Data security is one of the most critical responsibilities in any cloud strategy. From financial services to healthcare to SaaS platforms, organizations handle sensitive data that must be protected against unauthorized access, tampering, and regulatory violations. Encryption is essential, but without effective key management, even the strongest encryption becomes a liability.
Manual processes are error-prone, inconsistent, and difficult to audit. AWS Key Management Service (KMS) addresses this challenge by offering a centralized, fully managed solution for creating, using, and controlling encryption keys across your AWS environment.
This blog provides a detailed overview of AWS KMS, covering its architecture, key concepts, real-world use cases, and practical guidance to help you implement encryption strategies that are both secure and scalable.
What is AWS KMS?
Source - AWS
AWS Key Management Service (KMS) is a secure and fully managed solution for creating and controlling encryption keys used to protect your data. It acts as a central point from which you can manage all your cryptographic keys — from creation and storage to usage and deletion within your AWS environment.
Instead of handling encryption keys manually or across scattered systems, AWS KMS allows you to manage them centrally, consistently, and securely. It integrates tightly with AWS services, so your encryption policies and access controls can be enforced without additional tools or infrastructure. The service is designed to scale with your environment and maintain high levels of availability, security, and compliance.
Proper encryption key management is not just a security best practice; it’s essential. Mismanaged keys can result in lost data, accidental exposure, or compliance violations. AWS KMS helps eliminate these risks by offering strong protections, full visibility into key usage, and tools that simplify ongoing key operations.
Why Choose AWS KMS Over Other Solutions?
Many organizations underestimate the complexity of encryption key management until it becomes a problem. AWS KMS offers an effective solution for organizations that need to protect sensitive information, meet compliance requirements, and reduce operational burdens. Here’s how it stands out from traditional approaches or self-managed key systems:
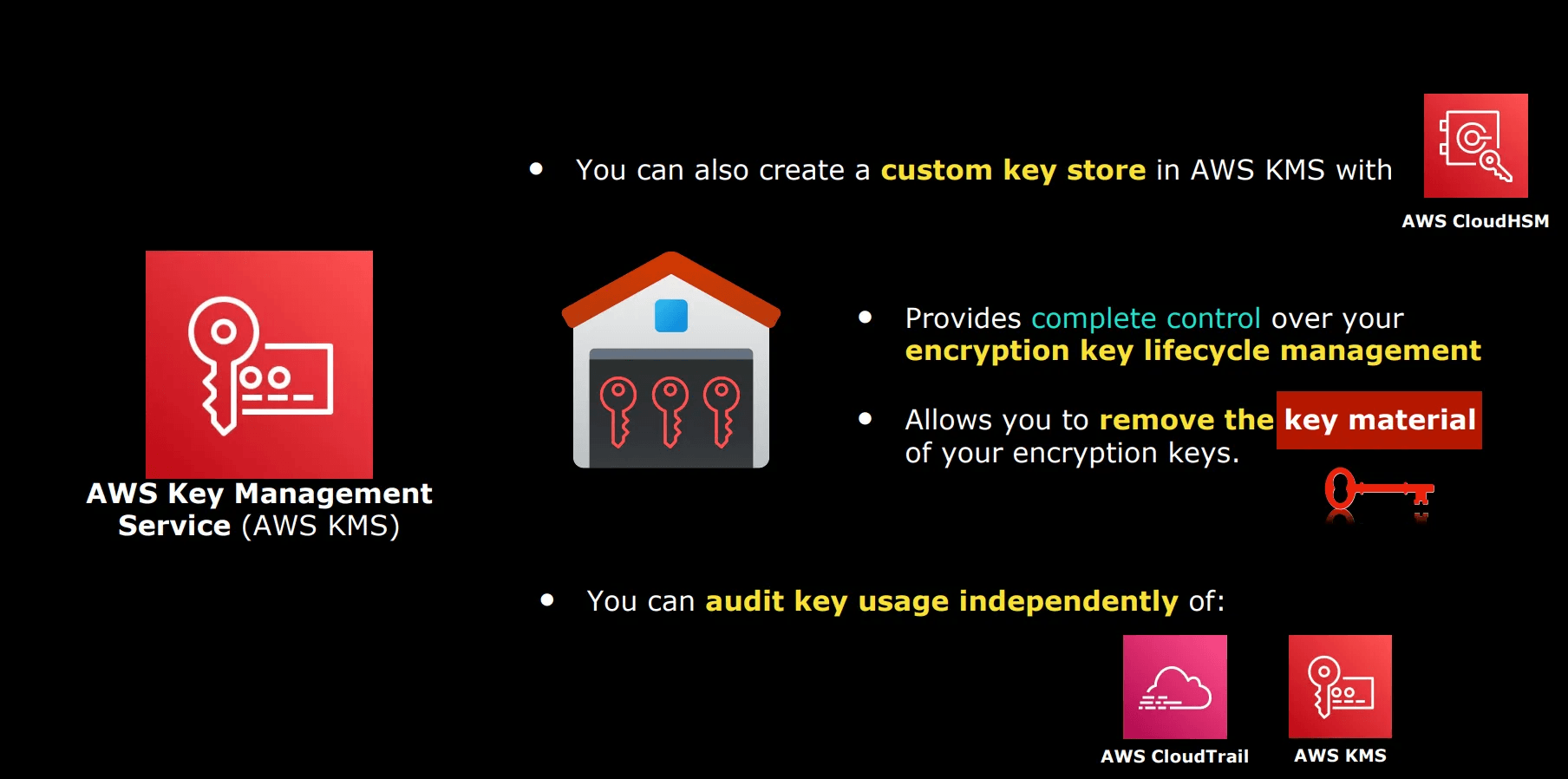
- Built-in Hardware-Level Security
