Managing cloud infrastructure manually can quickly become complex, error-prone, and difficult to maintain, especially as your environment grows. AWS CloudFormation simplifies this by allowing you to define your entire cloud environment as code. Instead of clicking around in the console, you create a template that serves as a blueprint for your infrastructure, and CloudFormation takes care of building and managing it for you.
What Is CloudFormation?
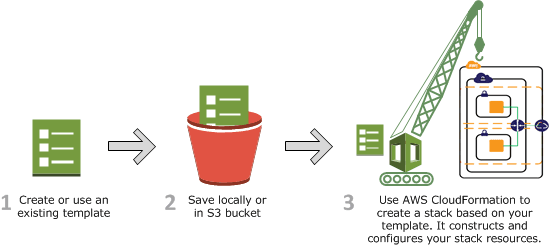
Source - AWS
CloudFormation is AWS’s native Infrastructure as Code (IaC) service that uses declarative templates written in YAML or JSON. These templates act as the single source of truth, describing everything from compute instances and storage to networking and security settings. This approach allows you to provision, update, and manage your infrastructure consistently and reliably.
Why Infrastructure as Code Matters?
Manual deployment often leads to problems that can be hard to spot until it’s too late. Configurations might drift apart between environments, human errors can introduce subtle bugs, and keeping track of changes is a challenge without proper documentation. Scaling up means repeating tedious tasks, which increases the risk of mistakes and delays.
By adopting infrastructure as code, you capture your setup in a template that serves as a one reliable source of information. This means you can deploy consistent environments quickly, minimize manual errors, and easily track any changes over time. Your infrastructure becomes as manageable as application code—testable, version-controlled, and reusable.
What Makes It Different?
This AWS infrastructure-as-code service stands out in the landscape due to its deep integration with the AWS ecosystem and its reliable, predictable approach to managing cloud resources. Understanding these unique characteristics helps clarify why it is often the preferred choice for AWS infrastructure automation.
- Native AWS Integration
Developed and maintained by AWS, it has immediate and full access to the latest AWS services and features. This tight integration means nearly every AWS resource can be provisioned directly from templates, often as soon as new services become generally available.
- Clear and Predictable Execution
Instead of specifying how to create resources, you declare what you want. The service then orchestrates creation, update, and deletion predictably, ensuring infrastructure always connects to the desired state.
- Built-in Dependency Management
Dependencies between resources are automatically understood and managed. Operations are sequenced correctly—creating or deleting resources in the right order—eliminating the need for manual scripting even in complex deployments.
- Stack Management and Rollbacks
Related resources are grouped into stacks, simplifying management, updates, or deletions of entire applications or environments as single units. Failed updates trigger automatic rollbacks to the last stable state, minimizing the risk of incomplete or broken infrastructure.
- Integration with AWS Ecosystem Tools
Seamless compatibility with AWS Identity and Access Management (IAM), CloudTrail, Config, and monitoring services enables secure, auditable, and compliant automation workflows.
CloudFormation Core Concepts
Let's break down the basic building blocks of CloudFormation:
Templates
A template is the blueprint of your infrastructure written in YAML or JSON. It defines all the AWS resources you want to create and how they should be configured. Templates are just text files that you can edit in any code editor, store in version control, and share with team members.
CloudFormation templates have several sections, but the most important is the Resources section, which defines the AWS components you want to create.
YAML Example (preferred for readability):
| yaml Resources: S3Bucket: Type: AWS::S3::Bucket Properties: BucketName: my-unique-bucket-name VersioningConfiguration: Status: Enabled |
The same template can be written in JSON, but YAML is generally preferred for its readability:
JSON Alternative:
| json { "Resources": { "S3Bucket": { "Type": "AWS::S3::Bucket", "Properties": { "BucketName": "my-unique-bucket-name", "VersioningConfiguration": { "Status": "Enabled" } } } } } |
In both examples:
- S3Bucket is a logical ID (a name you choose) that identifies this resource within the template
- Type: AWS::S3::Bucket tells CloudFormation what kind of resource to create (in this case, an S3 storage bucket)
- Properties defines the specific configuration for this bucket, including its name and that versioning should be enabled
Stacks
When you deploy a template, CloudFormation creates a stack. A stack is a collection of AWS resources that you manage as a single unit. You can create, update, or delete an entire stack, affecting all its resources.
