the most commonly used API operations:
- AssumeRole: This is the most widely used operation, where a user or service assumes a role and is issued temporary credentials.
- GetSessionToken: For users already authenticated, this operation provides temporary credentials to interact with AWS services.
- AssumeRoleWithWebIdentity: This allows users to authenticate using an external identity provider (e.g., Google, Facebook).
- AssumeRoleWithSAML: This operation is used for integrating with corporate identity providers using the SAML 2.0 standard.
Each of these operations provides a secure way to access AWS resources without exposing permanent credentials.
Table: Key STS API Operations
| API Operation | Description | Use Case |
| AssumeRole | Allows a user to assume a role and obtain temporary credentials. | Most common use case for role-based access. |
| GetSessionToken | Issues temporary credentials for authenticated users. | Used when you need temporary access without assuming a role. |
| AssumeRoleWithWebIdentity | Allows web identities (e.g., Facebook, Google) to authenticate. | Common for mobile apps or third-party integrations. |
| AssumeRoleWithSAML | Provides temporary credentials based on a SAML identity. | Used in enterprise environments with corporate login systems.
|
Common Implementation Scenarios
Understanding how AWS STS can be applied in different scenarios will help you leverage its capabilities effectively. Whether it's managing access across multiple accounts, federating identities, or integrating with applications, STS offers flexible solutions for various use cases.
Cross-Account Access
In larger AWS environments, cross-account access is a common scenario. AWS STS enables users from one AWS account to securely assume roles in another account without using permanent credentials. This method significantly reduces the attack surface by eliminating the need for long-lived access keys.
How it Works?
Imagine you have two AWS accounts:
- Account A (source account): The user or service needs access to resources in Account B.
- Account B (target account): The account containing the resources.
Here’s how cross-account access is set up:
- Create an IAM Role in Account B: This role defines the permissions to access specific resources in Account B (e.g., S3 buckets or EC2 instances).
- Define a Trust Policy in Account B: The trust policy specifies which identities (e.g., users, roles) from Account A can assume the role in Account B.
- Assume the Role via STS in Account A: A user or service in Account A makes an API call to AWS STS’s AssumeRole operation to request temporary credentials. These credentials allow them to access resources in Account B.
Best Practices for Cross-Account Access:
- Least Privilege: Only grant the minimum necessary permissions to the assumed role. For example, if the user only needs to read from an S3 bucket, don’t grant them full S3 access.
- Role Chaining: While chaining roles can help access multiple accounts, it's best to avoid deep role chains as they introduce complexity and increase the chance of misconfigurations.
- Cross-Account Auditing: Use AWS CloudTrail to log and monitor cross-account role assumptions for better visibility into who’s accessing your resources.
Federation Scenarios
Federating users from external identity providers (IdPs) allows you to integrate with existing authentication systems, like corporate Active Directory or even social login providers. AWS STS supports multiple federation scenarios, making it versatile for diverse authentication needs.
Types of Federation:
- Web Identity Federation: You can authenticate users via external web identity providers such as Google, Facebook, or Amazon Cognito. This allows mobile apps or web applications to authenticate users without needing to store long-term credentials in your AWS environment.
How it works?
The user logs in via a web identity provider (e.g., Google). After authentication, the identity provider sends an authentication token to AWS STS, which exchanges it for temporary security credentials, granting access to AWS resources.
- SAML-based Federation: If your organization uses SAML 2.0 for Single Sign-On (SSO) (e.g., Microsoft Active Directory Federation Services), you can use SAML-based federation to allow users to authenticate with their corporate credentials and access AWS resources.
How it works?
After the user is authenticated by the corporate IdP, a SAML assertion is sent to AWS STS, which then issues temporary credentials for accessing AWS resources based on the permissions associated with the role.
- Custom Identity Broker: You can also integrate a custom identity broker to connect to non-AWS IdPs or to handle complex authentication workflows. This is useful when working with niche authentication systems or hybrid environments.
How it works?
The custom broker authenticates users and passes the required information (such as tokens or SAML assertions) to AWS STS, which generates temporary credentials for accessing AWS.
Best Practices for Federation:
- Token Validation: Always validate the tokens before passing them to STS to ensure they are legitimate and haven't been tampered with.