All keys in AWS KMS are stored and used within hardware security modules (HSMs). These are dedicated physical devices designed to keep keys safe from tampering or unauthorized access. AWS’s HSMs meet strict government and industry standards (such as FIPS 140-2 Level 2), giving you high assurance that your keys are protected, even from internal threats.
- Deep Integration with AWS Services
AWS KMS works natively with many AWS services. For example:
- Amazon S3 uses KMS to encrypt stored files.
- Amazon EBS applies KMS-managed encryption to volumes without performance loss.
- Amazon RDS and DynamoDB support encryption of entire databases with a single configuration.
These services can automatically use your encryption keys stored in KMS, so you don’t need to build or maintain separate encryption mechanisms.
- Simplified, Centralized Key Management
Managing encryption keys across different applications and environments often leads to inconsistency and security gaps. AWS KMS offers:
- A single place to manage all keys across accounts and workloads
- Automatic key rotation, reducing the risk of key compromise
- Easy lifecycle control, including creating, disabling, deleting, and recovering keys
This simplifies operations for both security teams and developers, especially as your environment scales.
- Transparent and Auditable Key Usage
All actions involving your encryption keys, whether it's someone creating, using, or deleting a key, are logged automatically through AWS CloudTrail. These detailed logs help you:
- See exactly who accessed which key, when, and from where
- Monitor usage patterns for anomalies
- Demonstrate compliance with standards like GDPR, HIPAA, and PCI DSS
You can also connect these logs to alerting systems to detect suspicious activity in real time.
The Fundamental Concepts of AWS KMS
To effectively use AWS KMS, it is essential to understand some core components and how they work together.
Customer Master Keys (CMKs)
The Customer Master Key, or CMK, is the central element in AWS KMS. It is a logical key that you create and control, which is used to protect other keys that encrypt your actual data.
There are two types of CMKs:
- Customer-managed CMKs: You have full control over these keys. You create them, set permissions, and manage their lifecycle, including rotation and deletion.
- AWS-managed CMKs: These are created and managed by AWS on your behalf. They are used automatically by AWS services, and you do not have direct access to control them.