A typical organization might have several stacks for different components of their infrastructure:
- Network stack: VPC, subnets, route tables, internet gateways
- Security stack: IAM roles, security groups, KMS keys
- Data storage stack: RDS databases, DynamoDB tables, S3 buckets
- Compute stack: EC2 instances, Auto Scaling groups, Lambda functions
This modular approach makes management easier and allows different teams to own different parts of the infrastructure.
Resources
Resources are the individual AWS components that make up your stack. Each resource has:
- A type (like AWS::EC2::Instance or AWS::S3::Bucket)
- Properties that configure how the resource behaves
- A logical ID that identifies the resource within the template
- A physical ID that AWS assigns when the resource is created (like an actual EC2 instance ID)
CloudFormation supports over 800 resource types across AWS services. The five most commonly used are:
- AWS::EC2::Instance - Virtual servers in the cloud
- AWS::S3::Bucket - Object storage for files and data
- AWS::DynamoDB::Table - NoSQL database tables
- AWS::Lambda::Function - Serverless compute functions
- AWS::IAM::Role - Permission sets for AWS services and users
Each resource type has its own set of required and optional properties, which you can find in the AWS CloudFormation Resource Reference.
Conditional Resource Creation
In real-world infrastructure, you often need different resources for different environments. For example, you might want redundant servers in production but not in development to save costs. Conditions in CloudFormation let you include or exclude resources based on parameter values or other factors.
How Conditions Work?
Conditions are boolean expressions (true/false) that you define in a special Conditions section of your template. You can then apply these conditions to entire resources or to specific properties.
Here's a comprehensive example of conditional resource creation:
| yaml Parameters: CreateProdResources: Description: Create production-only resources Type: String Default: "false" AllowedValues: - "true" - "false" Conditions: IsProd: !Equals [!Ref CreateProdResources, "true"] Resources: PrimaryInstance: Type: AWS::EC2::Instance Properties: InstanceType: t3.micro ImageId: ami-0c55b159cbfafe1f0 # Other base instance configuration StandbyInstance: Type: AWS::EC2::Instance Condition: IsProd Properties: InstanceType: t3.micro ImageId: ami-0c55b159cbfafe1f0 # Standby instance for failover in production only BackupBucket: Type: AWS::S3::Bucket Condition: IsProd Properties: BucketName: !Sub "${AWS::StackName}-backups" VersioningConfiguration: Status: Enabled # Production-only backup storage |
Let's analyze this example:
- We define a parameter CreateProdResources that can be either "true" or "false".
- We create a condition called IsProd that uses the !Equals function to check if the parameter equals "true".
- In the Resources section:
- PrimaryInstance is created regardless of the condition (it has no Condition attribute)
- StandbyInstance and BackupBucket are only created when the IsProd condition is true
Real-World Applications of Conditions
Conditions are incredibly useful for creating templates that work across different environments. Here are some common scenarios:
- Environment-specific resources: Create high-availability configurations only in production
- Regional differences: Deploy certain resources only in specific AWS regions
- Optional features: Include additional components based on user requirements
- Cost optimization: Deploy lower-cost alternatives in non-production environments
More Complex Conditional Logic
CloudFormation provides several intrinsic functions for building complex conditions:
- !And - Returns true if all of the specified conditions are true
- !Or - Returns true if any of the specified conditions are true
- !Not - Negates a condition
- !If - Returns one value if the condition is true and another if it's false
For example, you might want to create a standby instance only if it's production AND the region is us-east-1:
| yaml Conditions: IsProd: !Equals [!Ref EnvironmentType, "prod"] IsUsEast1: !Equals [!Ref "AWS::Region", "us-east-1"] IsProdInUsEast1: !And [!Ref IsProd, !Ref IsUsEast1] Resources: StandbyInstance: Type: AWS::EC2::Instance Condition: IsProdInUsEast1 Properties: # Properties here... |
Conditions provide the flexibility
Making Your Templates Smart and Environment-Aware
AWS CloudFormation enables you to use a single template to deploy infrastructure tailored for different environments, such as development, testing, and production, by using a combination of parameters, mappings, and conditions.