- Limit the Scope of Roles: Assign specific roles to federated users based on their need to access certain resources (e.g., different roles for different departments).
- Session Duration: Consider shorter session durations for federated identities, as this helps mitigate risks in case tokens are compromised.
Application Integration
AWS STS is also commonly used to integrate AWS with various types of applications. These could be mobile apps, web applications, or microservices that require secure, temporary credentials for accessing AWS resources.
How it Works for Mobile Apps?
For mobile apps, security is key. You can integrate AWS STS with Amazon Cognito to authenticate users via social identity providers (like Google or Facebook) or a custom identity provider. Once authenticated, STS will provide the app with temporary credentials to interact with AWS services securely (such as accessing S3 buckets or invoking Lambda functions).
How it Works for Web Applications:
Web apps often use SAML-based federation or Cognito Identity Pools to authenticate users. Once authenticated, the app can retrieve temporary credentials through AWS STS to securely make requests to AWS resources like DynamoDB, S3, or EC2.
How it Works for Microservices:
Microservices in AWS environments often use IAM roles with STS to authenticate and gain temporary access to resources like Amazon SQS, SNS, or even EC2 instances within a VPC. When one microservice needs access to another service, it assumes a role to access the necessary resources securely.
Security Best Practices and Optimization
When using AWS STS, adhering to security best practices is critical to ensure the safe and efficient use of temporary credentials. By following these best practices, you can significantly reduce the risk of security incidents while also optimizing performance.
Security Guidelines
- Least Privilege Access:
Always follow the principle of least privilege. When defining roles in AWS, ensure they have only the permissions required to perform their specific tasks. Avoid granting broad permissions like * (wildcard).
- Use MFA (Multi-Factor Authentication):
For sensitive operations (like assuming critical roles), enforce MFA. This adds an extra layer of security by requiring a second factor (e.g., a smartphone app) in addition to the usual credentials.
- Short Session Duration:
By default, STS credentials expire after a set time (up to 12 hours). However, you should aim to use the shortest session duration possible. This minimizes the window in which credentials could be misused if compromised.
- Monitor and Audit STS Requests:
Use AWS CloudTrail to log and monitor all STS API calls. This provides visibility into who’s assuming which roles and helps in identifying any unusual or unauthorized behavior.
Performance Optimization
While security is critical, performance is also a key consideration. By optimizing your STS usage, you can reduce overhead and ensure that your applications work efficiently.
- Caching Tokens:
Once you’ve obtained temporary credentials from STS, store them securely for future use (e.g., in an encrypted cache). This reduces the need to request credentials repeatedly, which can reduce latency and API call overhead.
- Token Refresh Strategies:
Implement automatic token refresh mechanisms to ensure your sessions remain active without requiring user intervention. This is particularly important in scenarios where long-running processes or applications need to continuously interact with AWS resources.
- Regional Endpoints:
AWS STS has regional endpoints, which means you should make sure to use the endpoint closest to your application to minimize latency and improve performance.
| Optimization Strategy | Benefit |
| Caching Tokens | Reduces the need to request new tokens repeatedly, improving efficiency and reducing latency. |
| Token Refresh Strategies | Keeps sessions valid without the need for manual re-authentication, ensuring seamless operations. |
| Regional Endpoints | Minimizes latency by connecting to the nearest AWS region. |
Troubleshooting and Error Resolution
Even with a solid setup, issues may arise when using AWS STS. Understanding common errors and how to troubleshoot them will help ensure that you can quickly resolve any problems and keep your AWS environment running smoothly.
Common Error Scenarios
- Access Denied:
This error typically occurs when the IAM role or policy doesn’t allow the requested action. Double-check the permissions in the IAM role and ensure that the trust policy is properly configured.
- Token Expiration:
STS credentials have a limited lifespan. If you attempt to use expired credentials, you will receive an error indicating the token has expired. Ensure your applications handle token expiration gracefully by refreshing credentials when needed.
- Cross-Account Access Problems:
Cross-account access issues often stem from misconfigured trust relationships or incorrect IAM role policies. Ensure the target account trusts the source account and that both accounts have the appropriate permissions set.