Data Keys
Source - AWS
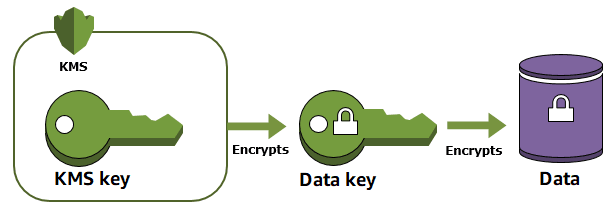
Instead of using CMKs to encrypt large amounts of data directly—which can be slow and inefficient, AWS KMS uses a two-step process:
- AWS KMS generates data keys.
- These data keys are used to encrypt your actual data.
- The data keys themselves are encrypted (or "wrapped") by the CMK and stored securely.
This method improves performance because the data keys can be used locally for fast encryption and decryption, while the CMK remains the trusted root key that protects the data keys.
Key Policies and IAM Policies
Managing who can use or administer keys is critical in AWS KMS.
- Key policies are permissions attached directly to CMKs that specify which users or services can manage or use the key.
- IAM policies from AWS Identity and Access Management work together with key policies to control access tightly. This ensures that only authorized users and applications can perform encryption or decryption operations.
Encryption Context
AWS KMS supports an optional feature called encryption context—a set of additional key-value pairs included during encryption and decryption.
This context adds extra metadata that must match during decryption, helping prevent misuse or unauthorized decryption by adding a layer of security.
How Does AWS KMS Work? The Encryption Workflow
Understanding the step-by-step process of how AWS KMS handles encryption helps clarify its strengths:
- Create a CMK: Begin by creating a Customer Master Key through the AWS Management Console, CLI, or SDK.
- Generate Data Keys: Use the CMK to generate a data key. AWS KMS returns this key in two forms: a plaintext version for immediate use and an encrypted version for safe storage.
- Encrypt Data: Use the plaintext data key to encrypt your data locally, which is faster and reduces reliance on network calls.
- Store Data: Save the encrypted data together with the encrypted data key.
- Decrypt Data: When you need to access the data, AWS KMS decrypts the encrypted data key back into plaintext. Then, you use this key to decrypt the data.
- Audit and Monitor: All key usage is logged automatically, providing full visibility for security monitoring and compliance.
Common Misconceptions About AWS KMS
Despite its capabilities, AWS KMS is sometimes misunderstood. Here are a few common misconceptions:
- “It’s too complex for small businesses.”
AWS KMS provides a simple setup process and can be implemented with basic IAM and S3 configurations. It’s suitable for startups and enterprises alike. - “Using KMS will degrade performance.”
Encryption and decryption are performed using locally cached data keys, minimizing performance impact. CMKs are not used for bulk data operations. - “AWS has full access to my keys.”
With customer-managed CMKs, access is controlled entirely by your defined policies. You can also use key policies and grants to strictly limit access.
Clarifying these points helps reduce hesitation and supports more informed adoption.
Getting Started with AWS KMS
For those new to AWS KMS, getting started is straightforward:
- Access the AWS Management Console: Navigate to the Key Management Service section.
- Create a Customer Master Key (CMK): Choose whether to use a symmetric or asymmetric key, define key usage permissions, and apply key policies.
- Enable Key Rotation (Optional): Set up automatic annual key rotation for enhanced security.
- Use the CMK with AWS Services: Integrate with services such as S3, EBS, RDS, or call the API directly to generate and encrypt data keys.
- Monitor Key Activity: Enable CloudTrail to log all key usage and operations.
This process can be completed with minimal setup, making it accessible even to organizations without deep security teams.
Planning Your Implementation
- Assess Your Data Classification: Identify which data requires encryption and determine appropriate key separation strategies. Different data types may require separate CMKs for optimal security and compliance.
- Design Your Key Architecture: Plan how many CMKs you need, their intended purposes, and access patterns. Consider factors like regulatory requirements, data sensitivity, and operational needs.
- Establish Governance Procedures: Define processes for key creation, rotation, access reviews, and incident response. Clear procedures prevent security gaps and support compliance efforts.