- Parameters allow you to pass values into your template at deployment time, like specifying which environment you’re deploying to or choosing an instance type. This makes templates reusable without editing the template itself.
- Mappings act as lookup tables inside your template, holding predefined values for each environment or region. This ensures consistency by avoiding manual input of every configuration detail and reduces the risk of errors.
- Conditions let you define logic within your template, such as deploying certain resources only in production or adjusting resource properties based on the environment.
Together, these features allow you to maintain one template that adjusts its behavior and resource configuration according to the deployment context.
For example, You might define a parameter called EnvironmentType with allowed values dev, test, and prod. Your template then references this parameter to choose appropriate resource sizes and enable features like backups only in production. Mappings could hold details like backup retention periods or availability zone settings for each environment. Conditions then decide which resources to create or configure based on these inputs.
By managing environment-specific settings this way, you avoid duplicating templates, reduce errors, and maintain clarity.
Writing CloudFormation Templates
When authoring CloudFormation templates, you have two format choices: YAML and JSON. Both are fully supported, but YAML tends to be more human-friendly due to its cleaner syntax and support for comments, making templates easier to read and maintain. JSON, on the other hand, is more verbose and strict, which can be useful if you generate templates programmatically or use certain tooling.
Most users today prefer YAML for its readability, but you should choose the format that best fits your workflow.
Anatomy of a CloudFormation Template
A CloudFormation template has several sections, but only Resources is actually required:
| yaml AWSTemplateFormatVersion: 'xxxx-xx-xx' Description: 'A simple template example' Parameters: # Input values you specify when creating the stack Mappings: # Key-value pairs for lookup tables Conditions: # Conditions controlling resource creation Resources: # The AWS resources to create (the only required section) Outputs: # Values returned after stack creation |
Let's look at a simple template that creates a single S3 bucket:
| yaml AWSTemplateFormatVersion: 'xxxx-xx-xx' Description: 'Template for an S3 bucket with versioning enabled' Resources: MyS3Bucket: Type: AWS::S3::Bucket Properties: VersioningConfiguration: Status: Enabled Outputs: BucketName: Description: Name of the S3 bucket Value: !Ref MyS3Bucket |
Organizing Complex Templates
Breaking Down Big Templates with Nested Stacks
As your infrastructure grows, your templates can become unmanageable. Nested stacks let you break them into manageable pieces:
| yaml Resources: NetworkStack: Type: AWS::CloudFormation::Stack Properties: TemplateURL: https://s3.amazonaws.com/bucket-name/network.yaml Parameters: VpcCIDR: 10.0.0.0/16 DatabaseStack: Type: AWS::CloudFormation::Stack Properties: TemplateURL: https://s3.amazonaws.com/bucket-name/database.yaml Parameters: VpcId: !GetAtt NetworkStack.Outputs.VpcId |
This approach lets you:
- Reuse common components across different projects
- Keep individual templates focused and simple
- Work around the CloudFormation template size limit
- Update parts of your infrastructure without touching the rest
Handling Different Environments Elegantly
One of the trickiest parts of infrastructure management is maintaining similar but slightly different environments for development, testing, and production. CloudFormation helps with this:
Use parameters to customize behavior by environment:
| yaml Parameters: Environment: Type: String Default: dev AllowedValues: [dev, test, prod] Resources: MyInstance: Type: AWS::EC2::Instance Properties: InstanceType: !If [IsProd, m5.large, t3.small] Conditions: IsProd: !Equals [!Ref Environment, prod] |
Create parameter files for each environment:
| json // dev-params.json { "Parameters": { "Environment": "dev", "InstanceType": "t3.micro", "BackupEnabled": "false" } } // prod-params.json { "Parameters": { "Environment": "prod", "InstanceType": "m5.large", "BackupEnabled": "true" } } |
Then deploy with:
| bash aws cloudformation create-stack --stack-name my-app-dev --template-body file://template.yaml --parameters file://dev-params.json |
Managing Infrastructure Changes Safely in CloudFormation
As your AWS infrastructure grows, managing changes safely becomes critical—not just to avoid downtime, but to ensure consistency, security, and long-term maintainability. AWS CloudFormation offers several tools that help you make informed, controlled updates.