Debugging Techniques
- CloudTrail Logs:
Use AWS CloudTrail to track all STS API requests and responses. CloudTrail logs provide detailed information about which role was assumed, who assumed it, and from which IP address, helping you pinpoint issues.
- Error Message Interpretation:
AWS error messages are often descriptive. If you encounter an error, carefully read the message—it usually indicates which part of the request failed (e.g., invalid role, insufficient permissions).
- Resolution Workflows:
Start by reviewing the permissions and trust policies associated with roles. If the error persists, check the token’s expiration or look for misconfigurations in cross-account trust relationships.
Advanced Implementation Patterns
As your use of AWS Security Token Service (STS) expands within your organization, you may need to consider more complex, enterprise-scale deployments. These scenarios often involve multi-account strategies, integration with corporate identity systems, and more sophisticated federated access patterns. Let’s explore some of these advanced patterns and how they can be implemented effectively.
Enterprise-Scale Deployments
When working with multiple AWS accounts within an organization, managing security and access at scale can become tricky. This is where multi-account strategies come in handy. AWS provides tools like AWS Organizations to manage multiple accounts, but integrating STS with it can take your security model a step further.
Here’s how it works?
- Centralized Role Management: With multiple accounts, you can create centralized roles that allow specific users or services in one account to assume roles in other accounts securely. This is especially useful when consolidating billing or managing cross-account access for specific resources.
- Cross-Account Access: By utilizing STS with IAM roles and trust policies, you can allow users or services in one AWS account to securely access resources in another, without needing to create separate access keys or hard-code credentials.
Federated Access for Enterprises
Many enterprises already have identity management systems in place, such as Active Directory or other SAML-based identity providers (IdPs). In these scenarios, you can use STS to integrate with these systems, allowing users to access AWS resources without needing separate AWS credentials.
- SAML Federation: For organizations that use SAML 2.0-based IdPs, STS can facilitate SAML-based authentication, enabling users to authenticate against their corporate directory and assume roles in AWS without creating IAM users.
- OIDC Federation: If your organization uses an OIDC-based provider (like Google or Okta), you can leverage STS with AssumeRoleWithWebIdentity to allow users to authenticate using their existing credentials and access AWS resources seamlessly.
These advanced federated scenarios allow enterprises to use existing identity systems, reducing the overhead of managing separate AWS identities and improving security by eliminating the need for permanent credentials.
Scaling Federated Identity Solutions
When your enterprise requires identity federation at scale, consider leveraging Amazon Cognito in combination with STS. For instance, if you need to integrate multiple identity providers (Google, Facebook, corporate directories) for a mobile or web app, Cognito can handle the authentication, while STS can provide the appropriate temporary credentials for AWS resources.
This hybrid approach allows you to scale identity management effectively while maintaining secure access to AWS services.
Comparing Authentication Methods
Choosing the right authentication and authorization method in AWS can be confusing, especially when dealing with multiple services that serve different needs. To make things clearer, let’s compare AWS STS, IAM, and Amazon Cognito, three services that handle identity and access management, but in different ways.
Understanding the Differences
Each service has its strengths and use cases. Let’s break down their key differences in a comparison table for easier understanding.
AWS STS vs IAM vs Amazon Cognito
| Feature | AWS STS (Security Token Service) | IAM (Identity and Access Management) | Amazon Cognito |
| Type of Credentials | Temporary credentials (access keys, secret keys, session tokens) | Permanent credentials (long-lived access keys, secret keys, users, roles) | Temporary credentials for users authenticated via external providers or custom IdPs |
| Primary Use Case | Temporary access to AWS resources, cross-account access, federated users | Long-term access management within AWS, controlling who can access what | User authentication, user management, and temporary credentials for apps |
| Expiration of Credentials | Credentials expire after a specified time (from minutes to several hours) | Credentials do not expire unless manually revoked | Credentials are temporary (e.g., session tokens) with expiration (user sessions) |
| Use with External Identity Providers | Supports federation with external IdPs (SAML, OIDC) | Limited support, typically via IAM roles for cross-account access | Built-in support for social IdPs (Google, Facebook), SAML, and custom IdPs |
| Granular Permissions | Temporary permissions based on role assumption | Permanent, fine-grained access control based on policies attached to users and roles | Fine-grained access control for web/mobile apps based on user attributes |
| Typical Use Cases | Cross-account access, federated identities, temporary permissions for services | Managing AWS resource access for users and roles, infrastructure access | Web and mobile app user authentication and management, social logins |
| Session Duration Control | Can be controlled when assuming a role (session duration is customizable) | N/A (access keys are permanent until manually revoked) | Session duration for users can be controlled (e.g., short-lived tokens) |
| Security Considerations | Reduced risk from temporary credentials, automatic expiration, and rotation | Long-lived access keys increase the risk of exposure if compromised | Secure, federated sign-in, but requires secure handling of credentials for sessions |
STS vs IAM vs Cognito: When to Use Each Service?