- Test Before Production: Implement KMS in development environments first to understand performance implications and operational procedures. Thorough testing prevents issues during production deployment.
Advanced Cross-Account Key Management
In multi-account AWS environments, managing encryption keys securely and efficiently is essential. AWS KMS enables centralized control by allowing keys to be shared across accounts without compromising isolation.
There are three common access patterns organizations use:
- Centralized Management: Creating CMKs in a dedicated security account and granting access to others simplifies policy enforcement and key management.
- Federated Access: AWS Organizations can automatically manage key permissions based on organizational units or tags, reducing manual overhead.
- Service-Specific Sharing: Keys are shared selectively for particular services like S3 replication or RDS snapshots, following the principle of least privilege.
When setting this up, key policies must explicitly allow access to external accounts, and those accounts need appropriate IAM permissions. All cross-account key usage is logged in CloudTrail, providing full auditability. It’s also important to consider that cross-region key operations may add slight latency.
A well-structured cross-account key policy typically includes root access for the owning account, permissions for specific AWS services, and carefully scoped access for external accounts often with conditions based on encryption context or resource tags.
This strategy ensures your encryption keys remain secure, manageable, and compliant across multiple AWS accounts.
Performance Optimization Strategies
Improving AWS KMS performance is essential to maintaining fast and efficient encryption operations. One common technique is caching data keys locally within your application. This reduces frequent calls to AWS KMS, which can save time and lower costs. However, it’s important to size your cache appropriately and ensure it is refreshed when keys are rotated or disabled to avoid security risks.
How your application interacts with KMS also affects performance. Grouping multiple encryption requests together or processing them asynchronously can minimize latency and prevent bottlenecks in user-facing processes. Additionally, placing KMS keys in the same AWS region as your data helps reduce network delays.
Be mindful of AWS KMS request limits. Monitor your API usage patterns, and when necessary, request quota increases or distribute workloads across multiple keys. Whenever possible, leverage built-in encryption features in AWS services like S3 and EBS, as these are optimized and don’t count against KMS quotas.
Key points to remember:
- Use local caching of data keys to reduce API calls
- Batch requests or use asynchronous processing to improve throughput
- Place keys regionally close to your applications and data
- Monitor quotas and distribute workloads to avoid throttling
Third-Party Service Integration
AWS KMS extends beyond native AWS services to support various third-party applications and hybrid cloud scenarios.
Database and Application Integration
- MongoDB Atlas: Configure MongoDB Atlas to use AWS KMS for encryption key management, enabling centralized key policies for cloud database deployments.
- Kubernetes Secrets: Use the AWS KMS provider for Kubernetes to encrypt secrets at rest, integrating container orchestration with AWS key management.
- HashiCorp Vault: Configure Vault to use AWS KMS as an auto-unseal mechanism, eliminating manual intervention during Vault startup procedures.
Hybrid Cloud Scenarios
- On-Premises Integration: Use AWS KMS APIs from on-premises applications through VPN or Direct Connect connections. This enables consistent encryption policies across hybrid environments.
- Multi-Cloud Key Management: While KMS keys remain in AWS, applications in other clouds can use AWS APIs to encrypt data before storage, maintaining centralized key governance.
- Edge Computing: AWS IoT Greengrass can use KMS-derived keys for local encryption at edge locations while maintaining central key management.
API Integration Patterns
- SDK Integration: Most programming languages offer AWS SDKs with KMS support. Use these SDKs to integrate encryption into custom applications with minimal development overhead.
- REST API Access: For applications that cannot use AWS SDKs, direct REST API integration provides full KMS functionality through standard HTTP requests.
- Proxy Patterns: Implement KMS proxy services for applications that require simplified encryption interfaces or need to abstract AWS-specific implementations.