Preview with Change Sets
Before applying changes to a CloudFormation stack, use Change Sets to preview exactly what will happen. This feature shows which resources will be created, modified, or deleted, allowing you to catch unintended impacts before they occur. It’s particularly valuable for production stacks, where an unexpected resource replacement could mean data loss or service disruption.
Deploy Across Accounts with StackSets
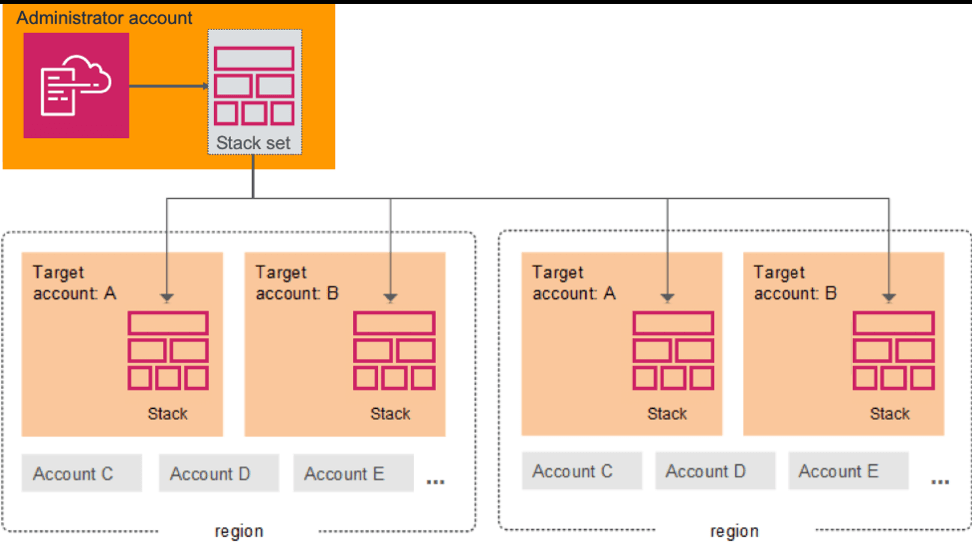
Source - AWS
StackSets allow you to deploy the same CloudFormation template across multiple AWS accounts and regions in a single operation. This is ideal for enterprises that need standardized infrastructure, such as IAM roles, logging configurations, or networking setups, rolled out uniformly across environments.
Detect Configuration Drift
Over time, manual changes made outside of CloudFormation—such as edits in the AWS Console—can create discrepancies between your live infrastructure and your defined templates. Drift Detection identifies these inconsistencies, helping teams bring the environment back into alignment with version-controlled definitions.
Validation: First Line of Defense
Always validate your templates before deployment. This basic but essential step helps catch syntax errors, invalid parameters, or unsupported resource configurations early—long before they become operational issues.
Automating CloudFormation Deployments
To fully unlock the power of infrastructure as code, integrate your CloudFormation templates into a CI/CD pipeline. This brings consistency, repeatability, and safety to your deployments.
Integrating with CI/CD Pipelines
CloudFormation excels when integrated into CI/CD pipelines. Here's a conceptual example using AWS CodePipeline:
- Source: Pull the latest CloudFormation templates from a version-controlled Git repository
- Validate: Use cfn-lint or aws cloudformation validate-template to catch syntax and structural issues early
- Test Deploy: Launch the stack in a sandbox or staging environment
- Approval: Require manual approval before promoting to production (optional but recommended)
- Deploy: Push the tested stack to production
This automation ensures your infrastructure changes go through proper testing and approval before affecting production environments.
Avoiding Surprises: Validating and Testing Your CloudFormation Templates
Before deploying your CloudFormation templates, it’s crucial to catch errors early to prevent costly outages and reduce debugging time. Validation should be an integral part of your development process.
Two popular tools help you do this:
- cfn-lint: Checks your template for syntax errors and adherence to best practices. Running this locally or in your CI pipeline helps catch simple mistakes early.
- cfn-nag: Focuses on security, scanning your templates for risky configurations or policy violations.