- AWS STS is perfect for scenarios where you need temporary, limited-time access to AWS resources, especially in cross-account access and federated scenarios. It’s a good choice for third-party integrations, such as vendors or temporary workers, who don’t need permanent access keys.
- IAM is your go-to service for long-term management of AWS resource access. It’s best suited for internal users, AWS services, or any situation where you need fine-grained, permanent access control to AWS resources.
- Amazon Cognito is ideal for user authentication and management in applications. Whether you are building mobile or web applications that need to authenticate users, Cognito integrates with external identity providers (like social media accounts) and provides secure temporary AWS credentials via STS for app backends.
By understanding the differences between these services and choosing the right one for your use case, you can design a more secure and efficient authentication and authorization system in AWS.
Integration Patterns: Combining Services Effectively
Now that we understand the differences between AWS STS, IAM, and Cognito, let’s look at some common integration patterns that combine these services to deliver seamless, secure, and scalable authentication and authorization solutions.
1. Combining STS with IAM for Cross-Account Access
If you have multiple AWS accounts within your organization, you can use AWS STS with IAM to enable cross-account access. This pattern is commonly used for organizations that have separate accounts for development, testing, production, and more. Instead of creating multiple IAM users across different accounts, you can use STS AssumeRole to allow users in one account to assume a role in another account temporarily.
Example Use Case:
- A developer in the Development Account needs access to resources in the Production Account for deployment. Instead of giving the developer permanent credentials for the production environment, you set up a role in the Production Account with a trust policy that allows the Developer Account’s IAM role to assume it. This way, the developer gets temporary credentials for the production environment, reducing security risks.
2. STS + SAML for Federated Access with External Identity Providers
Many organizations rely on external identity providers (IdPs) like Active Directory, Okta, or OneLogin for managing employee credentials. With AWS STS, you can use SAML-based federation to allow your employees to authenticate against their corporate IdP and assume roles in AWS, gaining access to AWS resources.
Example Use Case:
- A company has employees using a centralized corporate directory like Active Directory for authentication. By configuring SAML federation in STS, employees can sign in using their existing credentials, and the IdP passes a SAML assertion to STS to grant temporary credentials for accessing AWS resources.
3. Cognito + STS for User Authentication in Apps
When building a web or mobile application, Amazon Cognito can manage your users and authentication, while STS issues temporary credentials to access AWS resources on the backend. This is ideal for serverless applications or scenarios where users interact with AWS services like S3, DynamoDB, or API Gateway through your application.
Example Use Case:
- A mobile app requires users to upload files to an S3 bucket. You use Amazon Cognito to authenticate users and obtain an identity token. The app then calls AWS STS (AssumeRoleWithWebIdentity) to get temporary credentials, which are used to upload files directly to S3, all while ensuring that the user’s access rights are scoped and temporary.
4. Using IAM + Cognito for Scalable App Management
If your application has a large number of users, Cognito can be used to authenticate and manage those users, and IAM can be used to set up resource-based policies that grant or restrict access to AWS resources. For example, you can define IAM roles that grant access to specific services based on user attributes, and use Cognito to map those attributes to IAM policies.
Example Use Case:
- An e-commerce platform uses Cognito for user registration and login. Once logged in, users are granted access to the platform’s services using IAM roles that are assigned based on their user type (e.g., regular users, admins). For example, an admin user gets a role with permissions to manage AWS resources, while a regular user only has access to their personal data.