Security Considerations for Third-Party Integration
When integrating third-party services with AWS KMS:
- Use IAM roles with temporary credentials instead of long-term access keys
- Implement encryption context to add additional security layers
- Monitor all third-party key usage through CloudTrail logs
- Regular audit third-party service permissions and access patterns
- Consider network security for API communications, especially from external environments
Real-World Applications of AWS KMS
AWS KMS supports a wide range of use cases, demonstrated through both functional categories and industry-specific implementations:
- Cloud Storage Encryption
Encrypt data stored in Amazon S3 using SSE-KMS for server-side encryption. This ensures confidentiality and supports granular access control through key policies and IAM.
- Volume and Database Encryption
AWS services such as Amazon EBS, RDS, and DynamoDB offer native encryption at rest using KMS. This enhances data protection without altering application logic.
- Application-Level Encryption
Use AWS SDKs to generate and manage data keys for encrypting payloads before storage or transmission, ensuring protection across the entire data lifecycle.
- Digital Signing and Verification
AWS KMS supports digital signatures to verify data integrity and authenticate software or user identity.
- Compliance Enforcement
Meet regulatory requirements (e.g., HIPAA, PCI DSS, GDPR) by managing encryption keys with traceable access controls and audit trails.
Real-Life Examples: How Teams Use AWS KMS?
Understanding how AWS KMS works is one thing; seeing it in action makes it real. Here are some practical ways different teams use KMS every day:
- Retail: Protecting Card Data in S3 with Least Privilege
A retail company collects and stores card details during checkout. They need to keep this data encrypted in Amazon S3 and prove they’re protecting it under PCI DSS.
How they use KMS:
- The checkout system uploads encrypted card data to S3 using SSE-KMS.
- A customer-managed CMK is used for this data only — no other app shares the key.
- IAM and key policies ensure that only the payment service can decrypt the data.
- CloudTrail logs every decryption request and flags any unexpected access.
This setup lets the company isolate access at the service level, enforce encryption without changing application logic, and show detailed audit logs to pass PCI audits.
- Healthcare: Encrypting Patient Records in RDS for HIPAA
A healthcare startup needs to secure patient records in Amazon RDS and prove that only authorized systems can access them, critical for HIPAA compliance.
How they use KMS:
- RDS is encrypted at rest using a customer-managed CMK.
- Only the backend API used by authenticated clinicians has decrypt permissions.
- Logs show every time a record is accessed and by which service role.
- Key rotation is enabled automatically to reduce key compromise risk.
Instead of building access controls from scratch, the team uses KMS to enforce strict service-level access and prove data security to regulators.
- SaaS: Isolating Each Customer’s Data with Their Own Key
A SaaS company handles sensitive financial data across multiple clients. Their customers demand clear proof that their data is kept separate.
How they use KMS:
- A unique CMK is created for each customer at signup.
- Their data is encrypted using data keys derived from that customer’s CMK.
- When a customer is offboarded, their CMK is disabled or deleted.
- The team uses key-level access logs to detect any cross-tenant issues.
KMS gives them a straightforward way to enforce tenant isolation, instantly revoke access per customer, and prove that encryption boundaries are in place.
Common Mistakes to Avoid with AWS KMS
While AWS KMS is built to simplify encryption, it doesn’t secure your data by default. Missteps in setup or policy design can quietly weaken your defenses. These are some of the more frequent mistakes and how to handle them more effectively.
Overly Broad Access
It’s common to grant wide permissions to get things working quickly, especially in shared environments. But giving full kms:* or kms:Decrypt to multiple roles or people increases the chance of misuse or worse, compromise.
To keep control tight:
- Assign only the specific permissions needed for each role.
- Use key policies in combination with IAM roles, not in isolation.
- Restrict decryption rights to the smallest possible group, ideally, just the services that handle sensitive data.
Ignoring Key Rotation
Encryption keys don’t stay secure forever. Using the same key for years might feel stable, but it increases exposure if credentials are leaked or misused.
Make rotation a routine part of your setup:
- Enable automatic annual rotation for customer-managed keys.
- Plan key replacement cycles for highly sensitive workloads, especially in regulated environments.