By integrating these validation steps into your continuous integration (CI) pipelines, you ensure that every change is automatically checked, making deployments safer and more predictable.
Taking this proactive approach to testing your templates helps you avoid surprises and builds confidence in your infrastructure automation.
Real-World Use Cases of CloudFormation
Understanding how AWS CloudFormation is applied in real-world scenarios helps highlight its value beyond theory. Here are some common use cases that demonstrate why organizations rely on CloudFormation for infrastructure management:
- Auto-Scaling a Web Application
Many businesses deploy web applications that experience variable traffic. CloudFormation templates can provision auto-scaling groups, load balancers, and related networking resources in a repeatable way. By defining scaling policies and alarms within the template, the infrastructure dynamically adjusts capacity based on demand, improving availability and cost efficiency.
- Multi-Availability Zone (Multi-AZ) Database Deployments
For high availability and disaster recovery, CloudFormation can create databases like Amazon RDS instances distributed across multiple Availability Zones. Templates specify configurations such as backup retention, failover policies, and encryption. This ensures consistent and reliable deployment of robust database environments with minimal manual intervention.
- Infrastructure as Code for Microservices Architectures
Organizations adopting microservices use CloudFormation to provision independent stacks for each service. This modular approach simplifies updates and rollbacks, enables environment isolation (dev/test/prod), and helps maintain clean separation of concerns. Combined with CI/CD pipelines, CloudFormation supports automated, repeatable deployments that align with modern software development practices.
- Secure Networking and Compliance
CloudFormation allows teams to define complex networking configurations—VPCs, subnets, security groups, and network ACLs—in a codified way. By embedding security best practices directly into templates, companies ensure compliance and reduce the risk of misconfigurations that could lead to vulnerabilities.
- Multi-Region Deployments
For global applications, CloudFormation templates can be deployed in multiple AWS regions with regional-specific parameters and mappings. This enables consistent infrastructure standards worldwide, improves latency by serving users closer to their location, and enhances disaster recovery options.
Your First CloudFormation Stack: A Hands-On Example
Now that you’ve seen how templates work, how changes are managed, and how to structure your infrastructure as code, let’s bring it all together with a complete but approachable example.
This sample stack provisions:
- An EC2 instance running a basic web server
- An S3 bucket with versioning enabled
- A security group that allows HTTP and SSH access
- Output values for easy reference
The Template
Save the following YAML as web-app.yaml. It uses parameters, structured resources, and meaningful outputs to demonstrate clean infrastructure-as-code design.
| AWSTemplateFormatVersion: 'xxxx-xx-xx' Description: Basic web server with storage Parameters: InstanceType: Description: EC2 instance type Type: String Default: t3.micro BucketName: Description: Unique name for the S3 bucket Type: String Resources: WebSecurityGroup: Type: AWS::EC2::SecurityGroup Properties: GroupDescription: Allow HTTP and SSH SecurityGroupIngress: - IpProtocol: tcp FromPort: 80 ToPort: 80 CidrIp: 0.0.0.0/0 - IpProtocol: tcp FromPort: 22 ToPort: 22 CidrIp: 0.0.0.0/0 WebServer: Type: AWS::EC2::Instance Properties: InstanceType: !Ref InstanceType ImageId: ami-0c55b159cbfafe1f0 # Replace with a valid Amazon Linux 2 AMI ID for your region SecurityGroups: - !Ref WebSecurityGroup UserData: Fn::Base64: !Sub | #!/bin/bash yum update -y yum install -y httpd systemctl start httpd systemctl enable httpd echo "<html><h1>Deployed with CloudFormation</h1></html>" > /var/www/html/index.html Tags: - Key: Name Value: WebServer ContentBucket: Type: AWS::S3::Bucket Properties: BucketName: !Ref BucketName VersioningConfiguration: Status: Enabled Outputs: SiteURL: Description: Public DNS of the web server Value: !Join ['', ['http://', !GetAtt WebServer.PublicDnsName]] CreatedBucket: Description: Name of the S3 bucket Value: !Ref ContentBucket |
Deploying the Stack
This template can be launched through either the AWS Console or the CLI, depending on your workflow.