Integration Strategy: Hybrid Solutions for Flexibility
Many enterprises don’t rely on a single solution, but rather on hybrid models that combine IAM, STS, and Cognito to meet different needs across their organization. For instance, IAM roles could be used for internal services and users, Cognito could manage user authentication for web and mobile apps, and STS could facilitate temporary cross-account access or federated identity scenarios.
Best Practices for Integration:
- Use Temporary Credentials Where Possible: Always prefer temporary credentials (via STS) over long-term IAM credentials for external users or services.
- Granular Access Control: Ensure that IAM policies are finely tuned to only allow necessary permissions based on roles, user attributes, and session duration.
- Leverage Federated Identities: Use Cognito or STS to integrate your AWS environment with external identity providers for seamless and secure authentication.
Future-Proofing Your STS Implementation
As the cloud landscape continues to evolve, so too does the need for scalable, secure, and flexible identity and access management. With emerging technologies and new security frameworks, AWS Security Token Service (STS) plays an important role in ensuring that your system remains robust and adaptive to the future needs of your business. In this section, we will look at the emerging trends in identity management and the best practices to future-proof your STS implementation.
Emerging Trends
In recent years, a few critical trends have emerged in the world of cloud security and identity management. AWS STS, along with other identity services, is evolving to meet these trends and ensure that organizations can adapt seamlessly.
Zero Trust Architecture (ZTA)
Zero Trust is a security model that assumes no one, whether inside or outside the network, can be trusted by default. Every request for access, regardless of origin, is thoroughly verified before being granted. This approach helps mitigate insider threats and unauthorized access.
How STS Fits in a Zero Trust Model?
- STS plays a crucial role in enforcing Zero Trust by issuing temporary security credentials that are scoped and limited by the specific role or task a user or service needs to perform. This minimizes the attack surface and reduces the risk of long-lived credentials being exposed.
- Continuous authentication and authorization: In a Zero Trust environment, using STS with IAM roles and policies ensures that access to resources is continuously validated, not just during initial sign-on.
Identity-First Security
As organizations move towards Identity-First Security, managing identities becomes the core focus of security strategies. This model emphasizes securing access based on the identity of users or services rather than just network boundaries or device security.
How STS Supports Identity-First Security:
- Centralized identity management: AWS STS can integrate with centralized identity solutions like AWS Cognito, Active Directory, or SAML-based providers, allowing organizations to manage identities from a central point and grant access to AWS resources based on the identity’s specific permissions.
- Role-based access control (RBAC): By combining STS with IAM roles, organizations can ensure that access is granted based on the user’s identity, with policies reflecting the level of access they should have.
Best Practices for Scalability
When planning for the future, scalability is a critical consideration. As your organization grows and your infrastructure evolves, you will need to ensure that your STS implementation can scale efficiently.
1. Architecture Considerations
To future-proof your STS implementation, consider these architectural best practices:
- Leverage Automated Role Management: As your organization scales, the number of roles, policies, and users will increase. Automating role creation and management can help reduce manual overhead and the potential for human error. You can use services like AWS CloudFormation or AWS Organizations to automate this process.
- Use Fine-Grained Permissions: Fine-grained policies help ensure that only the necessary permissions are granted to users or services. This reduces the attack surface and allows your architecture to scale securely.
- Regional Considerations: AWS STS has regional endpoints that allow you to handle requests in different AWS regions. Ensure that your infrastructure takes advantage of regional endpoints to reduce latency and enhance performance.
2. Migration Strategies
As your architecture evolves, there will be times when you need to migrate from one identity management system to another, or move to new AWS regions. Here are a few strategies to ensure that your STS implementation supports such migrations:
- Gradual Migration: Migrate in stages to ensure minimal disruption. For example, you can begin by transitioning some IAM roles or users to use temporary STS credentials before migrating all resources to a new region or security model.
- Hybrid Cloud: During migrations to the cloud, STS can facilitate hybrid cloud setups. For instance, in a hybrid cloud environment, STS can be used to bridge the gap between on-premises identity systems and AWS services.
- Use of CloudTrail for Monitoring: During migrations, use AWS CloudTrail to monitor API requests and track any issues that arise from the change in your identity management process.