- Document key rotation events so data owners know what was protected with which version.
One Key, Too Many Jobs
Relying on a single key across applications or environments simplifies initial setup, but blurs the separation of access. It also makes it harder to audit, manage, or revoke access without breaking things unintentionally.
A better approach:
- Create distinct keys for different environments (dev, staging, production) and sensitive domains (e.g., customer data vs. logs).
- Use tagging and naming conventions to keep key ownership and purpose transparent.
- Segment access by team, system, or customer if you're supporting multi-tenant workloads.
Not Watching How Keys Are Used
Encrypting your data is one part of the equation. If you’re not tracking who uses your keys and you may miss early signs of a breach or internal misuse.
Build observability into your KMS use:
- Enable CloudTrail logging for every key.
- Set up alerts for unusual activity, such as access from unexpected regions or excessive decrypt operations.
- Review key usage logs regularly during security assessments or audits.
What If a Key Is Compromised?
If someone gets access to a key they shouldn’t, quick action is critical. Here's a simple plan for handling it:
Step 1: Disable the Key
- Go to the AWS Console → KMS
- Find the key and click Disable
- This stops all use of the key immediately no more encryption or decryption
Step 2: Check the Logs
- Use AWS CloudTrail to see who accessed the key
- Look for suspicious users, IPs, or regions
Step 3: Re-encrypt Your Data
- Create a new CMK
- Use it to generate new data keys
- Re-encrypt the affected data with the new keys
- Store new encrypted data keys alongside the data
Step 4: Update Permissions
- Review IAM and key policies to make sure the wrong person doesn’t still have access
- Remove any overly broad permissions (like wildcard * access)
Step 5: Document the Incident
- Record what happened and how you fixed it
- This is important for audits and team learning
Reacting quickly, staying calm, and using the tools AWS gives you will help you recover smoothly without losing data or trust.
AWS KMS vs Other Encryption Approaches
Not every encryption need is the same and AWS KMS isn’t the only tool out there. But what makes KMS worth choosing is how well it balances control, ease of use, and integration, especially for AWS-based workloads.
Here’s how it stacks up against alternatives in real-world scenarios:
| Aspect | AWS KMS | Client-Side Encryption | HSM (Hardware Security Module) |
| Where Encryption Happens | Server-side, within a managed environment | On the client or application layer, before data is sent or stored | Varies — can be client-side or integrated into secure modules |
| Who Controls the Keys | You define key usage policies, AWS manages secure storage | You control everything: key creation, storage, and use | You control everything, often via specialized tools or APIs |
| Trust Boundary | Shared: You trust AWS to secure keys physically and cryptographically | No third-party trust — encryption and keys remain entirely under your control | No third-party trust — HSMs are isolated, sometimes even air-gapped |
| Key Exposure Risk | Low — KMS doesn’t expose keys directly; access is tightly controlled | Moderate — risk depends on your implementation and storage decisions | Very low — private keys never leave the HSM hardware |
| Ease of Implementation | High — minimal custom development required | Medium to low — requires building secure flows for key handling | Low — needs specialized skills and infrastructure |
| Performance Overhead | Low — optimized for scale; keys are used to generate local data keys | Can be high, especially at scale or if keys aren't cached efficiently | Depends — hardware acceleration may help, but integration adds latency |
| Audit and Monitoring | Built-in logging; full visibility into access and usage | Must be implemented manually | Often includes internal logging, but external audit needs extra work |
| Best Fit For | Teams needing centralized, reliable encryption with some flexibility | Scenarios demanding total data control or end-to-end encryption | Regulated environments (e.g. finance, defense) needing physical trust anchors |
Conclusion
AWS KMS is more than just a key vault; it’s a foundational security service that enables you to protect your data effortlessly and compliantly. Its integration with AWS services, hardware-backed security, and centralized control make it an essential part of any cloud security strategy.
Whether you’re securing simple backups or powering complex encryption architectures for sensitive applications, AWS KMS offers the tools and peace of mind you need.