Using the AWS Console
- Open the CloudFormation service
- Choose Create stack > With new resources (standard)
- Upload your web-app.yaml file
- Provide values for the parameters
- Review and create the stack
Using the AWS CLI
| bash aws cloudformation create-stack \ --stack-name web-app-stack \ --template-body file://web-app.yaml \ --parameters ParameterKey=BucketName,ParameterValue=my-unique-bucket |
To track progress:
| bash aws cloudformation describe-stacks --stack-name web-app-stack |
Key Takeaways
This example reinforces several core principles:
- Use of parameters to keep templates reusable
- Logical resource grouping and dependency handling
- Outputs for developer convenience
- Secure defaults and minimal hardcoding
This is your baseline. As you move forward, try incorporating additional layers like load balancers, databases, IAM roles, and VPCs. Each new piece builds on the structure you’ve just implemented.
Best Practices for Secure and Maintainable Templates
Handling Sensitive Information
Avoid embedding secrets directly in templates. Instead, reference secure services like Parameter Store for configuration values and Secrets Manager for sensitive credentials. This approach keeps your infrastructure safe and compliant without exposing secrets in your code.
Writing Secure IAM Policies
Follow the principle of least privilege by granting only the permissions necessary. Use IAM roles with narrowly scoped policies, and where appropriate, restrict access further using conditions such as IP address whitelisting or time-based access.
Designing Templates That Are Easy to Manage
- Group related resources logically to keep templates organized and understandable.
- Use clear, descriptive resource names to simplify navigation and maintenance.
- Comment on complex or non-obvious parts of your templates for clarity.
- Maintain consistent formatting for better readability and collaboration.
Limitations
While AWS CloudFormation is a powerful infrastructure-as-code tool, it’s important to understand its limitations to set realistic expectations and avoid common pitfalls.
- State Management Complexity
CloudFormation maintains the state of your infrastructure through stacks, but it can sometimes struggle with detecting drift—changes made outside of CloudFormation. Although drift detection exists, it’s not always comprehensive, and manual reconciliation may be needed to avoid unexpected resource mismatches.
- Update and Rollback Challenges
Updating stacks with complex or interdependent resources can occasionally lead to long deployment times or failures. Rollbacks, while designed to restore previous states, may sometimes leave stacks in a partial or inconsistent state, requiring manual intervention to fix.
- Limited Debugging Feedback
Error messages during stack creation or updates can be cryptic, making troubleshooting difficult for those new to CloudFormation. Detailed root causes may require inspecting CloudTrail logs or AWS console events, which adds overhead.
- Template Size and Complexity Constraints
There are limits on template size (up to 1 MB for direct uploads, higher with S3) and nested stack depth (up to 5 levels). Large or highly complex infrastructures may need careful modularization, which adds design overhead.
- Lag Between AWS Feature Releases and CloudFormation Support
New AWS features sometimes take time before CloudFormation supports them fully. This can delay infrastructure automation for cutting-edge services or require workarounds.
Being aware of these limitations helps you plan better, implement safeguards, and design templates that are maintainable and resilient.
Troubleshooting CloudFormation
When Things Go Wrong
CloudFormation deployments can fail for various reasons. Here's how to diagnose issues:
- Check the events tab - CloudFormation shows error messages here
- Look for the first failure - Subsequent failures are often consequences
- Common issues include:
- Missing permissions
- Resource already exists
- Invalid property values
- Service limits exceeded
For persistent problems, try creating the stack with rollback disabled to preserve the partial state for investigation:
| bash aws cloudformation create-stack \ --stack-name troubleshooting-stack \ --template-body file://template.yaml \ --disable-rollback |
Avoiding Common Pitfalls
- Test in a sandbox account before deploying to production
- Start small and gradually add complexity
- Use parameter constraints to prevent invalid input
- Handle resource deletion carefully - Some resources (like S3 buckets with content) won't be deleted by default
- Watch for circular dependencies - Resources that depend on each other
CloudFormation transforms how you manage AWS infrastructure, making it consistent, repeatable, and version-controlled. Start with simple templates and gradually build your skills. Before long, you'll deploy complex architectures confidently and spend less time on manual configuration.
Remember that the goal is to spend less time managing your infrastructure and more time building great applications.





